引言
NEWSCTF 2021.6.1萌新赛
比赛时间:2021.5.31 08:00 - 6.3 00:00
唯一官方QQ群:1063624041
六一那几天有个小比赛,不过前段时间比较忙没做几个题,也没空整理。
比赛结束后本来还想复现几个题的,咕着咕着发现都忘记了,这里就把几个简单题发一发好了吧。
Misc
very-ez-dump
链接:https://pan.baidu.com/s/1mqJsQN1kfNFwV0lpGiOBpg 提取码:news
(或去官方比赛群1063624041的群文件-临时题目文件夹中获取)
# volatility -f mem.raw --profile Win7SP1x64 filescan | grep Desktop
Volatility Foundation Volatility Framework 2.6
0x000000003dca8280 4 0 R--r-d \Device\HarddiskVolume1\Users\mumuzi\Desktop\DumpIt.exe
0x000000003dcc8600 2 0 R--rwd \Device\HarddiskVolume1\Users\mumuzi\Links\Desktop.lnk
0x000000003de778f0 2 1 R--rwd \Device\HarddiskVolume1\Users\Public\Desktop
0x000000003dfdcd20 2 1 R--rwd \Device\HarddiskVolume1\Users\mumuzi\Desktop
0x000000003e0e9f20 1 0 R--rwd \Device\HarddiskVolume1\Users\mumuzi\AppData\Roaming\Microsoft\Windows\SendTo\Desktop.ini
0x000000003e156f20 16 0 R--rwd \Device\HarddiskVolume1\Users\mumuzi\Desktop\desktop.ini
0x000000003e15aac0 2 0 R--rwd \Device\HarddiskVolume1\Users\Public\Desktop\desktop.ini
0x000000003e16c250 16 0 R--rwd \Device\HarddiskVolume1\ProgramData\Microsoft\Windows\Start Menu\Programs\Accessories\Desktop.ini
0x000000003e16e070 16 0 R--rwd \Device\HarddiskVolume1\Users\mumuzi\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Accessories\Desktop.ini
0x000000003e16ff20 16 0 R--rwd \Device\HarddiskVolume1\Users\mumuzi\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Maintenance\Desktop.ini
0x000000003e170f20 16 0 R--rwd \Device\HarddiskVolume1\Users\mumuzi\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Accessories\Accessibility\Desktop.ini
0x000000003e171f20 16 0 R--rwd \Device\HarddiskVolume1\Users\mumuzi\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Accessories\System Tools\Desktop.ini
