
引言
又是一年一度系列,杭州电子科技大学 Vidar Team 举办的 Hgame 来了!
主办方:杭电 Vidar-Team
赞助方:奇安信技术研究院
比赛时间:1/20 20:00 ~ 2/17 20:00
题目类型:Crypto 、Reverse、Misc、Pwn 、Web、IoT
比赛规则:解题模式,前三血分别有5%,3%,1%的额外加分
今年还是和往年一样,持续四周,这篇是第一周的 WriteUp,做的题目还是比较多的,不过相对而言比较简单,就随便水一水了。
后面几周的话,过年啥的了就摸了((
喵喵往年的 WriteUp:
CTF | Hgame2020 Week1 WriteUp.
CTF | 2021 Hgame Week1 WriteUp
CTF | 2021 Hgame Week2 WriteUp
IoT
饭卡的uno
Description
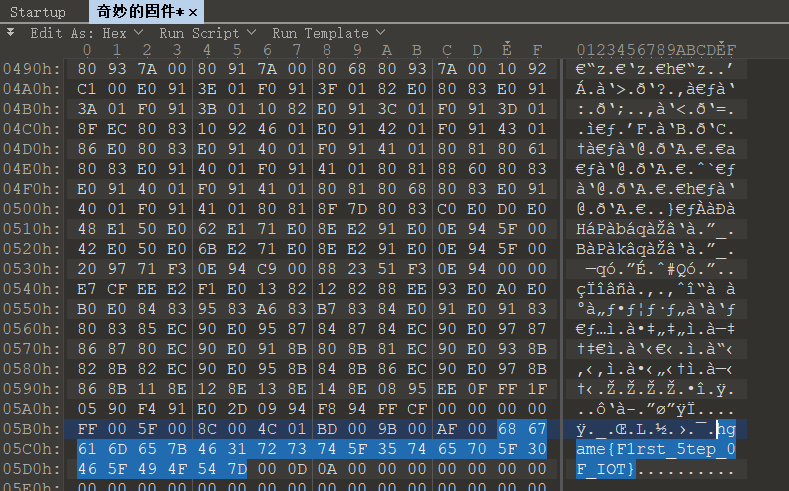
饭卡今天第一天学iot 然后他的好朋友Actue让他先去学uno 然后悄悄给饭卡塞了一个固件
Challenge Address
Web
easy_auth
Description
尊贵的admin写了个todo帮助自己管理日常,但他好像没调试完就部署了….一个月后,当他再一次打开他的小网站,似乎忘记了密码…他的todo之前记录了很重要的东西,快帮帮他
不要爆破!Challenge Address
注册个账号登录,发现返回来的 token 是 JWT。
eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJJRCI6MTcyNywiVXNlck5hbWUiOiJtZW93IiwiUGhvbmUiOiIiLCJFbWFpbCI6IiIsImV4cCI6MTY0MzA4ODQxMCwiaXNzIjoiTUpjbG91ZHMifQ.Or2NibhPn-EFCmzn7KhmRAZIv8lWJOM4phafnW22fHo到 https://jwt.io/ 改一下 username 为 admin, ID 为 1 就行了,甚至 secret 为空。
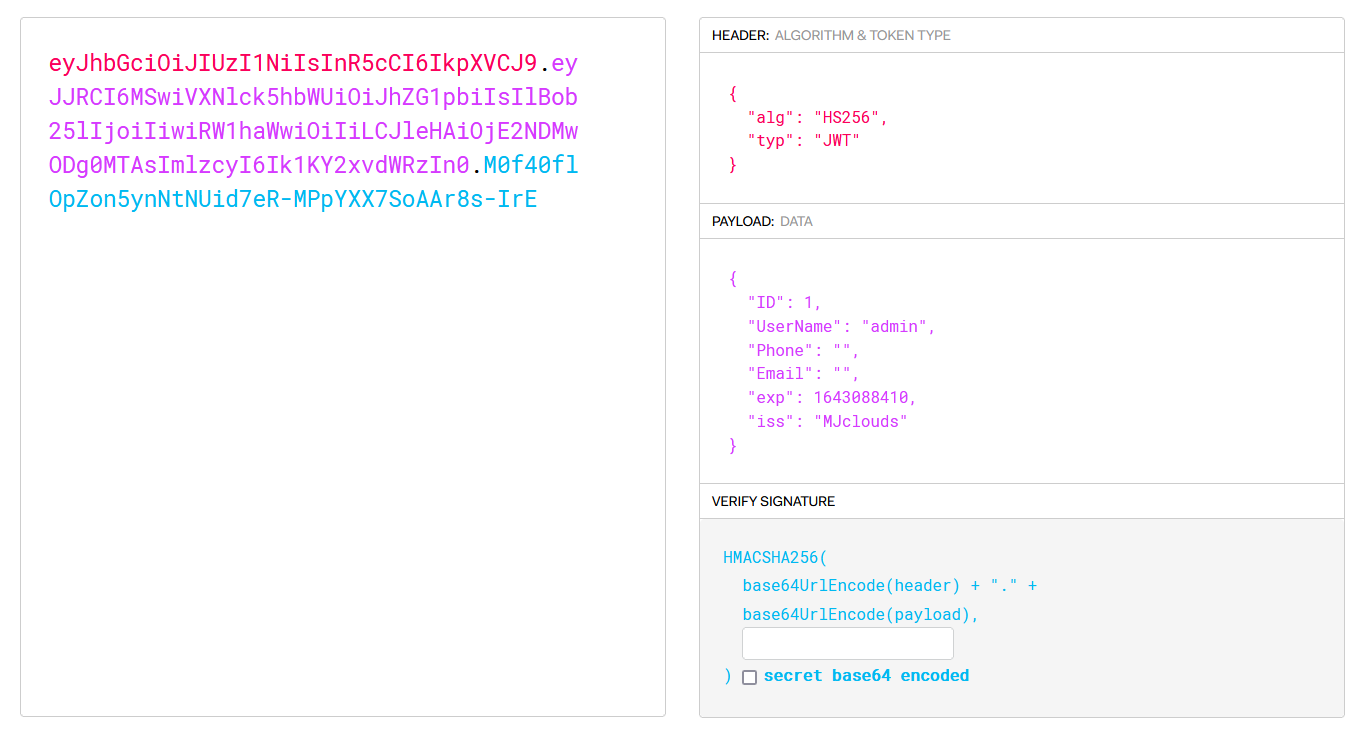
eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJJRCI6MSwiVXNlck5hbWUiOiJhZG1pbiIsIlBob25lIjoiIiwiRW1haWwiOiIiLCJleHAiOjE2NDMwODg0MTAsImlzcyI6Ik1KY2xvdWRzIn0.M0f40flOpZon5ynNtNUid7eR-MPpYXX7SoAAr8s-IrE然后把 localStorage 里的 token 改成这个,刷新页面就看到 flag 了。
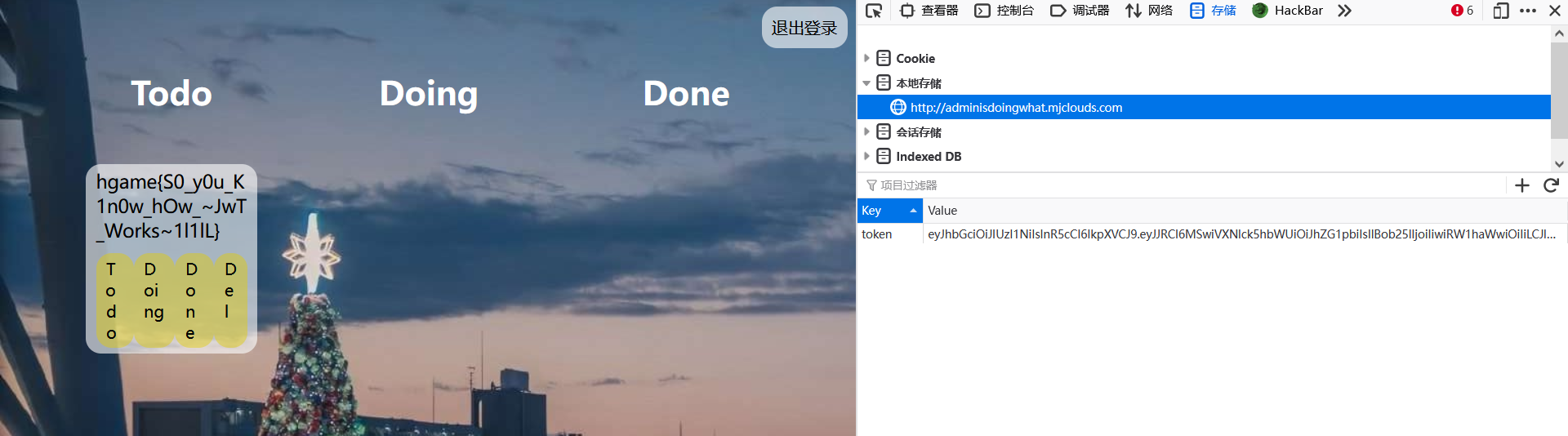
hgame{S0_y0u_K1n0w_hOw_~JwT_Works~1l1lL}
蛛蛛…嘿嘿♥我的蛛蛛
Description
蛛蛛…嘿嘿…我的蛛蛛…我的蛛蛛正在满地找头???
