前言
安恒月赛,2020年DASCTF——四月春季战。
比赛时间:2020年4月25日下午13:30-17:30
比赛平台:https://www.linkedbyx.com/studyCenter/36998/tasks
请提交flag{}/DASCTF{}括号里面的内容。
今天下午有个 DASCTF 安恒月赛,四月春季战,难度据赵师傅说“雨露均沾”,就来看了看题。
其实还是大概比赛开始之后一两个小时才注册的,于是划了个水,大概看了几道 Re 和 Misc 的题,随便写写 WP 吧。
(其实也没几道题会做的,有的还是赛后补的,呜。
Reverse
入门reverse
题目附件:在这里
拖进 IDA 看下。
int __cdecl main(int argc, const char **argv, const char **envp)
{
size_t i; // [esp+28h] [ebp-80h]
char v5; // [esp+30h] [ebp-78h]
char v6[8]; // [esp+A0h] [ebp-8h]
_alloca(0x10u);
__main();
std::operator<<<std::char_traits<char>>((int)&std::cout, "input your key: ");
std::operator>><char,std::char_traits<char>>(&std::cin, &v5);
for ( i = 0; i < strlen(&v5); ++i )
v6[i - 112] = (v6[i - 112] ^ 6) + 1;
if ( !strcmp(&v5, "akhb~chdaZrdaZudqduvdZvvv|") )
std::operator<<<std::char_traits<char>>((int)&std::cout, "yes!you are right");
else
std::operator<<<std::char_traits<char>>((int)&std::cout, "try again");
system("PAUSE");
return 0;
}A0h-30h 正好就是十进制的 112,于是 v6[i - 112] 对应的就是 v5 的地址。
Exp:
# -*- coding:utf-8 -*-
s="akhb~chdaZrdaZudqduvdZvvv|"
new=''
for i in s:
t=(ord(i)-1)^6
new+=chr(t)
print(new)flag{daef_wef_reverse_sss}
哇好耶,好久没看到这么简单的 Re 题了唉!
encrypt3
题目附件:在这里
同样拖进 IDA。
signed __int64 __fastcall main(__int64 a1, char **a2, char **a3)
{
__int64 v3; // rax
__int64 v5; // rdx
__int64 v6; // rax
__int64 v7; // rdx
__int64 v8; // rax
__int64 v9; // rdx
char v10; // [rsp+17h] [rbp-49h]
int v11; // [rsp+18h] [rbp-48h]
int i; // [rsp+1Ch] [rbp-44h]
int j; // [rsp+20h] [rbp-40h]
int k; // [rsp+24h] [rbp-3Ch]
__int64 v15; // [rsp+28h] [rbp-38h]
char v16; // [rsp+30h] [rbp-30h]
char v17; // [rsp+31h] [rbp-2Fh]
char v18; // [rsp+32h] [rbp-2Eh]
char v19; // [rsp+33h] [rbp-2Dh]
char v20; // [rsp+34h] [rbp-2Ch]
char v21; // [rsp+35h] [rbp-2Bh]
char v22; // [rsp+36h] [rbp-2Ah]
char v23; // [rsp+37h] [rbp-29h]
char v24; // [rsp+38h] [rbp-28h]
char v25; // [rsp+39h] [rbp-27h]
char v26; // [rsp+3Ah] [rbp-26h]
char v27; // [rsp+3Bh] [rbp-25h]
char v28; // [rsp+3Ch] [rbp-24h]
char v29; // [rsp+3Dh] [rbp-23h]
char v30; // [rsp+3Eh] [rbp-22h]
char v31; // [rsp+3Fh] [rbp-21h]
char v32; // [rsp+40h] [rbp-20h]
char v33; // [rsp+41h] [rbp-1Fh]
char v34; // [rsp+42h] [rbp-1Eh]
char v35; // [rsp+43h] [rbp-1Dh]
char v36; // [rsp+44h] [rbp-1Ch]
char v37; // [rsp+45h] [rbp-1Bh]
char v38; // [rsp+46h] [rbp-1Ah]
char v39; // [rsp+47h] [rbp-19h]