0x000000003e172d00 16 0 R--rwd \Device\HarddiskVolume1\ProgramData\Microsoft\Windows\Start Menu\Programs\Games\Desktop.ini
0x000000003e174e20 16 0 R--rwd \Device\HarddiskVolume1\ProgramData\Microsoft\Windows\Start Menu\Programs\Maintenance\Desktop.ini
0x000000003e175af0 16 0 R--rwd \Device\HarddiskVolume1\ProgramData\Microsoft\Windows\Start Menu\Programs\Accessories\System Tools\Desktop.ini
0x000000003e176890 16 0 R--rwd \Device\HarddiskVolume1\ProgramData\Microsoft\Windows\Start Menu\Programs\Accessories\Accessibility\Desktop.ini
0x000000003e50cd10 16 0 RW-rw- \Device\HarddiskVolume1\Users\mumuzi\Desktop\计算机 - 快捷方式.lnk
0x000000003f6bf330 2 0 R--rwd \Device\HarddiskVolume1\ProgramData\Microsoft\Windows\Start Menu\Programs\Accessories\Remote Desktop Connection.lnk
0x000000003fa20e20 1 1 R--rw- \Device\HarddiskVolume1\Users\mumuzi\Desktop
0x000000003fa4b450 16 0 RW-r-- \Device\HarddiskVolume1\Users\mumuzi\Desktop\hint.txt
0x000000003fa557f0 1 0 R--rwd \Device\HarddiskVolume1\Windows\assembly\Desktop.ini
0x000000003fa62c60 1 0 R--rwd \Device\HarddiskVolume1\Windows\Media\Desktop.ini
0x000000003fa63200 2 1 R--rwd \Device\HarddiskVolume1\Users\mumuzi\Desktop
0x000000003fa77920 2 1 R--rwd \Device\HarddiskVolume1\Users\Public\Desktop
0x000000003fabec90 1 1 RW-rw- \Device\HarddiskVolume1\Users\mumuzi\Desktop\WIN-DLV72BHQ4GL-20210520-130833.raw
0x000000003faf9f20 6 0 R--rwd \Device\HarddiskVolume1\Users\mumuzi\Desktop\DumpIt.exe
# volatility -f mem.raw --profile Win7SP1x64 dumpfiles -Q 0x000000003fa4b450 -D . -u
Volatility Foundation Volatility Framework 2.6
DataSectionObject 0x3fa4b450 None \Device\HarddiskVolume1\Users\mumuzi\Desktop\hint.txt
桌面上有个 hint.txt,提取出来。
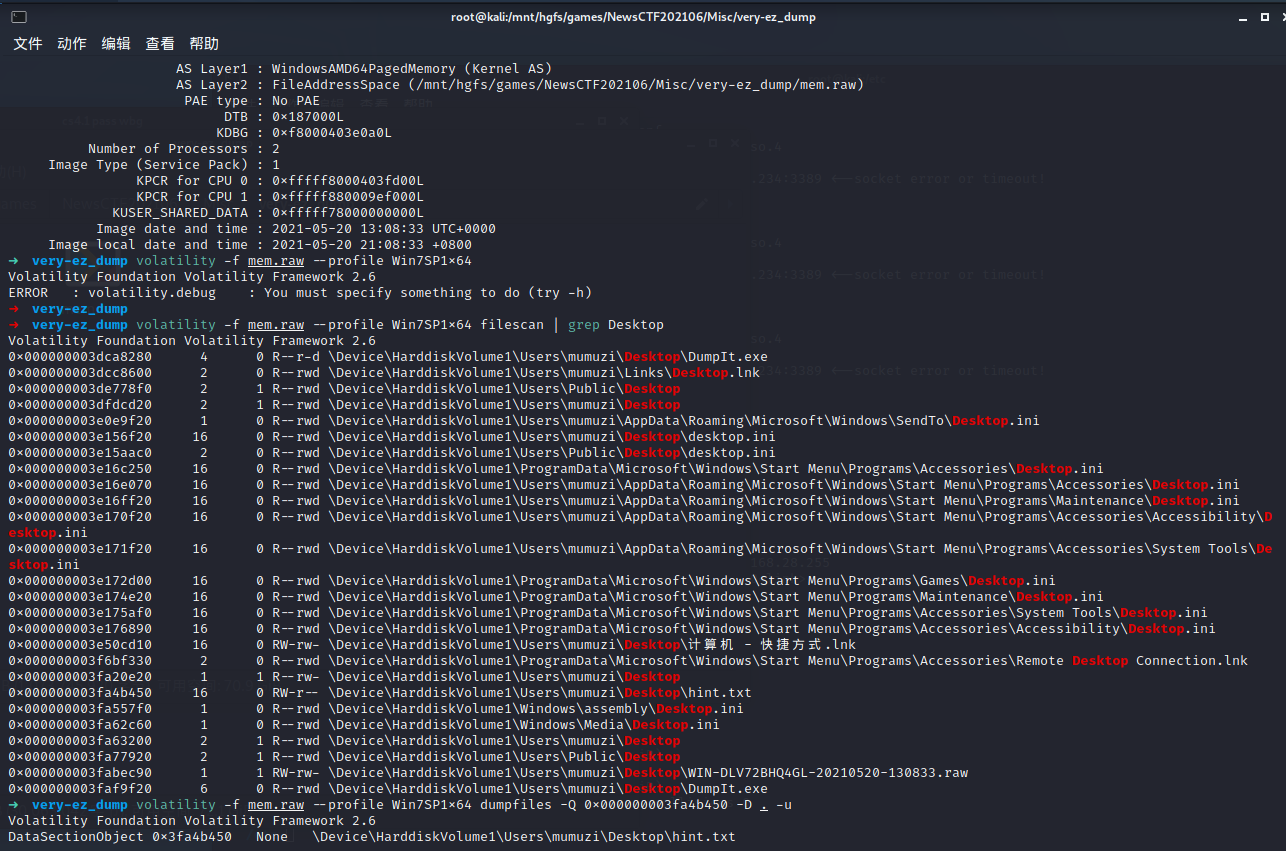
内容是
you ask me where is the passwd?