Challenge Address
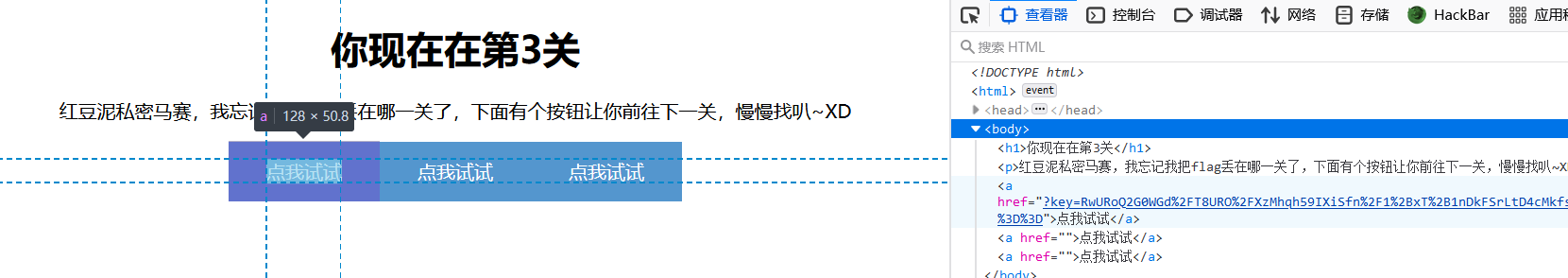
只有一个 a 标签有链接,反正写个脚本提取,不断访问下去就行了。
exp:
"""
MiaoTony
"""
from bs4 import BeautifulSoup
import requests
def is_valid_href(tag):
return tag.has_attr('href') and tag.get('href') != ''
url_raw = "https://hgame-spider.vidar.club/786a9cef21"
url = url_raw
cnt = 1
while True:
print(cnt)
r = requests.get(url)
# if 'hgame' in r.text:
if cnt == 100:
print(r.text)
break
soup = BeautifulSoup(r.text, 'lxml')
l = soup.find(is_valid_href)
print(l.get('href'))
url = url_raw + l.get('href')
cnt += 1
print('==========')最后100的时候是这个
https://hgame-spider.vidar.club/786a9cef21?key=RwURoQ2G0WGd%2FT8URO%2FXzMhqh59IXiSfn%2F1%2BxT%2B1nDng9X6mbXiFKg7vizZgM0iQlCH6bBTugENNpAKkNEhiIQ%3D%3D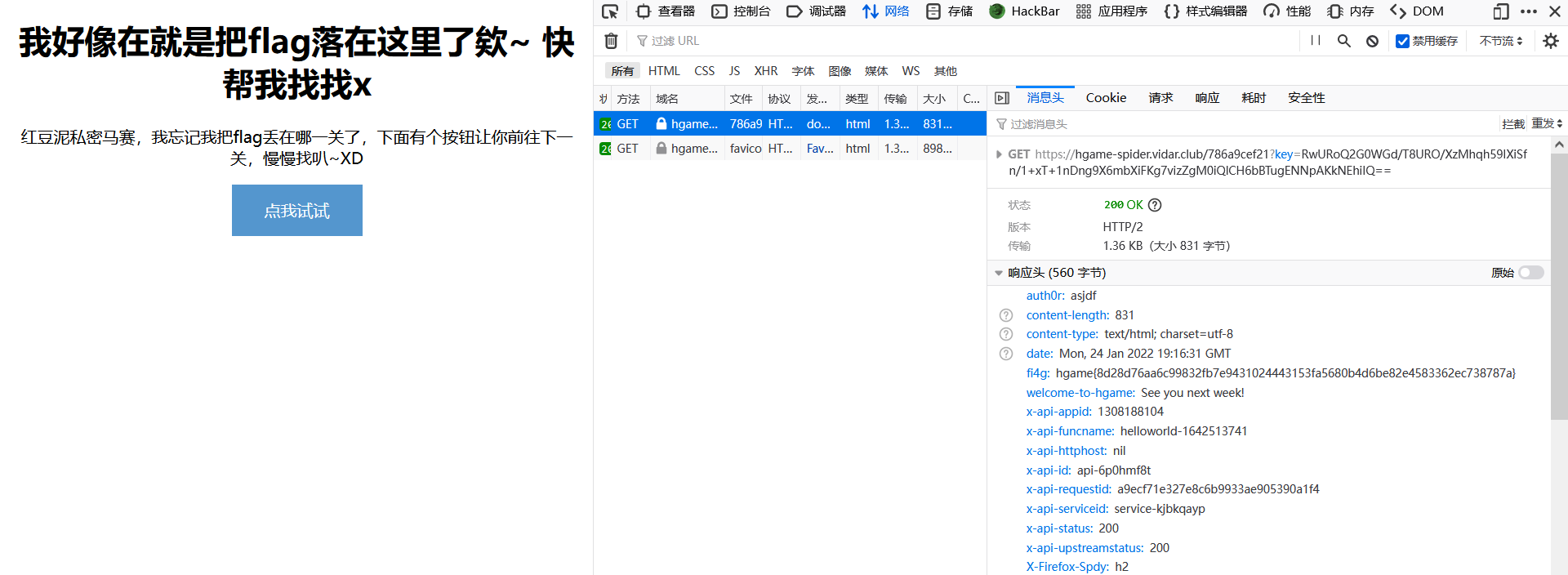
flag 藏 header 里了。
Tetris plus
Description
据说没人能超过 3000 分。要是做题做累了,就来玩玩小游戏吧(x
Challenge Address
checking.js
[][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]][([][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+[]]+([][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]]((!![]+[])[+!+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+([][[]]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+!+[]]+([]+[])[(![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(!![]+[])[+[]]+([][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]]()[+!+[]+[!+[]+!+[]]]+((![]+[])[+!+[]]+(![]+[])[!+[]+!+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]+(!![]+[])[+[]]+[+!+[]]+[!+[]+!+[]+!+[]+!+[]+!+[]+!+[]]+[!+[]+!+[]+!+[]+!+[]]+(!![]+[])[+[]]+[!+[]+!+[]+!+[]+!+[]+!+[]]+[+[]]+(!![]+[])[+[]]+[!+[]+!+[]+!+[]+!+[]]+[!+[]+!+[]]+(!![]+[])[+[]]+[+!+[]]+[!+[]+!+[]+!+[]+!+[]+!+[]]+[+[]]+(!![]+[])[+[]]+[+!+[]]+[!+[]+!+[]+!+[]+!+[]]+[!+[]+!+[]+!+[]+!+[]+!+[]+!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]+[+!+[]]+[!+[]+!+[]+!+[]+!+[]+!+[]]+[!+[]+!+[]+!+[]+!+[]+!+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+[+!+[]]+[!+[]+!+[]+!+[]+!+[]+!+[]+!+[]+!+[]]+[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+[+!+[]]+[!+[]+!+[]+!+[]+!+[]+!+[]]+[!+[]+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(![]+[])[+[]]+([][[]]+[])[+[]]+(!![]+[])[+[]]+[+!+[]]+[!+[]+!+[]+!+[]+!+[]]+[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+[+!+[]]+[!+[]+!+[]+!+[]+!+[]+!+[]]+[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+[+!+[]]+[!+[]+!+[]+!+[]]+[!+[]+!+[]+!+[]+!+[]+!+[]+!+[]+!+[]]+[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+[+!+[]]+[!+[]+!+[]+!+[]]+[!+[]+!+[]+!+[]+!+[]+!+[]+!+[]+!+[]]+(!![]+[])[+[]]+[+!+[]]+[!+[]+!+[]]+[!+[]+!+[]+!+[]]+[+[]]+(!![]+[])[+[]]+[+!+[]]+[!+[]+!+[]+!+[]]+[!+[]+!+[]+!+[]+!+[]+!+[]+!+[]+!+[]]+(![]+[])[+[]]+(!![]+[])[+[]]+[+!+[]]+[!+[]+!+[]]+[!+[]+!+[]+!+[]+!+[]+!+[]]+([][[]]+[])[+[]]+[+!+[]]+([][[]]+[])[+!+[]]+(!![]+[])[+[]]+[+!+[]]+[!+[]+!+[]+!+[]+!+[]+!+[]+!+[]+!+[]]+[!+[]+!+[]+!+[]+!+[]+!+[]]+(!![]+[])[+[]]+[!+[]+!+[]+!+[]+!+[]]+[!+[]+!+[]]+(!![]+[])[+[]]+[!+[]+!+[]+!+[]+!+[]+!+[]]+[+!+[]])[(![]+[])[!+[]+!+[]+!+[]]+(+(!+[]+!+[]+[+!+[]]+[+!+[]]))[(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]])[+!+[]+[+[]]]+([]+[])[([][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+[]]+([][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]][([][[]]+[])[+!+[]]+(![]+[])[+!+[]]+((+[])[([][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+[]]+([][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]]+[])[+!+[]+[+!+[]]]+(!![]+[])[!+[]+!+[]+!+[]]]](!+[]+!+[]+!+[]+[+!+[]])[+!+[]]+(![]+[])[!+[]+!+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(!![]+[])[+[]]]((!![]+[])[+[]])[([][(!![]+[])[!+[]+!+[]+!+[]]+([][[]]+[])[+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(!![]+[])[!+[]+!+[]+!+[]]+(![]+[])[!+[]+!+[]+!+[]]]()+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]])[+!+[]+[+[]]]+([![]]+[][[]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]](([][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]][([][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+[]]+([][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]]((!![]+[])[+!+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+([][[]]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+!+[]]+(![]+[+[]])[([![]]+[][[]])[+!+[]+[+[]]]+(!![]+[])[+[]]+(![]+[])[+!+[]]+(![]+[])[!+[]+!+[]]+([![]]+[][[]])[+!+[]+[+[]]]+([][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]]+[])[!+[]+!+[]+!+[]]+(![]+[])[!+[]+!+[]+!+[]]]()[+!+[]+[+[]]]+![]+(![]+[+[]])[([![]]+[][[]])[+!+[]+[+[]]]+(!![]+[])[+[]]+(![]+[])[+!+[]]+(![]+[])[!+[]+!+[]]+([![]]+[][[]])[+!+[]+[+[]]]+([][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]]+[])[!+[]+!+[]+!+[]]+(![]+[])[!+[]+!+[]+!+[]]]()[+!+[]+[+[]]])()[([][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+[]]+([][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]]((![]+[+[]])[([![]]+[][[]])[+!+[]+[+[]]]+(!![]+[])[+[]]+(![]+[])[+!+[]]+(![]+[])[!+[]+!+[]]+([![]]+[][[]])[+!+[]+[+[]]]+([][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]]+[])[!+[]+!+[]+!+[]]+(![]+[])[!+[]+!+[]+!+[]]]()[+!+[]+[+[]]])+[])[+!+[]])+([]+[])[(![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(!![]+[])[+[]]+([][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]]()[+!+[]+[!+[]+!+[]]])() 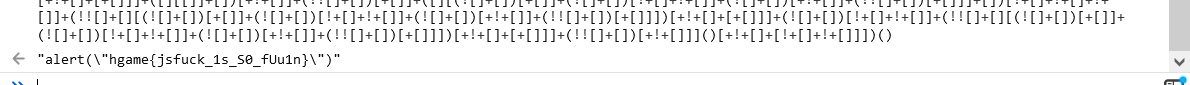
hgame{jsfuck_1s_S0_fUu1n}
Fujiwara Tofu Shop
Description
昨晚我输给一辆AE86。他用惯性漂移过弯,他的车很快,我只看到他有个豆腐店的招牌。
Challenge Address
经典考 header 的题了。
用 X-Forwarded-For 的话会提示 大黑阔也想当车神?