char v40; // [rsp+48h] [rbp-18h]
char v41; // [rsp+49h] [rbp-17h]
char v42; // [rsp+4Ah] [rbp-16h]
char v43; // [rsp+4Bh] [rbp-15h]
char v44; // [rsp+4Ch] [rbp-14h]
char v45; // [rsp+4Dh] [rbp-13h]
char v46; // [rsp+4Eh] [rbp-12h]
char v47; // [rsp+4Fh] [rbp-11h]
char v48; // [rsp+50h] [rbp-10h]
char v49; // [rsp+51h] [rbp-Fh]
char v50; // [rsp+52h] [rbp-Eh]
char v51; // [rsp+53h] [rbp-Dh]
char v52; // [rsp+54h] [rbp-Ch]
char v53; // [rsp+55h] [rbp-Bh]
unsigned __int64 v54; // [rsp+58h] [rbp-8h]
v54 = __readfsqword(0x28u);
v16 = 38;
v17 = 44;
v18 = 33;
v19 = 39;
v20 = 59;
v21 = 35;
v22 = 34;
v23 = 115;
v24 = 117;
v25 = 114;
v26 = 113;
v27 = 33;
v28 = 36;
v29 = 117;
v30 = 118;
v31 = 119;
v32 = 35;
v33 = 120;
v34 = 38;
v35 = 114;
v36 = 117;
v37 = 113;
v38 = 38;
v39 = 34;
v40 = 113;
v41 = 114;
v42 = 117;
v43 = 114;
v44 = 36;
v45 = 112;
v46 = 115;
v47 = 118;
v48 = 121;
v49 = 112;
v50 = 35;
v51 = 37;
v52 = 121;
v53 = 61;
v3 = std::operator<<<std::char_traits<char>>(&std::cout, "Please input your magic number", a3);
std::ostream::operator<<(v3, &std::endl<char,std::char_traits<char>>);
std::istream::operator>>(&std::cin, &v11);
if ( v11 <= 9 )
return 0xFFFFFFFFLL;
v15 = operator new[](v11);
for ( i = 0; i < v11; ++i )
std::operator>><char,std::char_traits<char>>(&std::cin, i + v15);
v6 = std::operator<<<std::char_traits<char>>(&std::cout, "You have input sth.", v5);
std::ostream::operator<<(v6, &std::endl<char,std::char_traits<char>>);
v8 = std::operator<<<std::char_traits<char>>(&std::cout, "I will mix them with the enc_flag!", v7);
std::ostream::operator<<(v8, &std::endl<char,std::char_traits<char>>);
for ( j = 0; j <= 37; ++j )
{
v10 = 0;
for ( k = 0; k < v11; ++k )
v10 ^= *(_BYTE *)(k + v15);
putchar(v10 ^ (unsigned __int8)*(&v16 + j));
}
std::operator<<<std::char_traits<char>>(&std::cout, "\nMaybe you have found the `flag`\n", v9);
return 0LL;
}是 Cpp 唉。虽然逆向出来有点丑emmm。
大概意思是先让你输入一个 magic number,如果v11 <= 9则返回 -1 退出,说明输入的数要大于9。
然后依次输入v11个数,存到v15及之后的空间内。
后面输出了一个 enc_flag。重点就是这几句嘛。
for ( j = 0; j <= 37; ++j )
{
v10 = 0;
for ( k = 0; k < v11; ++k )
v10 ^= *(_BYTE *)(k + v15);
putchar(v10 ^ (unsigned __int8)*(&v16 + j));
}
std::operator<<<std::char_traits<char>>(&std::cout, "\nMaybe you have found the `flag`\n", v9);正好前面那串数字就有38个。看来起始的几个字符为 flag。
v10依次和输入的每个数异或一下,再输出v10和最开始那串数字异或的结果。
逆向的话,只要找到 flag 就完事了!
于是直接爆破好了!