you can try to find the user passwd.
it is so ez!!!!!! 那就查看内存,提取密码。
# volatility -f mem.raw --profile Win7SP1x64 hivelist
Volatility Foundation Volatility Framework 2.6
Virtual Physical Name
------------------ ------------------ ----
0xfffff8a001108010 0x000000001e9f0010 \??\C:\Windows\ServiceProfiles\LocalService\NTUSER.DAT
0xfffff8a001283010 0x000000003d0fa010 \??\C:\Users\mumuzi\ntuser.dat
0xfffff8a00141b010 0x0000000034bea010 \??\C:\Users\mumuzi\AppData\Local\Microsoft\Windows\UsrClass.dat
0xfffff8a0020bb010 0x000000002482d010 \??\C:\System Volume Information\Syscache.hve
0xfffff8a00000f010 0x00000000208a1010 [no name]
0xfffff8a000024010 0x00000000209ac010 \REGISTRY\MACHINE\SYSTEM
0xfffff8a000053010 0x000000001fddb010 \REGISTRY\MACHINE\HARDWARE
0xfffff8a0000f6010 0x000000001a98f010 \SystemRoot\System32\Config\DEFAULT
0xfffff8a0005fd010 0x0000000022eb3010 \Device\HarddiskVolume1\Boot\BCD
0xfffff8a0009f5010 0x00000000227ca010 \SystemRoot\System32\Config\SOFTWARE
0xfffff8a000f2b010 0x000000001f3c2010 \SystemRoot\System32\Config\SECURITY
0xfffff8a000fc1010 0x0000000000b5a010 \SystemRoot\System32\Config\SAM
0xfffff8a00107e010 0x00000000055cd010 \??\C:\Windows\ServiceProfiles\NetworkService\NTUSER.DAT
# volatility -f mem.raw --profile Win7SP1x64 hashdump -y 0xfffff8a000024010 -s 0xfffff8a000fc1010
Volatility Foundation Volatility Framework 2.6
Administrator:500:aad3b435b51404eeaad3b435b51404ee:1507e24d634a54c0b14750a7da2bdfdb:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:c22b315c040ae6e0efee3518d830362b:::
mumuzi:1000:aad3b435b51404eeaad3b435b51404ee:0606ac59df4a10d3a9e1f97b3612546f:::
# volatility -f mem.raw --profile Win7SP1x64 hashdump -y 0xfffff8a000024010 -s 0xfffff8a000fc1010 > pass.txt
Volatility Foundation Volatility Framework 2.6
# john pass.txt --format=NT
Using default input encoding: UTF-8
Loaded 3 password hashes with no different salts (NT [MD4 256/256 AVX2 8x3])
Warning: no OpenMP support for this hash type, consider --fork=2
Proceeding with single, rules:Single
Press 'q' or Ctrl-C to abort, almost any other key for status
Warning: Only 11 candidates buffered for the current salt, minimum 24 needed for performance.
Warning: Only 23 candidates buffered for the current salt, minimum 24 needed for performance.
Almost done: Processing the remaining buffered candidate passwords, if any.
Warning: Only 12 candidates buffered for the current salt, minimum 24 needed for performance.
Proceeding with wordlist:/usr/share/john/password.lst, rules:Wordlist
123456789 (Guest)
Proceeding with incremental:ASCII
...貌似没啥用……
看看命令行记录。
# volatility -f mem.raw --profile Win7SP1x64 cmdscan
Volatility Foundation Volatility Framework 2.6
**************************************************
CommandProcess: conhost.exe Pid: 1588
CommandHistory: 0x117120 Application: cmd.exe Flags: Allocated, Reset
CommandCount: 13 LastAdded: 12 LastDisplayed: 12
FirstCommand: 0 CommandCountMax: 50
ProcessHandle: 0x60
Cmd #0 @ 0x109cf0: dir
Cmd #1 @ 0x108290: ipconfig
Cmd #2 @ 0xf8bd0: ipconfig 192.168.26.2
Cmd #3 @ 0x116aa0: ping newsctf.top
Cmd #4 @ 0x1082d0: network
Cmd #5 @ 0x1082f0: net user
Cmd #6 @ 0xf8c50: net user Guest 123456789
Cmd #7 @ 0xf8c90: net user mumuzi (ljmmz)ovo
Cmd #8 @ 0x108350: clear
Cmd #9 @ 0x116a40: if_you_see_it,
Cmd #10 @ 0xf8cd0: you_will_find_the_flag
Cmd #11 @ 0x116ad0: where_is_the_flag?