最终 payload:
GET / HTTP/1.1
Host: shop.summ3r.top
User-Agent: Hachi-Roku
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Connection: close
Upgrade-Insecure-Requests: 1
Pragma: no-cache
Cache-Control: no-cache
X-Real-IP: 127.0.0.1
Referer: qiumingshan.net
Cookie: flavor=Raspberry
Gasoline: 100
Content-Length: 0
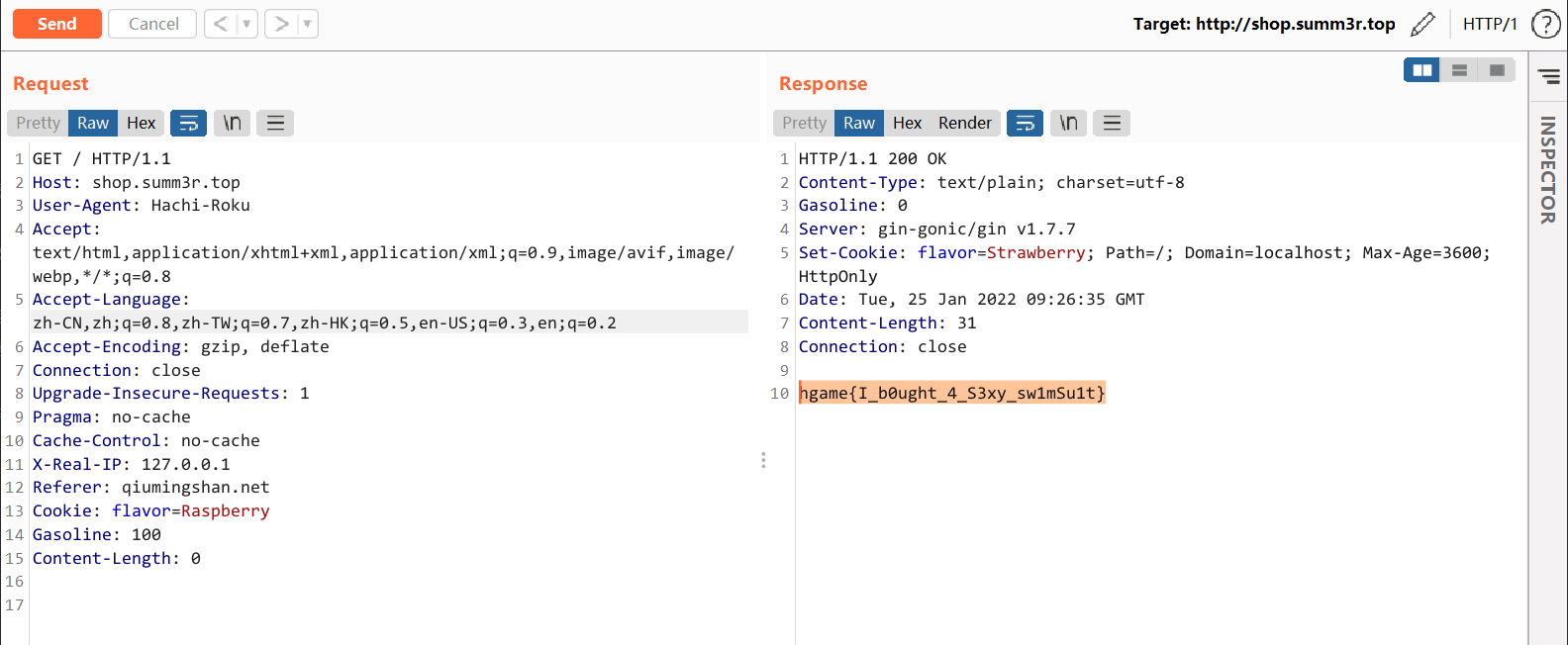
hgame{I_b0ught_4_S3xy_sw1mSu1t}
Misc
欢迎欢迎!热烈欢迎!
Description
关注“奇安信技术研究院”微信公众号,发送
HelloHGAME2022获得flag
hgame{We1com3_t0_HG@ME_2O22}
群青(其实是幽灵东京)
Description
4CTU3从小就是Yoasobi的狂热粉丝 今天它给大家带来了一首它觉得很好听的老歌 它说你要用多感官去感觉
Challenge Address
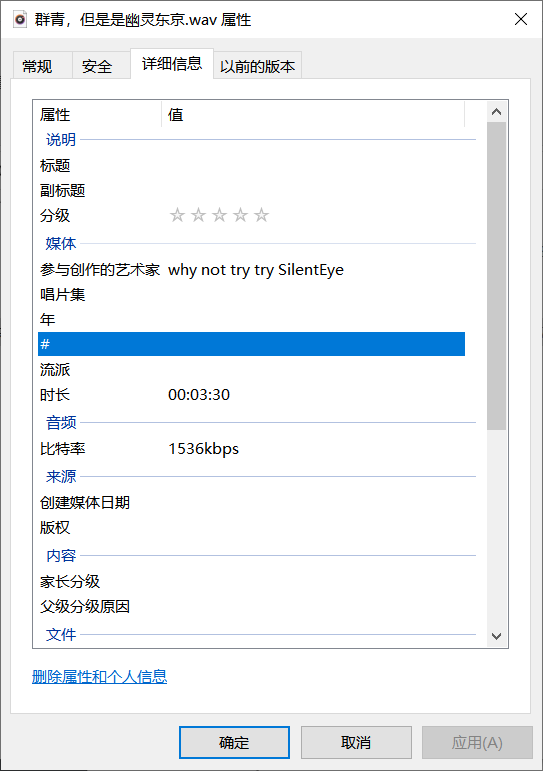
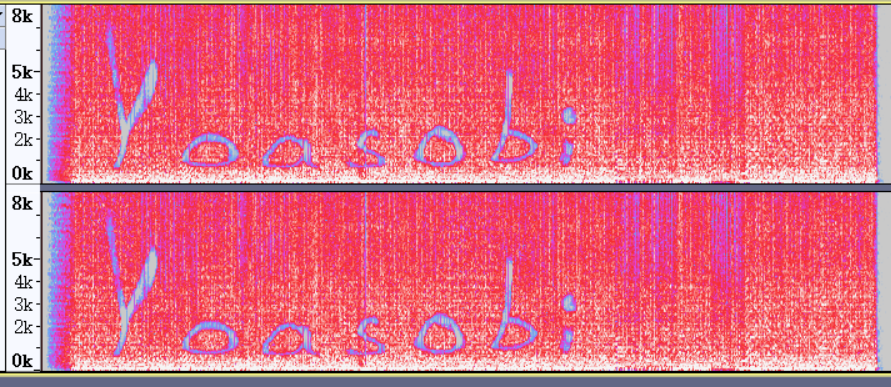
SilentEye Yoasobi
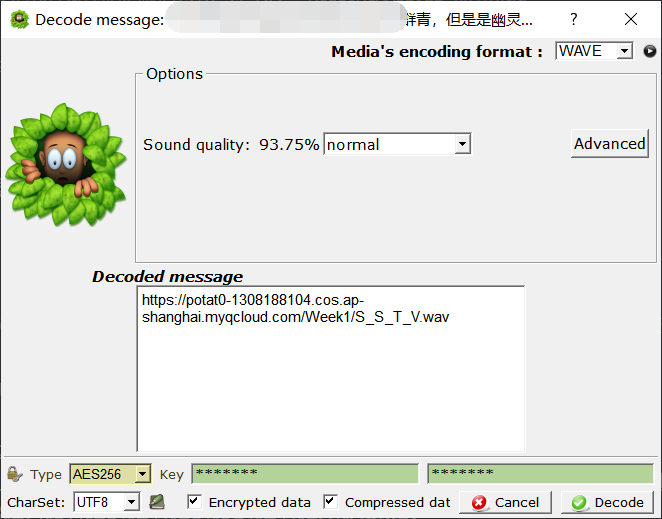
得到 https://potat0-1308188104.cos.ap-shanghai.myqcloud.com/Week1/S_S_T_V.wav
又是 SSTV 呗。
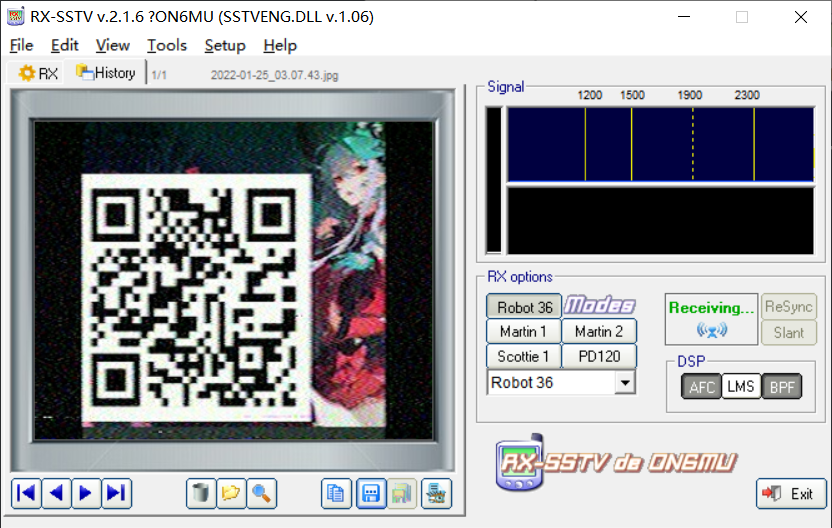

