
引言
DASCTF May
2021年5月29日 10:00-18:00
这周末好啊,特别是5月29日真是个好日子,一堆比赛全堆在这天了……
比如 DASCTF May、春秋杯、XCTF final、DozerCTF,balabala。
几个比赛题目大概看了看,DASCTF May 这次比较基础(赵总貌似也说是为了测试 buuoj 的 matches 新模块),这里就随意写写当作做题记录好了。
Misc
Holmes
Do you know Holmes?

文件结尾一个 rar 压缩包
图片上是个跳舞的小人密码,参考下图。
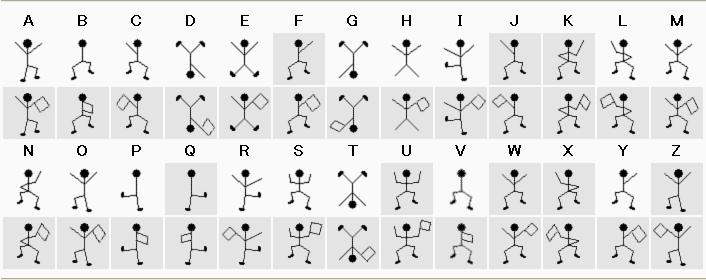
得到密码为 YOYAREHOLMES,然而并不对,根据意思应该是 YOUAREHOLMES
解压得到 flag.py
flag="flag{********************************}"
encflag=[]
for i in range(len(flag)):
encflag.append((ord(flag[i])+i)%128)
print(encflag)
'''
[102, 109, 99, 106, 127, 57, 60, 104, 60, 107, 61, 62, 65, 68, 115, 64, 67, 119, 66, 74, 73, 74, 119, 75, 74, 79, 79,
76, 78, 82, 78, 85, 83, 84, 82, 86, 92, 34]
'''逆着写脚本解密就好。
l = [102, 109, 99, 106, 127, 57, 60, 104, 60, 107, 61, 62, 65, 68, 115, 64, 67, 119, 66, 74, 73, 74, 119, 75, 74, 79, 79,
76, 78, 82, 78, 85, 83, 84, 82, 86, 92, 34]
flag = ''
for k, v in enumerate(l):
try:
s = chr(v-k)
except:
s = chr(v-k+128)
flag += s
print(s, flag)
print(flag)flag{46a4b3357e13f0755a42651250633038}
rickroll_u
we will rickroll you!(flag内容为字母数字组合,请MD5后提交。)
链接: https://pan.baidu.com/s/1JJ8AtqFJVFa6u9z7RKunPw 密码: nwld
压缩包明文解密,先把 ah_old_time.txt 以不压缩的方式弄成一个压缩包。
跑出来密码是 t!m32R1。
解压出来有个音频文件 rickroll_u.wav
好家伙,是那个理查德·艾斯利的 Never Gonna Give You Up,太经典啦。
文件结尾还有个 wav,手动提取出来。
发现是个 DTMF.