Cmd #12 @ 0x1178d0: net user Administrator flag_not_here
Cmd #29 @ 0x90158:
Cmd #30 @ 0x10f920:
**************************************************
CommandProcess: conhost.exe Pid: 2824
CommandHistory: 0x357140 Application: DumpIt.exe Flags: Allocated
CommandCount: 0 LastAdded: -1 LastDisplayed: -1
FirstCommand: 0 CommandCountMax: 50
ProcessHandle: 0x60
Cmd #29 @ 0x2d0158: 5
Cmd #30 @ 0x34f940: 4当成 flag 交上去都不对。不信了。
再去搜一波文件。
# volatility -f mem.raw --profile Win7SP1x64 filescan |grep "flag"
Volatility Foundation Volatility Framework 2.6
0x000000003e4b2070 2 0 -W-rwd \Device\HarddiskVolume1\galf\fl^ag.zipesktop\fl^ag.zipp\vmware-mumuzi\VMwareDnD\9451fe4f\flag.zip
0x000000003fa56dd0 2 0 RW-rw- \Device\HarddiskVolume1\Users\mumuzi\AppData\Roaming\Microsoft\Windows\Recent\flag.lnk
# volatility -f mem.raw --profile Win7SP1x64 dumpfiles -Q 0x000000003e4b2070 -D . -u
Volatility Foundation Volatility Framework 2.6
DataSectionObject 0x3e4b2070 None \Device\HarddiskVolume1\galf\fl^ag.zipesktop\fl^ag.zipp\vmware-mumuzi\VMwareDnD\9451fe4f\flag.zip
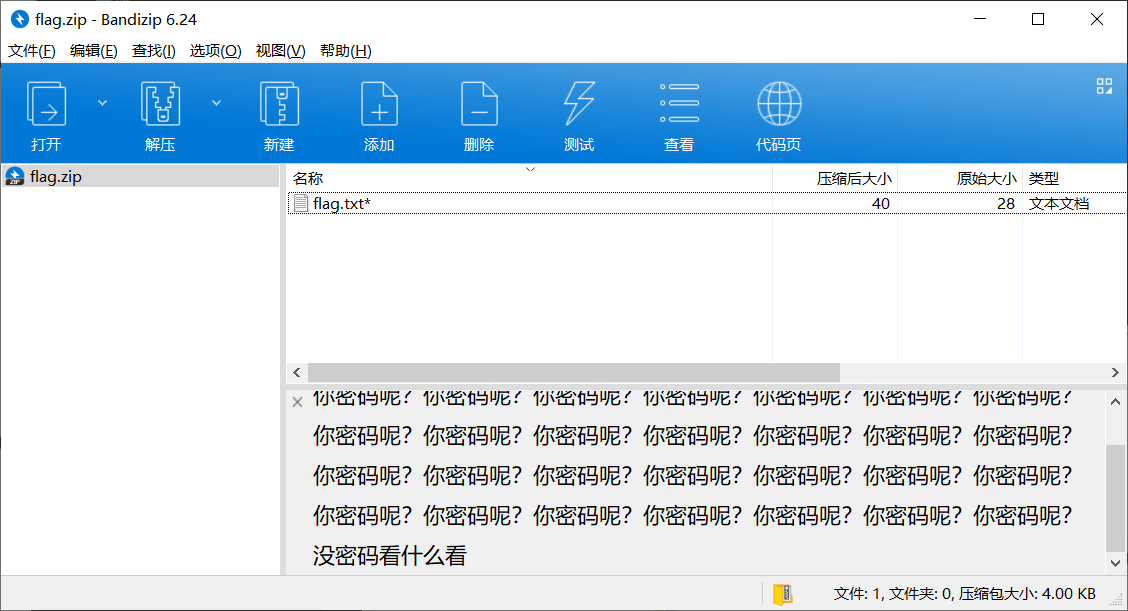
用 (ljmmz)ovo 作为密码解压,得到 flag。
flag{ez_di_imp_1t_y0u_like?}
Crypto
签到
Web
easy_web
签到题
题目地址:http://47.106.172.29:22221/
hint:这个图片真好看呀,没啥隐藏的东西吧
再也不信你们什么签到题了!!!