hgame{1_c4n_5ee_the_wav}
好康的流量
Description
总所周知 饭卡是个LSP并十分喜欢向其他人推销他的涩图 让我们去悄悄康康他发了什么
Challenge Address
SMTP 流量
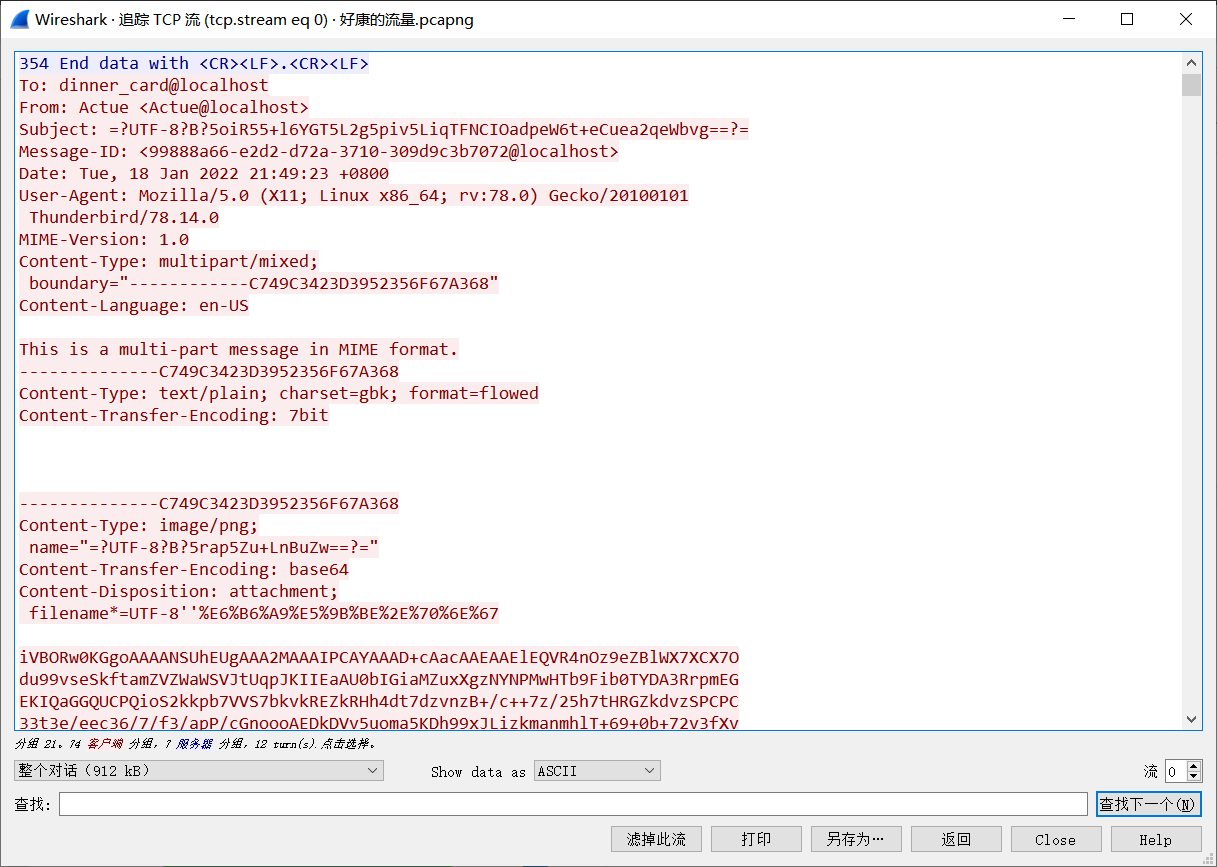
主题是 我知道你是个LSB 来康点涩图(惹
一张图片,base64

green 2(可能要反相

hgame{ez_1mg_
LSB
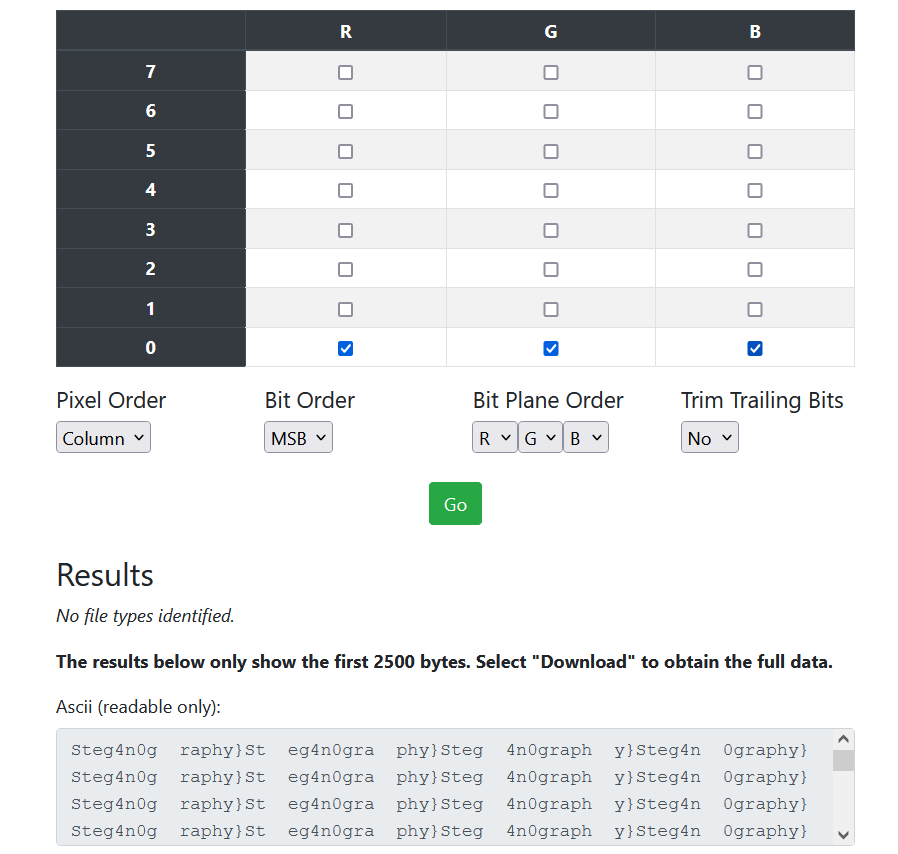
Steg4n0graphy}
hgame{ez_1mg_Steg4n0graphy}
这个压缩包有点麻烦
Description
这个压缩包,它真的可以打开吗?
(附件已更新,请重新下载)Challenge Address
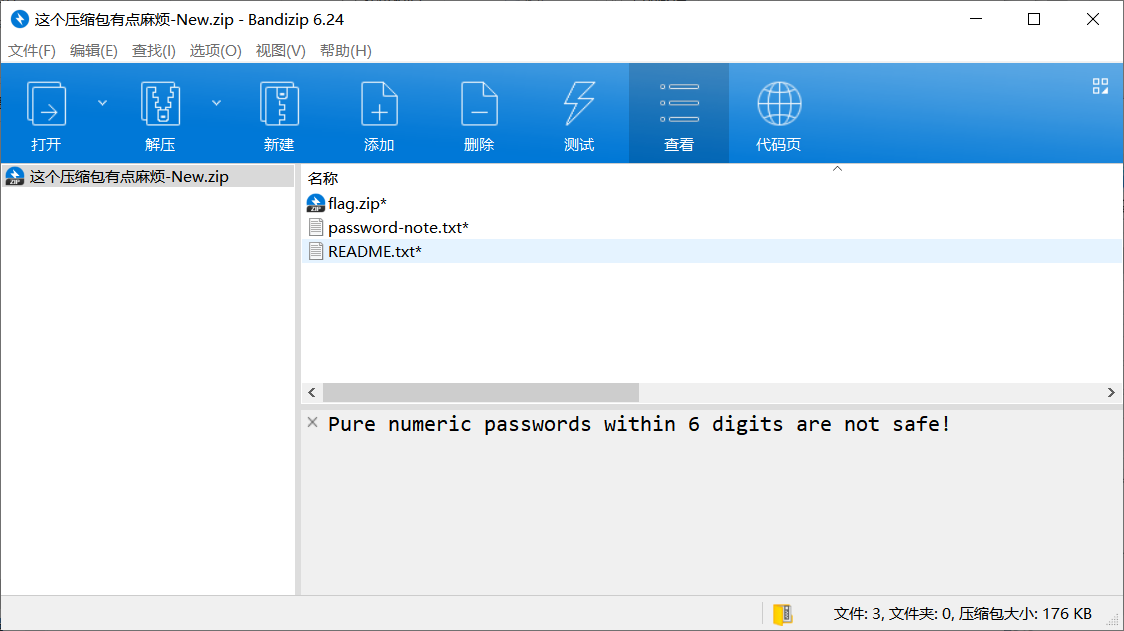
爆破pass 483279
README.txt
I don't know if it's a good idea to write down all the passwords.给了密码字典
&-`;qpCKliw2yTR\If you don't like to spend time compressing files, just stores them.明文攻击 Store
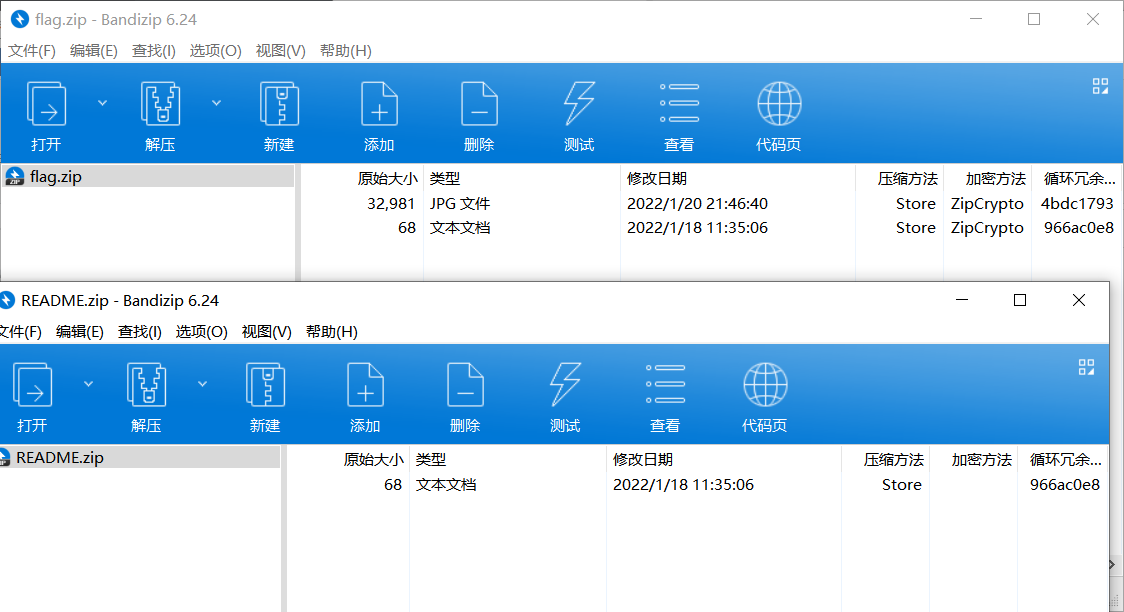
跑了一段时间停掉就行了,得到加密密钥就好,然后确定 把解密后的压缩包保存就完事。
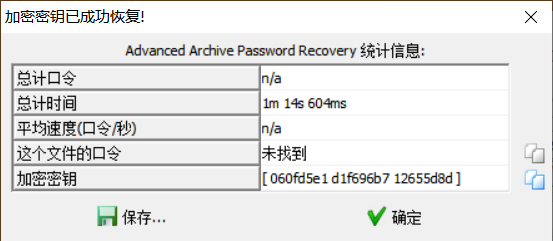

图种,提取出来,伪加密,50 4B 03 04 14 00 09 00 以及 50 4B 01 02 3F 00 14 00 00 00 最后的 09 改 00 就行
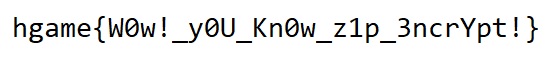