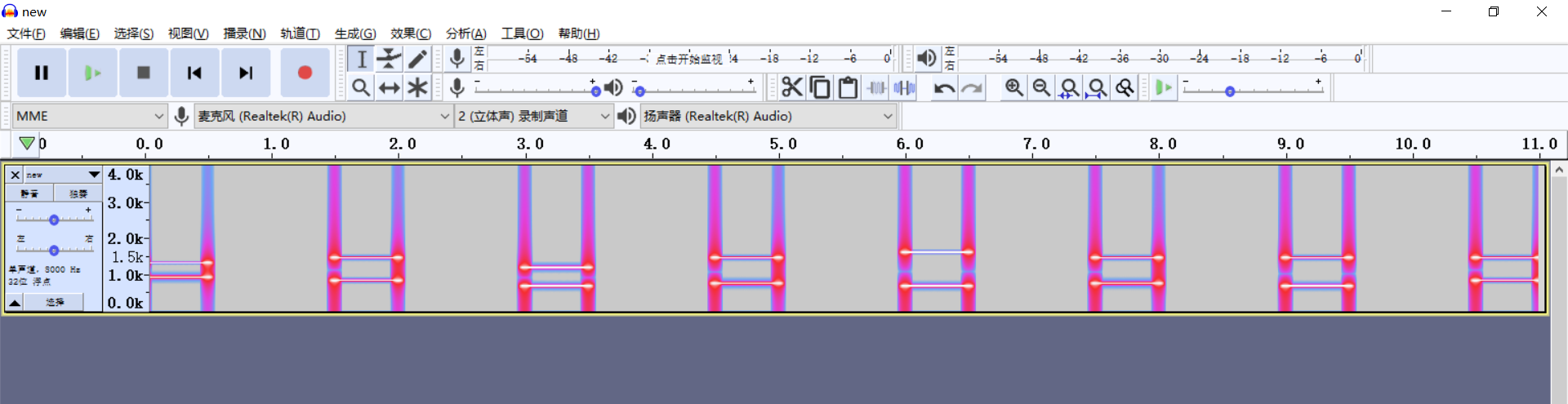
提取出来是 0916A639。发现 md5 提交上去不对。
最后发现字母是小写。。。0916a639
md5 => c8c15a11dd2852cbe63df405debc9d41
直接交上去就行。
DCT domain steganography & crack
hint1链接: https://pan.baidu.com/s/1obhR1KqUv2VCuyC0Qy62AQ 密码: t86j
这里有个 top 1000 密码
开局一张图……

DCT 域隐写的有好几个工具来着,给了个 top1000 密码应该就是用来解密的密钥了。
(感觉没意思,没往后做了,后来群里说是 outguess
sseddoG
下载下来是个流量包,提取出来有个Athena.png 结尾拼接了个 xml,里面有公钥和私钥。
<?xml version="1.0" encoding="UTF-8"?>
<ATHENA>
<TASKING>
<COMMAND_EXECUTE_TIMEOUT>10</COMMAND_EXECUTE_TIMEOUT>
<STATE_FILE_PATH>.\STATE_FILES</STATE_FILE_PATH>
<MAX_CPU_UTILIZATION>40</MAX_CPU_UTILIZATION>
<MAX_PROCESSING_DATA_SIZE>1000000</MAX_PROCESSING_DATA_SIZE>
<MAX_CHUNK_SIZE>0</MAX_CHUNK_SIZE>
<BATCH_EXECUTION_TIMEOUT>123</BATCH_EXECUTION_TIMEOUT>
</TASKING>
<INSTALL>
<RESTART_SERVICE>1</RESTART_SERVICE>
<TARGET_FILE_NAME>%SystemRoot
%\System32\Microsoft\Crypto\RAS\iprcache.dll</TARGET_FILE_NAME>
<ORIGINAL_FILE_NAME>%SystemRoot%\System32\iprtrmgr.dll</ORIGINAL_FILE_NAME>
<DATA_FILE_NAME>%SystemRoot%\System32\codeintegrity\ras.cache</DATA_FILE_NAME>
</INSTALL>
<UNINSTALL>
<KILL_FILE_PATH></KILL_FILE_PATH>
<DEAD_MAN_DELAY>0</DEAD_MAN_DELAY>
<BEACON_FAILURES>0</BEACON_FAILURES>
<DATE_AND_TIME></DATE_AND_TIME>
</UNINSTALL>
<BEACON>
<BOOT_DELAY>0</BOOT_DELAY>
<DOMAINS>10.3.2.56</DOMAINS>
<PORT>443</PORT>
<JITTER>0</JITTER>
<USER_AGENT_STRING>Mozilla/5.0 (Windows NT 6.3; Trident/7.0;
rv:11.0)</USER_AGENT_STRING>
<ACCEPT_STRING></ACCEPT_STRING>
<INTERVAL>5</INTERVAL>
<TASKING_DELAY>0</TASKING_DELAY>
<PROXY_PORT>0</PROXY_PORT>
<HIBERNATION_DELAY>0</HIBERNATION_DELAY>
<ACCEPT_LANG_STRING></ACCEPT_LANG_STRING>
<IE_PROXY_ADDRESS></IE_PROXY_ADDRESS>
<URL_PATH>/octopus/</URL_PATH>
<ACCEPT_ENCODING_STRING></ACCEPT_ENCODING_STRING>
<WPAD_PROXY_ADDRESS></WPAD_PROXY_ADDRESS>
</BEACON>
<CLIENT_KEY>
<PUBLIC_KEY>-----BEGIN PUBLIC KEY-----
MIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAmN9l2LF50PqlGXwwk4Ai