先把背景图下载下来吧。

提取出来个 zip
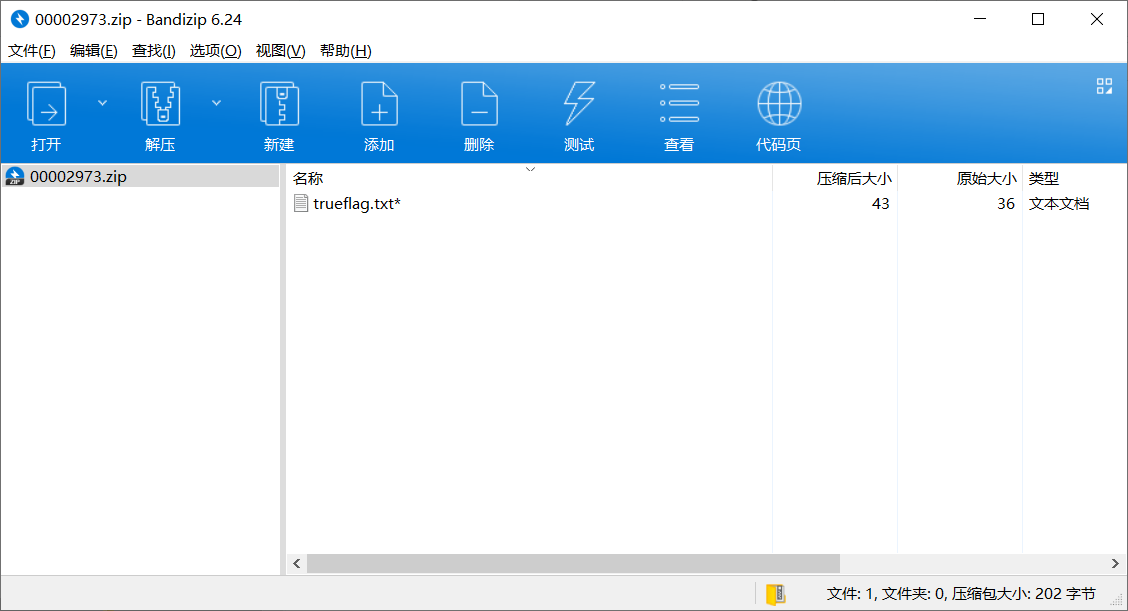
好家伙,看来网页上又有假的 flag。原来是 Misc + Web 啊。
网页上给了源码。
<html>
<head>
<meta http-equiv="Content-Type" content="text/html;charset=UTF-8">
<title>EasyWeb</title>
<style>
html, body {
margin: 0;
padding: 0;
width: 100%;
height: 100%;
text-align: center;
}
body {
background-image: url(backImg.jpg);
background-size: contain;
}
.content {
width: 80%;
text-align: left;
padding : 10px;
margin: 0 auto;
background-color: rgb(255, 255, 255, 0.7);
}
</style>
</head>
<body>
<h1>EasyWeb</h1>
<div class="content">
<?php highlight_file("index.php") ?>
</div>
<div class="content">
<?php
$six_number = $_POST['webp'];
$a = $_POST['a'];
$b = $_POST['b'];
$c = $_POST['c'];
if (md5($six_number) == 'e10adc3949ba59abbe56e057f20f883e' && md5($a) === md5($b) && $a !== $b) {
if($array[++$c]=1){
if($array[]=1){
echo "nonono";
}
else{
require_once 'flag.php';
echo $flag;
}
}
}
?>
</div>
</body>
</html>md5 e10adc3949ba59abbe56e057f20f883e 对应的明文是 123456,md5 相同而内容不同的话可以用数组绕过,即 a[]=1&b[]=2.
然而这个 if($array[]=1) 怎么绕过,咱两天里断断续续想着也没想出来……
最后比赛结束了才知道是数组 Key 整数溢出。
在 php 中一个 array 包含键 key 和值 value,当给一个未指定 key 的 array 赋值时,会自动给当前 key 赋值为上一个使用过的 整数 key +1(一个整数),如果没有使用过的话则为 0.
假如之前的 key 是个字符或字符串,那新的下标也就是 0.