hgame{W0w!_y0U_Kn0w_z1p_3ncrYpt!}
Pwn
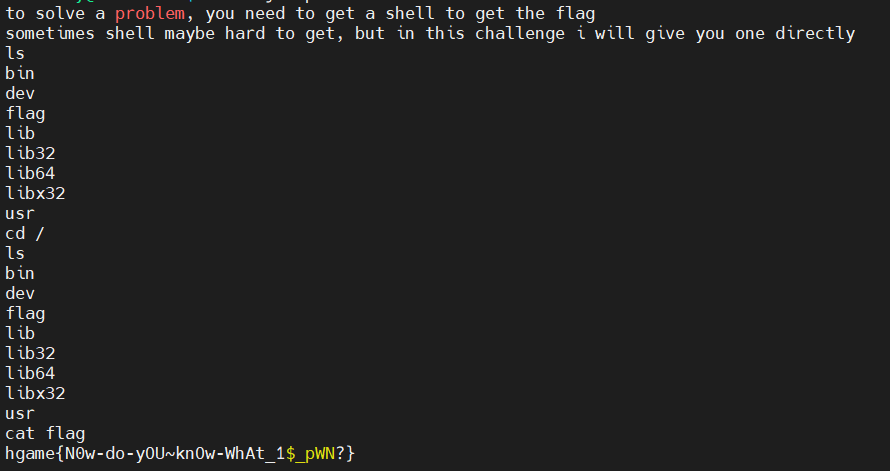
test_your_nc
Description
入门 pwn 的第一步~
Challenge Address
nc chuj.top 50254
Reverse
easyasm
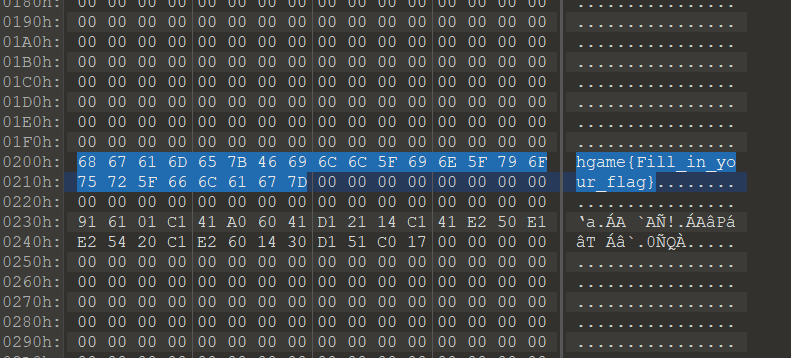
hgame{Fill_in_your_flag} 不对
看看逻辑8,啊,8086CPU,好久没看汇编都快忘完了(((
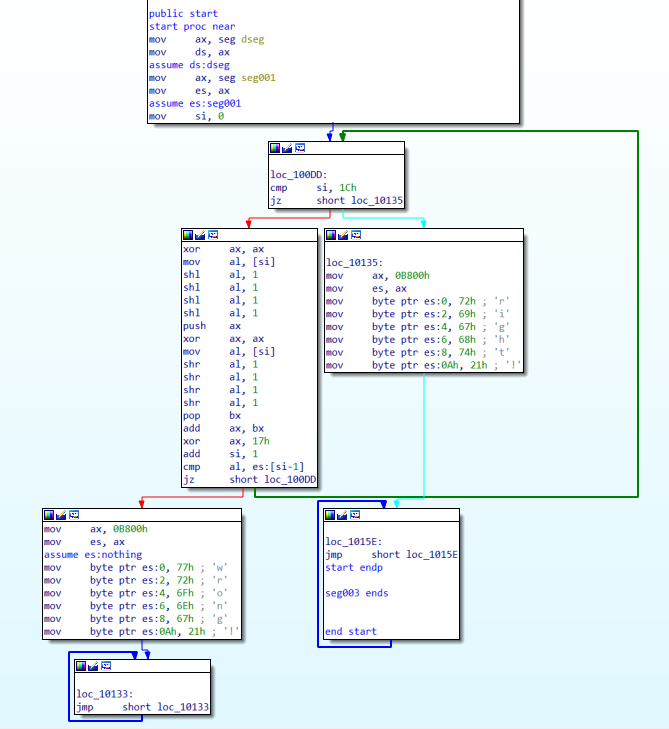
分别取每个字符,逻辑左移4位而后 push,再取同一个字符逻辑右移4位,pop 弹出之前的结果进行相加存到 ax 里,再和 0x17 异或,最后把结果和 es 里的 seg001 做对比,相同即判断下一个字符。
seg001
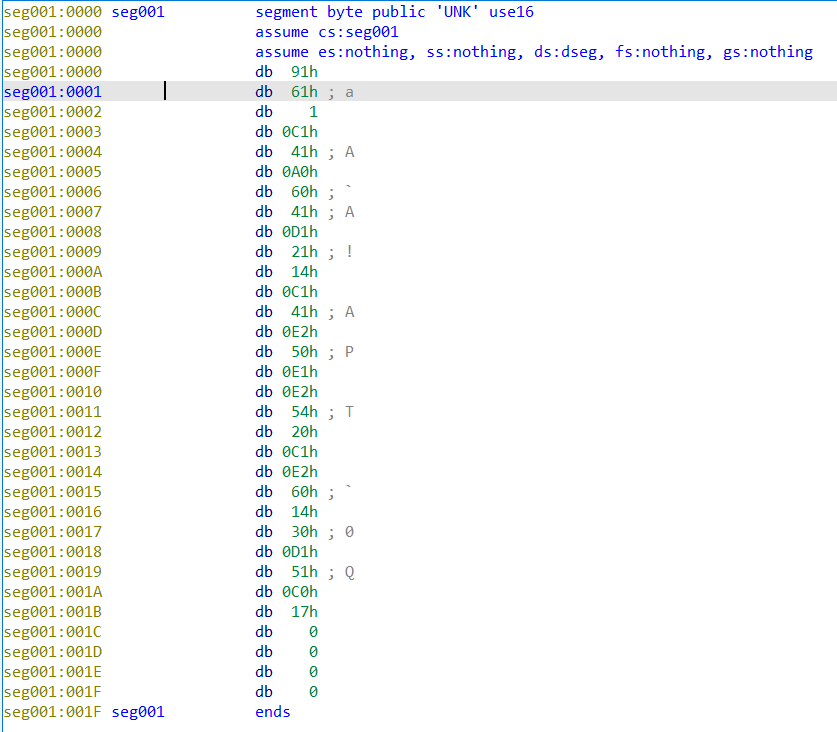
916101C141A06041D12114C141E250E1E25420C1E2601430D151C01700000000反过来写就行了,高4位低4位交换一下就好。
exp:
"""
MiaoTony
"""
with open('seg001.txt', 'r') as f:
s = f.read()
print(s)
b = bytes.fromhex(s)
r = ''
for i in b:
i ^= 0x17
print(i, hex(i))
x = (i % 0x10 << 4) | (i // 0x10)
# print(hex(x))
r += chr(x)
print(r)
# hgame{welc0me_to_4sm_w0rld}Flag Checker
Description
A Flag Checker,can you pass this check?