nAKHLyd5dpDVr9G7LqD2pi492zzIA9hgU2a+kLoV3+/VMbrI+Y0mp707Gifz9PB1
mABAdppeTQyYyE9+KmnAjg1WuI/HDtMrfqzkXh8m4p2u1o8sWIOfFUpZxK1H5TMT
DicdJ3UJ3NNkP3asIxFWRXNmQ2tdINtmViJufotE7lj9gCDRleZsm0Io8t12b90h
Tgd+aqKCRumIgdnOm6VW4dsHzClyAYaxz0JCpxBQffJ9rWRlPklkUJw5WrC8YoCb
hdO7p3ZdizcDgazDC1/G4lwmvWC7v7c1PAeMX5DBkov4MwbX4aYQRqX5nxkegZOI
pQIDAQAB
-----END PUBLIC KEY-----
</PUBLIC_KEY>
<PRIVATE_KEY>-----BEGIN RSA PRIVATE KEY-----
MIIEowIBAAKCAQEAmN9l2LF50PqlGXwwk4AinAKHLyd5dpDVr9G7LqD2pi492zzI
A9hgU2a+kLoV3+/VMbrI+Y0mp707Gifz9PB1mABAdppeTQyYyE9+KmnAjg1WuI/H
DtMrfqzkXh8m4p2u1o8sWIOfFUpZxK1H5TMTDicdJ3UJ3NNkP3asIxFWRXNmQ2td
INtmViJufotE7lj9gCDRleZsm0Io8t12b90hTgd+aqKCRumIgdnOm6VW4dsHzCly
AYaxz0JCpxBQffJ9rWRlPklkUJw5WrC8YoCbhdO7p3ZdizcDgazDC1/G4lwmvWC7
v7c1PAeMX5DBkov4MwbX4aYQRqX5nxkegZOIpQIDAQABAoIBABjaCFaH04PTm09f
Tw5LgFTYXF2gDzDlLrfcYo+b/zzYu5mOcf2eCVrFkyk39yJmfMQO12kqNySBsL/5
ysEA7jz9nX0qbzYbXCMEOUBv3Ku7I2Pxi6yvS5zWQnHCorGobKnYsJ7bFtuBMMK2
YL+z498jIKwvbKEHhH6ErkstIFc9wQnl635zYLE3EywbD4ktyDholdfBFyTCwk1J
Gd/holAwGN78PldVc+K73m8E2Jo3VnN7TGOG7Fb5CS19xj7zcIE4cubhEH+w6RMU
Ra592NjSd2iZEW5xjugIbTThmLbFOXaBioeXVWstW9VRzgTIfb3TlcssLtzZoAje
0c9wrgECgYEAxvwc9hlEY8VABtoVrxxY7NtqRUh3B8jeKW4eCP8Ri0DiH9eYHL9R
pJSBP///vWcOt4EBfvb1krp7HJgh/5bJlewuuEtR4WbFfqgfwLPbKjKE0D6TVQyk
AH4egcplynKqSdDwQvlghpqya69YmTx+S7qawr3aTUJ2Zvl/ldzrKEECgYEAxKzg
OOLOJu5QHB3MPaE9HKcxU+xir2j0rCNyUOtN9dVXg/wdWOabatGfdhPa2xmgzlPc
QzqLW5ZnIITjXYZIx7uctP2i5dhDm7NycthrTzykT7owHbMHX6Ey6qvup4K6EzwL
uCKD7XoAz7ImfQvv6e2BYYhIqUfvQFAuitj652UCgYAUlSF9x1FOrKmZy9cwXNNJ
9MxCTGObl4h7apuKvK+Y4uZA+vEOEDAmwQG5mAZhFhbsnliERJFUUxvG8mmZ4YQK
kPqoL4pRsWq+Vi+qpDAIZl9clwxwYLVaI7GOJVxwG3pH1mfz1Y3Jfpj0EJguiZZa
yPuXJ0I8eaJ7tlUfMFHWwQKBgEIHD9fJPRCQ3VAzKMhgA1ZFQyg7qf3drJbF57EG
7ktj7lefInMgKHk6GuDXVZhNCFF8kev4EaUT31dphbN2S6TSdY/FvxSPAFObcQbh
ZVVatIcXqOOvoQAX7DIguqR+HN4sQHr3C3eEiBUyZ/1/LnJIjDEkQdCjF81tndJ7
efCJAoGBAJ3sgwKQUSdKhiduyok/qJ0Ye5EgJGuskUIsLeLVnShzYrAAUVJMIpLK
OLXC8ygMyAp9gpusnS5obQjUKaB7livuqQ3OKEUvm9tyJbjMLfJoMGry7wjj0eiI