另外 php 的 ++ 除了会给整数 +1 外,还可以给字符 +1,倒是字符的 ++ 有亿点怪,比如 z-> aa, Z -> AA, 1Z -> 2A, Zaf -> Zag, 3adAZ -> 3adBA, etc.
这里就不研究了,也不是这题关键(喵喵懵了,感觉得看底层源码才知道
而这里的最大表示数是 2**63-1,即 9223372036854775807,然后因为 if($array[++$c]=1) 做了自增处理,咱把 c 设为 9223372036854775806,当 if($array[]=1) 赋值的时候就会造成溢出,报错且判断不为真,从而能够拿到 $flag.
(感觉说的好乱啊,随意看看就好了
于是 Payload:
webp=123456&a[]=1&b[]=2&c=9223372036854775806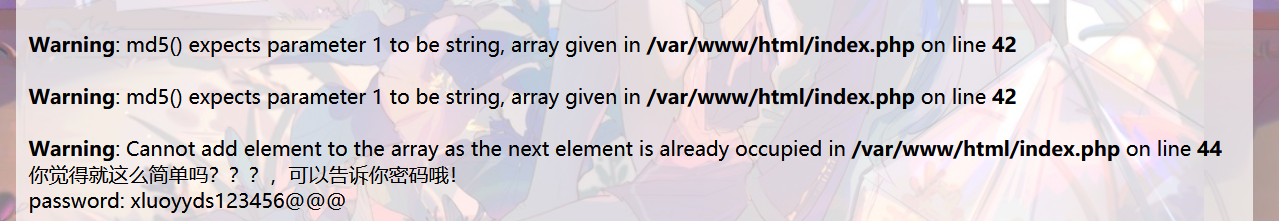