flag格式:hgame{}Challenge Address
https://0wl-1308188104.cos.ap-shanghai.myqcloud.com/week1/flagchecker.apk
安卓逆向
package com.example.flagchecker;
import android.util.Base64;
import android.view.View;
import android.view.View.OnClickListener;
import android.widget.EditText;
import android.widget.Toast;
class MainActivity$1
implements View.OnClickListener
{
MainActivity$1(MainActivity paramMainActivity) {}
public void onClick(View paramView)
{
Object localObject = ((EditText)this.this$0.findViewById(2131165238)).getText().toString();
paramView = new byte[0];
try
{
localObject = MainActivity.encrypt((String)localObject, "carol");
paramView = (View)localObject;
}
catch (Exception localException)
{
localException.printStackTrace();
}
if (Base64.encodeToString(paramView, 0).replace("\n", "").equals("mg6CITV6GEaFDTYnObFmENOAVjKcQmGncF90WhqvCFyhhsyqq1s=")) {
Toast.makeText(this.this$0, "Congratulations!!!", 1).show();
} else {
Toast.makeText(this.this$0, "Fail,try again.", 1).show();
}
}
}package com.example.flagchecker;
import android.os.Bundle;
import android.support.v7.app.AppCompatActivity;
import android.widget.Button;
import javax.crypto.Cipher;
import javax.crypto.spec.SecretKeySpec;
public class MainActivity
extends AppCompatActivity
{
public static byte[] encrypt(String paramString1, String paramString2)
throws Exception
{
SecretKeySpec localSecretKeySpec = new SecretKeySpec(paramString2.getBytes(), 0, paramString2.length(), "RC4");
paramString2 = Cipher.getInstance("RC4");
paramString2.init(1, localSecretKeySpec);
return paramString2.doFinal(paramString1.getBytes());
}
protected void onCreate(Bundle paramBundle)
{
super.onCreate(paramBundle);
setContentView(2131296284);
((Button)findViewById(2131165218)).setOnClickListener(new MainActivity.1(this));
}
}
RC4 加解密,密码为 carol
构造器 描述 SecretKeySpec(byte[] key, int offset, int len, String algorithm)使用 len的第一个len字节构造来自给定字节数组的key,从offset开始。SecretKeySpec(byte[] key, String algorithm)从给定的字节数组构造一个密钥。
http://tool.chacuo.net/cryptrc4
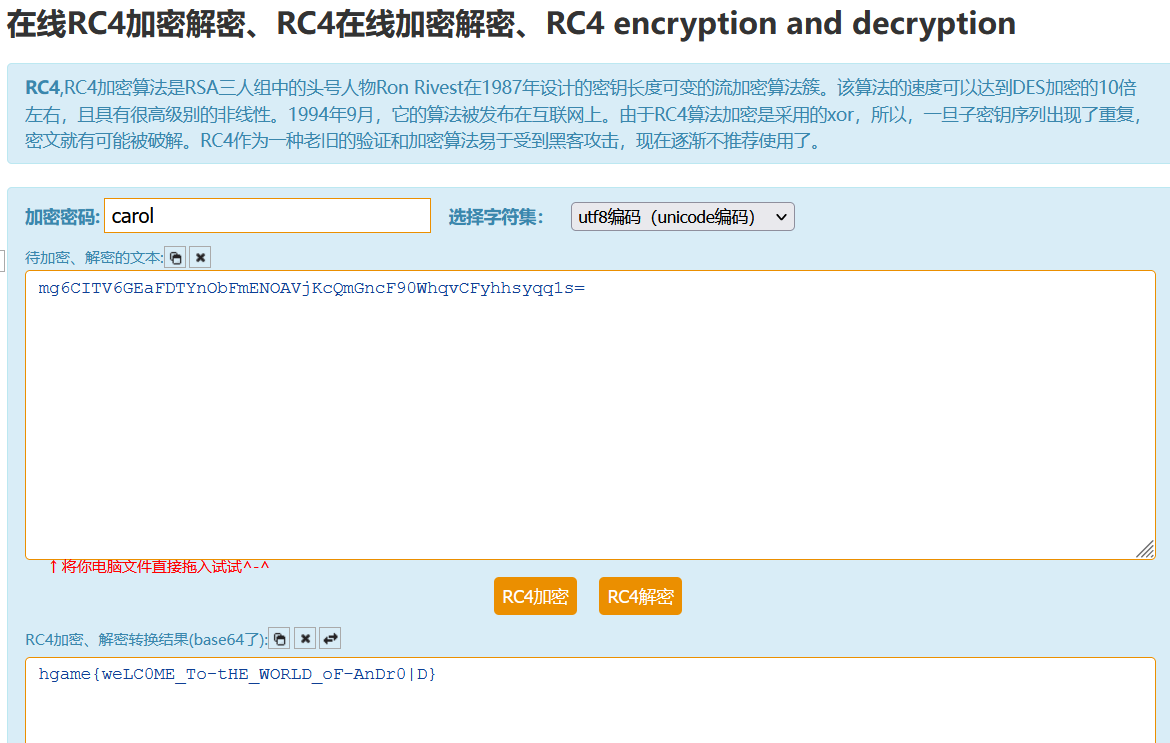
hgame{weLC0ME_To-tHE_WORLD_oF-AnDr0|D}
或者赛博厨子也行
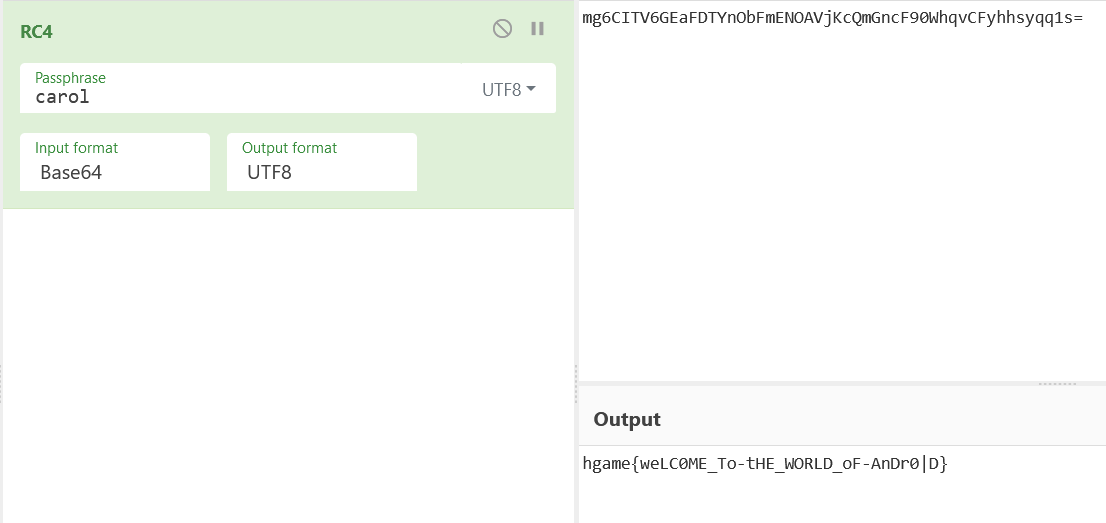
creakme
Description
flag 格式:hgame{}
Challenge Address
https://4nsw3r-1308188104.cos.ap-nanjing.myqcloud.com/a7218184a63354eff3a7adfba246b9e85387ec.exe
拖进 IDA
int __cdecl main(int argc, const char **argv, const char **envp)
{
int v3; // edx
int i; // esi
unsigned int v5; // edi
unsigned int v6; // ebx
int v7; // esi
int v8; // esi
_DWORD v10[17]; // [esp+Ch] [ebp-8Ch] BYREF
__int128 v11[2]; // [esp+50h] [ebp-48h]
char Arglist[32]; // [esp+70h] [ebp-28h] BYREF
int v13; // [esp+90h] [ebp-8h]
int v14; // [esp+94h] [ebp-4h]
memset(Arglist, 0, sizeof(Arglist));
sub_40103A("%s", (char)Arglist);
strcpy((char *)v10, "ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/=");
v3 = 0;
v14 = 0;
for ( i = 0; i < 32; v14 = i )
{
v5 = *(_DWORD *)&Arglist[i];
v6 = *(_DWORD *)&Arglist[i + 4];
v13 = 0;
v7 = 32;
do
{
v3 += 0x12345678;
v5 += v3 ^ (v3 + v6) ^ (v10[2] + 16 * v6) ^ (v10[3] + (v6 >> 5));
v6 += v3 ^ (v3 + v5) ^ (v10[0] + 16 * v5) ^ (v10[1] + (v5 >> 5));
--v7;
}
while ( v7 );
v8 = v14;
v3 = 0;
*(_DWORD *)&Arglist[v14] = v5;
*(_DWORD *)&Arglist[v8 + 4] = v6;
i = v8 + 8;
}
v11[0] = xmmword_402180;
v11[1] = xmmword_402170;
while ( Arglist[v3] == *((_BYTE *)v11 + v3) )
{
if ( ++v3 >= 32 )
{
sub_40100C("right!", v10[0]);
return 0;
}
}
sub_40100C("wrong!", v10[0]);
return 0;
}.rdata:00402170 xmmword_402170 xmmword 65E0F2E3CF9284AABA5A126DAE1FEDE6h
.rdata:00402170 ; DATA XREF: _main+BD↑r
.rdata:00402180 xmmword_402180 xmmword 0ED9CE5ED52EB78C2030C144C48D93488h
.rdata:00402180 ; DATA XREF: _main+B0↑r看起来是魔改的 Tiny Encryption Algorithm (TEA)
(咕
Crypto
Easy RSA
Description
这 RSA 不是有手就行?!