F3OCoV5LfjIfAldn/k2KGGR6/LM1K2vi/wCo1wuHHwpWbndJwqF3
-----END RSA PRIVATE KEY-----
</PRIVATE_KEY>
</CLIENT_KEY>
<SERVER_KEY>
<PUBLIC_KEY>-----BEGIN PUBLIC KEY-----
MIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAmN9l2LF50PqlGXwwk4Ai
nAKHLyd5dpDVr9G7LqD2pi492zzIA9hgU2a+kLoV3+/VMbrI+Y0mp707Gifz9PB1
mABAdppeTQyYyE9+KmnAjg1WuI/HDtMrfqzkXh8m4p2u1o8sWIOfFUpZxK1H5TMT
DicdJ3UJ3NNkP3asIxFWRXNmQ2tdINtmViJufotE7lj9gCDRleZsm0Io8t12b90h
Tgd+aqKCRumIgdnOm6VW4dsHzClyAYaxz0JCpxBQffJ9rWRlPklkUJw5WrC8YoCb
hdO7p3ZdizcDgazDC1/G4lwmvWC7v7c1PAeMX5DBkov4MwbX4aYQRqX5nxkegZOI
pQIDAQAB
-----END PUBLIC KEY-----
</PUBLIC_KEY>
<PRIVATE_KEY>-----BEGIN RSA PRIVATE KEY-----
MIIEowIBAAKCAQEAmN9l2LF50PqlGXwwk4AinAKHLyd5dpDVr9G7LqD2pi492zzI
A9hgU2a+kLoV3+/VMbrI+Y0mp707Gifz9PB1mABAdppeTQyYyE9+KmnAjg1WuI/H
DtMrfqzkXh8m4p2u1o8sWIOfFUpZxK1H5TMTDicdJ3UJ3NNkP3asIxFWRXNmQ2td
INtmViJufotE7lj9gCDRleZsm0Io8t12b90hTgd+aqKCRumIgdnOm6VW4dsHzCly
AYaxz0JCpxBQffJ9rWRlPklkUJw5WrC8YoCbhdO7p3ZdizcDgazDC1/G4lwmvWC7
v7c1PAeMX5DBkov4MwbX4aYQRqX5nxkegZOIpQIDAQABAoIBABjaCFaH04PTm09f
Tw5LgFTYXF2gDzDlLrfcYo+b/zzYu5mOcf2eCVrFkyk39yJmfMQO12kqNySBsL/5
ysEA7jz9nX0qbzYbXCMEOUBv3Ku7I2Pxi6yvS5zWQnHCorGobKnYsJ7bFtuBMMK2
YL+z498jIKwvbKEHhH6ErkstIFc9wQnl635zYLE3EywbD4ktyDholdfBFyTCwk1J
Gd/holAwGN78PldVc+K73m8E2Jo3VnN7TGOG7Fb5CS19xj7zcIE4cubhEH+w6RMU
Ra592NjSd2iZEW5xjugIbTThmLbFOXaBioeXVWstW9VRzgTIfb3TlcssLtzZoAje
0c9wrgECgYEAxvwc9hlEY8VABtoVrxxY7NtqRUh3B8jeKW4eCP8Ri0DiH9eYHL9R
pJSBP///vWcOt4EBfvb1krp7HJgh/5bJlewuuEtR4WbFfqgfwLPbKjKE0D6TVQyk
AH4egcplynKqSdDwQvlghpqya69YmTx+S7qawr3aTUJ2Zvl/ldzrKEECgYEAxKzg
OOLOJu5QHB3MPaE9HKcxU+xir2j0rCNyUOtN9dVXg/wdWOabatGfdhPa2xmgzlPc
QzqLW5ZnIITjXYZIx7uctP2i5dhDm7NycthrTzykT7owHbMHX6Ey6qvup4K6EzwL
uCKD7XoAz7ImfQvv6e2BYYhIqUfvQFAuitj652UCgYAUlSF9x1FOrKmZy9cwXNNJ
9MxCTGObl4h7apuKvK+Y4uZA+vEOEDAmwQG5mAZhFhbsnliERJFUUxvG8mmZ4YQK
kPqoL4pRsWq+Vi+qpDAIZl9clwxwYLVaI7GOJVxwG3pH1mfz1Y3Jfpj0EJguiZZa
yPuXJ0I8eaJ7tlUfMFHWwQKBgEIHD9fJPRCQ3VAzKMhgA1ZFQyg7qf3drJbF57EG