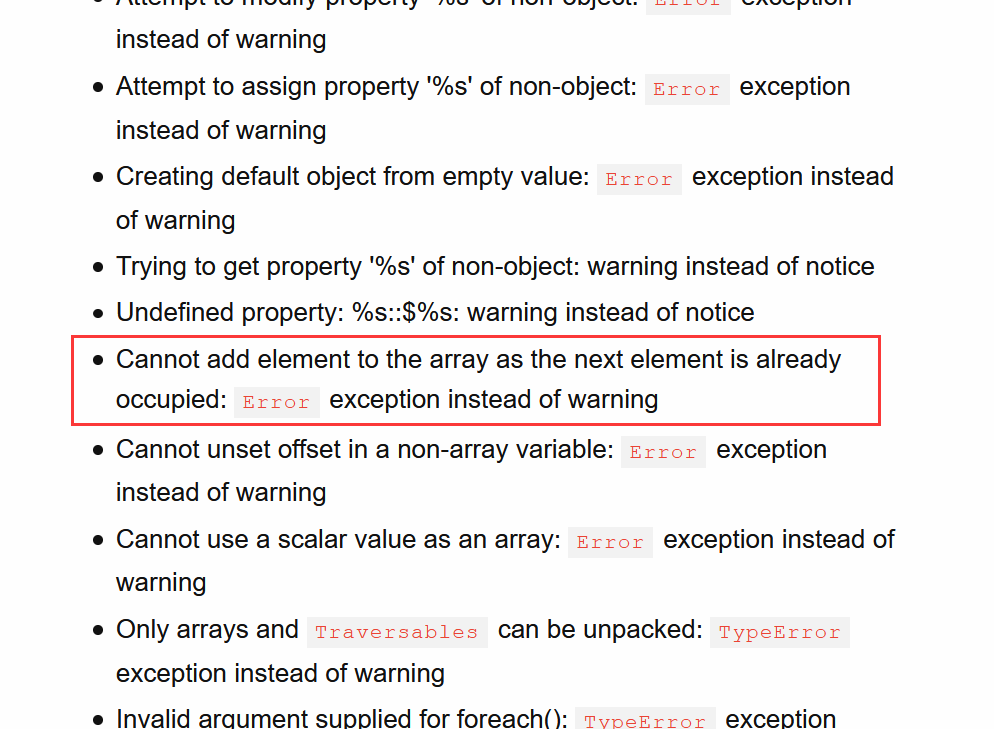
你看他这里报的错就是 由于下一个元素被占用而不能将其添加到 array 中。
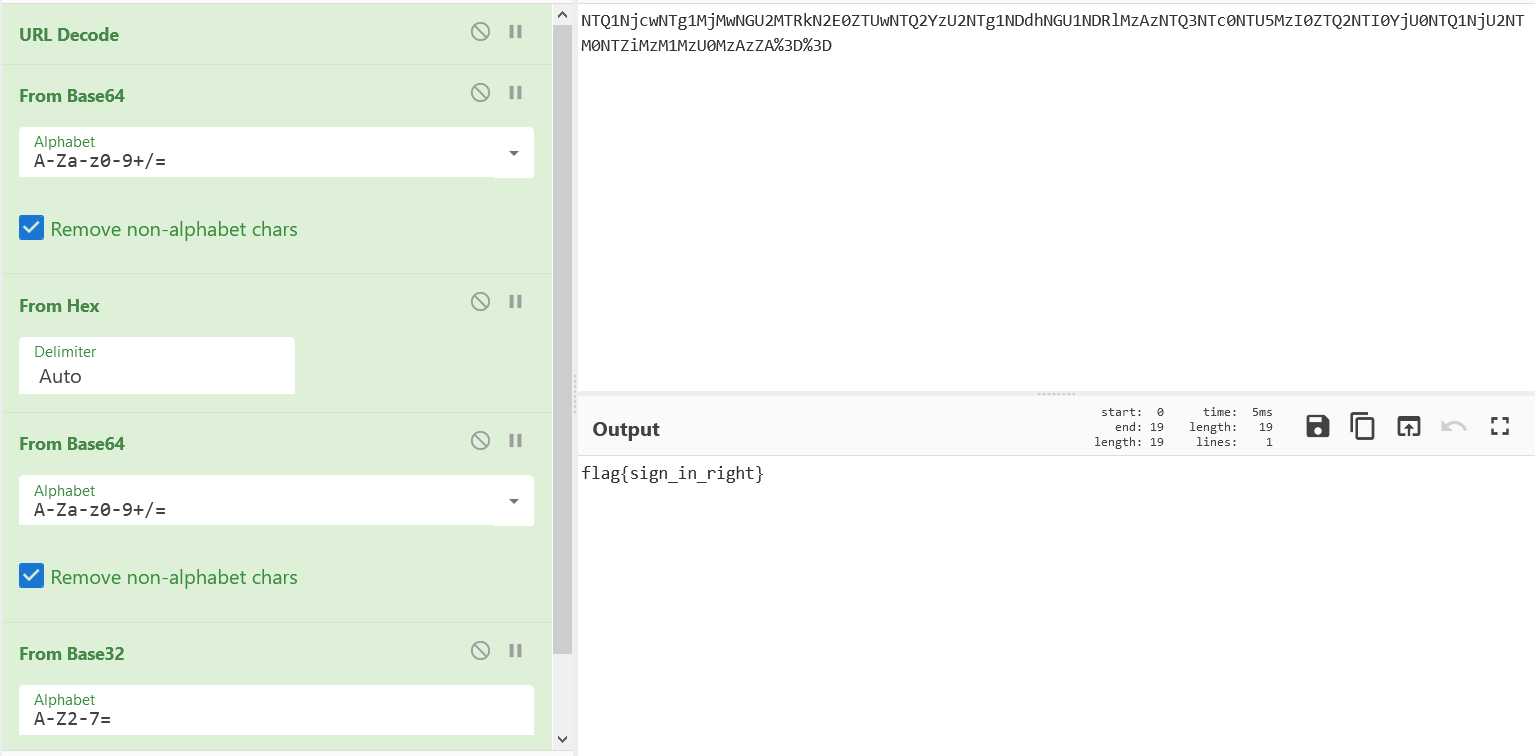
password: xluoyyds123456@@@ 拿去解压得到最终的 flag。
newsctf{this_1s_veryveryveryeasyweb}
去搜了一下
stackoverflow: “next element is already occupied” error
其实这题的
c就是赋值为PHP_INT_MAX -1.相当于在 PHP 里一个 array 最多能够表示的元素个数就是
PHP_INT_MAX了。然后又发现,在去年发布的 PHP8 里,这个 抛出异常变成 Error 了!
(安全性提升++
小结
其他有的题目还是有点意思的。
就先这样吧(摊手睡大觉
(溜了溜了喵