(100分的题能拿125分,这不血赚)Challenge Address
[https://cmfj-1308188104.cos.ap-shanghai.myqcloud.com/Week1/Easy%20RSA.zip](https://cmfj-1308188104.cos.ap-shanghai.myqcloud.com/Week1/Easy RSA.zip)
Task:
from math import gcd
from random import randint
from gmpy2 import next_prime
from Crypto.Util.number import getPrime
from secret import flag
def encrypt(c):
p = getPrime(8)
q = getPrime(8)
e = randint(0, p * q)
while gcd(e, (p - 1) * (q - 1)) != 1:
e = int(next_prime(e))
return e, p, q, pow(ord(c), e, p * q)
if __name__ == '__main__':
print(list(map(encrypt, flag)))
# [(12433, 149, 197, 104), (8147, 131, 167, 6633), (10687, 211, 197, 35594), (19681, 131, 211, 15710), (33577, 251, 211, 38798), (30241, 157, 251, 35973), (293, 211, 157, 31548), (26459, 179, 149, 4778), (27479, 149, 223, 32728), (9029, 223, 137, 20696), (4649, 149, 151, 13418), (11783, 223, 251, 14239), (13537, 179, 137, 11702), (3835, 167, 139, 20051), (30983, 149, 227, 23928), (17581, 157, 131, 5855), (35381, 223, 179, 37774), (2357, 151, 223, 1849), (22649, 211, 229, 7348), (1151, 179, 223, 17982), (8431, 251, 163, 30226), (38501, 193, 211, 30559), (14549, 211, 151, 21143), (24781, 239, 241, 45604), (8051, 179, 131, 7994), (863, 181, 131, 11493), (1117, 239, 157, 12579), (7561, 149, 199, 8960), (19813, 239, 229, 53463), (4943, 131, 157, 14606), (29077, 191, 181, 33446), (18583, 211, 163, 31800), (30643, 173, 191, 27293), (11617, 223, 251, 13448), (19051, 191, 151, 21676), (18367, 179, 157, 14139), (18861, 149, 191, 5139), (9581, 211, 193, 25595)]
Exp:
"""
MiaoTony
"""
import gmpy2
from Crypto.Util.number import long_to_bytes
l = [(12433, 149, 197, 104), (8147, 131, 167, 6633), (10687, 211, 197, 35594), (19681, 131, 211, 15710), (33577, 251, 211, 38798), (30241, 157, 251, 35973), (293, 211, 157, 31548), (26459, 179, 149, 4778), (27479, 149, 223, 32728), (9029, 223, 137, 20696), (4649, 149, 151, 13418), (11783, 223, 251, 14239), (13537, 179, 137, 11702), (3835, 167, 139, 20051), (30983, 149, 227, 23928), (17581, 157, 131, 5855), (35381, 223, 179, 37774), (2357, 151, 223, 1849), (22649, 211, 229, 7348),
(1151, 179, 223, 17982), (8431, 251, 163, 30226), (38501, 193, 211, 30559), (14549, 211, 151, 21143), (24781, 239, 241, 45604), (8051, 179, 131, 7994), (863, 181, 131, 11493), (1117, 239, 157, 12579), (7561, 149, 199, 8960), (19813, 239, 229, 53463), (4943, 131, 157, 14606), (29077, 191, 181, 33446), (18583, 211, 163, 31800), (30643, 173, 191, 27293), (11617, 223, 251, 13448), (19051, 191, 151, 21676), (18367, 179, 157, 14139), (18861, 149, 191, 5139), (9581, 211, 193, 25595)]
def decrypt(x):
e, p, q, c = x
phi = (p-1) * (q-1)
d = gmpy2.invert(e, phi)
return chr(pow(c, d, p*q))
for i in l:
print(decrypt(i), end='')
# hgame{L00ks_l1ke_y0u've_mastered_RS4!}Matryoshka
Description
某天饭卡捡到了张奇怪的纸条。
上面写满了奇奇怪怪的字符。
纸条背面还写着奇怪的话:“Caesar:21; Vigenère:hgame”。
你能看懂上面写了什么吗?Challenge Address
https://cmfj-1308188104.cos.ap-shanghai.myqcloud.com/Week1/Matryoshka.zip
题目名称就是套娃啊((
⠨⠨⠤⠌⠤⠤⠨⠨⠨⠌⠤⠤⠨⠨⠤⠤⠌⠤⠤⠤⠤⠤⠌⠤⠤⠨⠨⠨⠌⠤⠤⠨⠨⠤⠤⠌⠤⠤⠤⠨⠨⠌⠨⠨⠨⠤⠤⠌⠤⠤⠨⠨⠤⠤⠌⠨⠤⠨⠨⠌⠨⠨⠨⠨⠤⠌⠤⠤⠨⠨⠤⠤⠌⠨⠨⠤⠤⠤⠌⠨⠨⠨⠨⠤⠌⠤⠤⠨⠨⠤⠤⠌⠨⠨⠤⠤⠤⠌⠤⠤⠨⠨⠨⠌⠤⠤⠨⠨⠤⠤⠌⠨⠤⠨⠤⠌⠤⠨⠨⠨⠨⠌⠤⠤⠨⠨⠤⠤⠌⠨⠨⠨⠤⠌⠨⠨⠨⠨⠤⠌⠤⠤⠨⠨⠤⠤⠌⠨⠨⠨⠨⠤⠌⠤⠤⠨⠨⠨⠌⠤⠤⠨⠨⠤⠤⠌⠤⠤⠤⠨⠨⠌⠨⠨⠨⠨⠨⠌⠤⠤⠨⠨⠤⠤⠌⠤⠤⠤⠨⠨⠌⠤⠤⠨⠨⠨⠌⠤⠤⠨⠨⠤⠤⠌⠨⠨⠨⠤⠌⠤⠨⠨⠨⠨⠌⠤⠤⠨⠨⠤⠤⠌⠤⠤⠤⠨⠨⠌⠨⠨⠨⠤⠤⠌⠤⠤⠨⠨⠤⠤⠌⠨⠤⠤⠤⠤⠌⠤⠤⠨⠨⠨⠌⠤⠤⠨⠨⠤⠤⠌⠤⠤⠨⠨⠨⠌⠨⠨⠨⠤⠤⠌⠤⠤⠨⠨⠤⠤⠌⠨⠨⠨⠤⠌⠨⠨⠨⠨⠤⠌⠤⠤⠨⠨⠤⠤⠌⠤⠨⠌⠨⠨⠨⠨⠤⠌⠤⠤⠨⠨⠤⠤⠌⠤⠤⠤⠤⠨⠌⠤⠤⠨⠨⠨⠌⠤⠤⠨⠨⠤⠤⠌⠤⠤⠨⠨⠨⠌⠨⠨⠨⠨⠨⠌⠤⠤⠨⠨⠤⠤⠌⠨⠨⠤⠌⠤⠨⠨⠨⠨⠌⠤⠤⠨⠨⠤⠤⠌⠨⠤⠨⠨⠌⠨⠨⠨⠨⠤⠌⠤⠤⠨⠨⠤⠤⠌⠨⠤⠤⠤⠤⠌⠤⠤⠨⠨⠨⠌⠤⠤⠨⠨⠤⠤⠌⠨⠌⠤⠨⠨⠨⠨⠌⠤⠤⠨⠨⠤⠤⠌⠤⠤⠤⠤⠨⠌⠨⠨⠨⠨⠨⠌⠤⠤⠨⠨⠤⠤⠌⠤⠤⠤⠨⠨⠌⠨⠨⠨⠤⠤⠌⠤⠤⠨⠨⠤⠤⠌⠨⠤⠤⠤⠤⠌⠤⠤⠨⠨⠨⠌⠤⠤⠨⠨⠤⠤⠌⠨⠨⠤⠌⠨⠨⠨⠨⠤⠌⠤⠤⠨⠨⠤⠤⠌⠨⠨⠨⠤⠌⠨⠨⠨⠨⠤⠌⠤⠤⠨⠨⠤⠤⠌⠨⠤⠤⠤⠤⠌⠨⠨⠨⠤⠤⠌⠤⠤⠨⠨⠤⠤⠌⠨⠤⠨⠤⠌⠨⠨⠨⠨⠤⠌⠤⠤⠨⠨⠤⠤⠌⠤⠤⠨⠨⠨⠌⠨⠨⠨⠨⠨⠌⠤⠤⠨⠨⠤⠤⠌⠤⠨⠨⠨⠨⠌⠨⠨⠨⠨⠤⠌⠤⠤⠨⠨⠤⠤⠌⠤⠤⠨⠨⠨⠌⠨⠨⠨⠨⠤⠌⠤⠤⠨⠨⠤⠤⠌⠤⠤⠤⠤⠤⠌⠤⠤⠨⠨⠨⠌⠤⠤⠨⠨⠤⠤⠌⠨⠌⠤⠨⠨⠨⠨⠌⠤⠤⠨⠨⠤⠤⠌⠨⠤⠤⠤⠤⠌⠨⠨⠨⠨⠤⠌⠤⠤⠨⠨⠤⠤⠌⠤⠨⠨⠨⠨⠌⠤⠤⠨⠨⠨⠌⠤⠤⠨⠨⠤⠤⠌⠤⠤⠤⠤⠤⠌⠨⠨⠨⠤⠤⠌⠤⠤⠨⠨⠤⠤⠌⠤⠤⠤⠨⠨⠌⠤⠤⠨⠨⠨⠌⠤⠤⠨⠨⠤⠤⠌⠨⠨⠤⠤⠤⠌⠨⠨⠨⠨⠨⠌⠤⠤⠨⠨⠤⠤⠌⠨⠨⠨⠨⠤⠌⠤⠤⠨⠨⠨⠌⠤⠤⠨⠨⠤⠤⠌⠨⠤⠨⠤⠌⠤⠨⠨⠨⠨⠌⠤⠤⠨⠨⠤⠤⠌⠤⠨⠨⠨⠨⠌⠨⠨⠨⠤⠤⠌⠤⠤⠨⠨⠤⠤⠌⠨⠤⠤⠤⠤⠌⠨⠨⠨⠨⠨⠌⠤⠤⠨⠨⠤⠤⠌⠨⠤⠤⠤⠤⠌⠨⠨⠨⠨⠤⠌⠤⠤⠨⠨⠤⠤⠌⠤⠤⠨⠨⠨⠌⠨⠨⠨⠤⠤⠌⠤⠤⠨⠨⠤⠤⠌⠤⠤⠨⠨⠨⠌⠤⠤⠨⠨⠨⠌⠤⠤⠨⠨⠤⠤⠌⠤⠨⠨⠨⠨⠌⠤⠨⠨⠨⠨⠌⠤⠤⠨⠨⠤⠤⠌⠨⠨⠨⠨⠤⠌⠤⠤⠨⠨⠨⠌⠤⠤⠨⠨⠤⠤⠌⠤⠤⠨⠨⠨⠌⠨⠨⠨⠤⠤⠌⠤⠤⠨⠨⠤⠤⠌⠨⠤⠨⠤⠌⠤⠨⠨⠨⠨⠌⠤⠤⠨⠨⠤⠤⠌⠨⠨⠤⠌⠨⠨⠨⠨⠤⠌⠤⠤⠨⠨⠤⠤⠌⠨⠌⠨⠨⠨⠨⠤⠌⠤⠤⠨⠨⠤⠤⠌⠨⠨⠨⠨⠤⠌⠤⠨⠨⠨⠨⠌⠤⠤⠨⠨⠤⠤⠌⠨⠨⠨⠨⠨⠌⠤⠨⠨⠨⠨⠌⠤⠤⠨⠨⠤⠤⠌⠨⠨⠨⠨⠤⠌⠨⠨⠨⠨⠤⠌⠤⠤⠨⠨⠤⠤⠌⠨⠨⠨⠨⠨⠌⠨⠨⠨⠤⠤⠌⠤⠤⠨⠨⠤⠤⠌⠤⠤⠤⠨⠨⠌⠤⠨⠨⠨⠨⠌⠤⠤⠨⠨⠤⠤⠌⠨⠨⠨⠨⠤⠌⠨⠨⠨⠨⠤⠌⠤⠤⠨⠨⠤⠤⠌⠨⠨⠨⠨⠤⠌⠤⠨⠨⠨⠨是盲文,以为是加密,试了几个
https://www.qqxiuzi.cn/bianma/wenbenjiami.php?s=mangwen
或者 http://www.atoolbox.net/Tool.php?Id=837
啊,都不行……盲文里没有这种的吧,难道是中文?