7ktj7lefInMgKHk6GuDXVZhNCFF8kev4EaUT31dphbN2S6TSdY/FvxSPAFObcQbh
ZVVatIcXqOOvoQAX7DIguqR+HN4sQHr3C3eEiBUyZ/1/LnJIjDEkQdCjF81tndJ7
efCJAoGBAJ3sgwKQUSdKhiduyok/qJ0Ye5EgJGuskUIsLeLVnShzYrAAUVJMIpLK
OLXC8ygMyAp9gpusnS5obQjUKaB7livuqQ3OKEUvm9tyJbjMLfJoMGry7wjj0eiI
F3OCoV5LfjIfAldn/k2KGGR6/LM1K2vi/wCo1wuHHwpWbndJwqF3
-----END RSA PRIVATE KEY-----
</PRIVATE_KEY>
</SERVER_KEY>
<SOURCE>
<FLAG?>TheyWereBelieversInTheGoddess</FLAG?>
</SOURCE>
<TARGET>
<CHILD_ID>0xABCD0064</CHILD_ID>
<DYN_CONFIG_TYPE>0</DYN_CONFIG_TYPE>
<PARENT_ID>flag</PARENT_ID>
</TARGET>
</ATHENA>另外还提取出来个 Top_secret.zip,解压出来一个 client_secret.dat,里面是
<data>
6945004599188163993695415369835695903301224003136994252560594956191090963121611565339316899123749651980866032846579298200421747380583546633355992903073674181349057044030322829788264132202636849376954935277228938532451604402772829242424577058024238656161078439246537271516326863255516855631753446705292842229626286876548916801469642547513456705866784202623394305276451128865785358297012288872815722144655832856702699498675579782594166664458814522864775862036884859354259378908758433643337060342583622920263235497780709801069090899910257671959718315799533292405361650450010152269010240983236777594133358567962307235569
<sign>
2657375403899004421682435875591648757169751001935445937761677813563331237751296771655965799410203548200444843121899114276425174188686046977514392352233441829494629361400810323413751538449142557000621910082199277027187814332458889139635831754705831808451385798544850324418189973193940364270700678684371080465070928269782397410454121628205746311654719735981174781630012234885865191874665887323338400055601894791632973447395440378983992188376105785566869556895986983889219094640854379267584790389009829385657891279182819588524435817909919666674804622368593843455996806164859962400637898116212711639490474051288221345806应该是数据和签名,拿密钥去解密应该就好了8
(后来去看其他比赛题目了……
小结
这个比赛比较基础,适合拿来摸🐟。
随便玩玩就好了,相对而言还是大一点的比赛题目质量更高一些。
(溜了溜了喵