中国盲文数字平台汉盲翻译系统,这玩意只能汉字英文转盲文,不能反过来,嘤!
最后发现了这个 https://www.reddit.com/r/codes/comments/nnma6p/funky_cryptography_puzzle_can_anyone_figure_it_out/
噢,赛博厨子就能解啊,我紫菜。
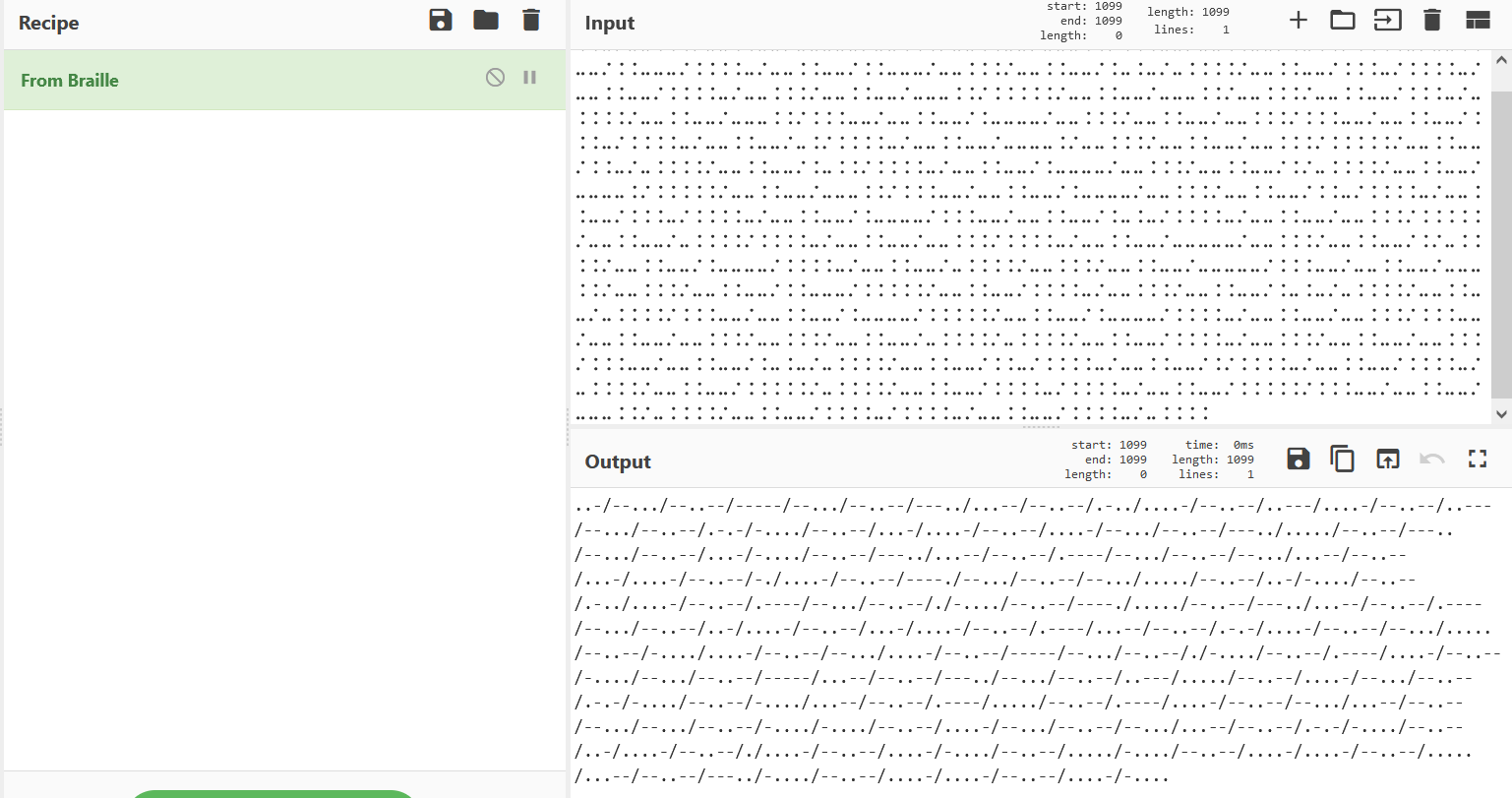
之后是摩斯,不过明显不对,得逆序。。
反正最后是下面这样。
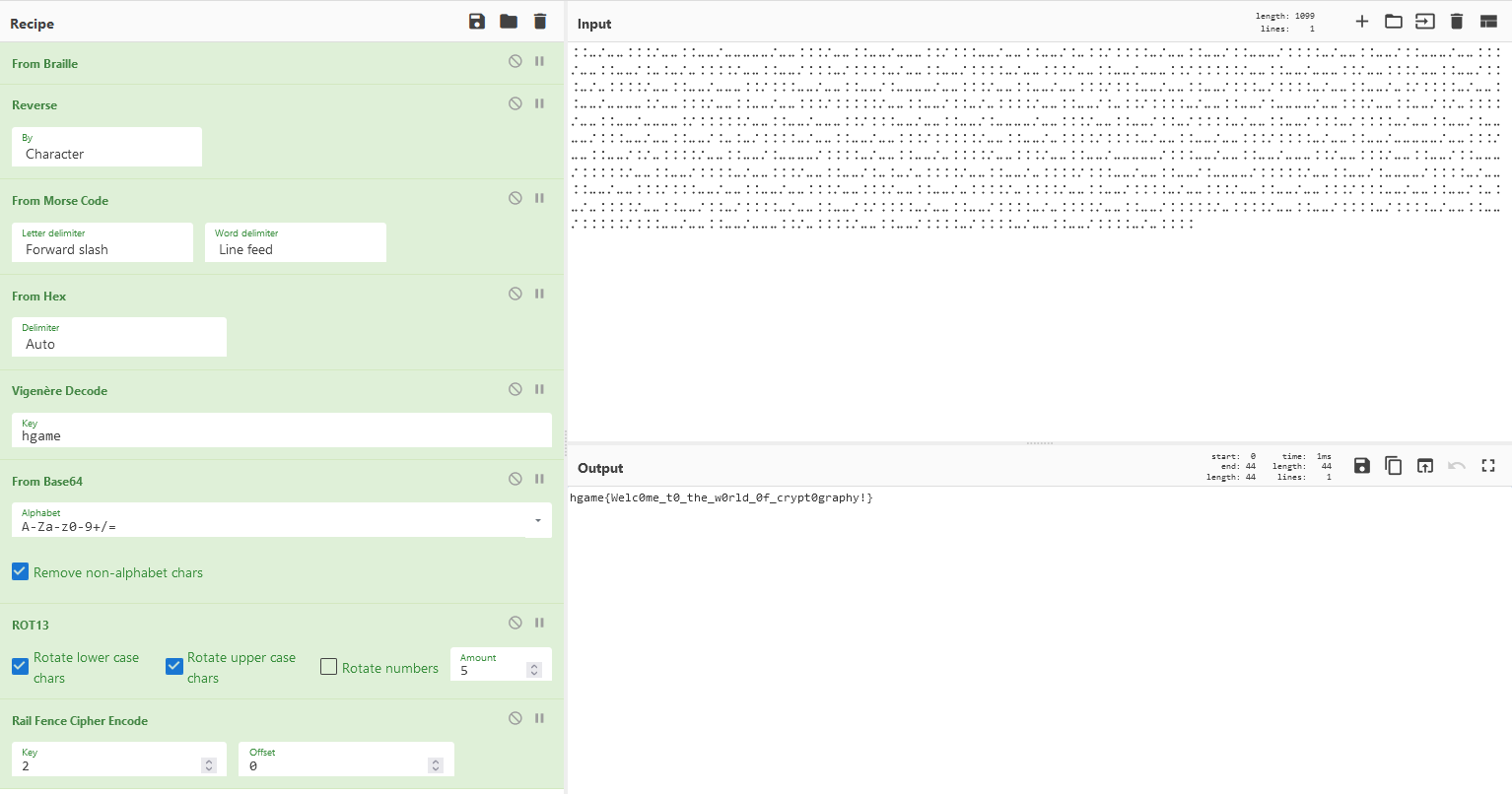
hgame{Welc0me_t0_the_w0rld_0f_crypt0graphy!}
Animal Farm
A Fairy Story by George Orwell
https://www.marxists.org/subject/art/literature/children/texts/orwell/animal-farm/ch09.htm
给了打乱了顺序的原文和密文文件,先匹配一下找到对应关系,再还原 flag 就好了。
小结
就这样吧,水完了,喵~
pwn 好难,呜呜呜。
就要过年啦,祝大家虎年大吉,虎虎生威!
(溜了溜了喵~