Exp:
输了几个数字觉得太麻烦了,于是直接正则匹配好了。
import re
s = """
v16 = 38;
v17 = 44;
v18 = 33;
v19 = 39;
v20 = 59;
v21 = 35;
v22 = 34;
v23 = 115;
v24 = 117;
v25 = 114;
v26 = 113;
v27 = 33;
v28 = 36;
v29 = 117;
v30 = 118;
v31 = 119;
v32 = 35;
v33 = 120;
v34 = 38;
v35 = 114;
v36 = 117;
v37 = 113;
v38 = 38;
v39 = 34;
v40 = 113;
v41 = 114;
v42 = 117;
v43 = 114;
v44 = 36;
v45 = 112;
v46 = 115;
v47 = 118;
v48 = 121;
v49 = 112;
v50 = 35;
v51 = 37;
v52 = 121;
v53 = 61;
"""
t = re.compile(r'v\d{2} = (\d+);')
result = re.findall(t, s)
# print(result)
l = list(map(int, result))
print(l)
# [38, 44, 33, 39, 59, 35, 34, 115, 117, 114, 113, 33, 36, 117, 118, 119, 35, 120, 38, 114, 117, 113, 38, 34, 113, 114, 117, 114, 36, 112, 115, 118, 121, 112, 35, 37, 121, 61]得到一系列的数字,转换为字符串。上面用了 map,下面这里用用生成式的写法,嘻嘻。
而后先找出flag对应的v10,再用它来异或就完事了。
l_str = [chr(x) for x in l]
s2 = ''.join(l_str)
print(s2)
# &,!';#"surq!$uvw#x&ruq&"qrur$psvyp#%y=
for i in range(10, 100):
tmp = chr(ord(s2[0]) ^ i)
if tmp == 'f'or tmp == 'F':
print(tmp, i)
# f 64
# F 96
final = ''
for x in s2:
final += chr(ord(x) ^ 64)
print(final)
# flag{cb3521ad567c8f251fb1252d03690ce9}得到 flag:
flag{cb3521ad567c8f251fb1252d03690ce9}
Misc
(签到题)6G还远吗?
5G都来了,6G还远吗?6G下还需要开会员才能高速下载吗?请提交 DASCTF{} 里的内容。
http://server.zhaoj.in:8888/1GTest.file or http://das.wetolink.com:8888/1GTest.file
文件大小显示是 977MB,然而下载速度慢到 1KB/s 不到,还不允许多线程……
想到估计是假的文件,毕竟是签到题,应该不难的。(才不像上个比赛假的签到
于是按下 F12,就看接收到的这部分 payload 好了。
或者就接收一部分然后截断也行。
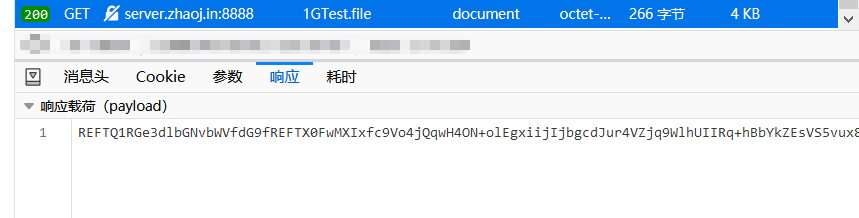
REFTQ1RGe3dlbGNvbWVfdG9fREFTX0FwMXIxfc9Vo4jQqwH4ON+olEgxiijIjbgcdJur4VZjq9WlhUIIRq+hBbYkZEsVS5vux8bVmJVja6tNhXfCd6yA5ENaNdd71StufW73yWPvhDqb1CdPjqBjCCnbLVGqRkulvFFUZv6z7MllCQgkZhjm57ueMkPj28eSMymY4JLjYZ/bSPGkclsK1ySI+M/sn6QxLdKJhAvR4tVLHHrjdJBMPSRO52CAur7r5FEXCkjMEisOrAL9qufae0FV+iOGZAsH4cxJ0sMNSlNnX1Lso+6IlT0mj9QC+yRbQzsfZ4Bww/SMOLuWcosCLiQYtJRaG9tJiiR/R7vjRf5egHyBph1eVwMGA0puUvI8jXz9mdn08kfP2XxnB5CUdkhK2RIwJPwu+egKygfG+WeJihIa0eepB83Zvty/NUTpuPjmIS+DdS2yzYAc7IhdGNEbQpW5wG2zpNZDDS3l2E5YDAfF7oEyVFEE8CSB17sgzdCMzKgwbQhFU0o0260e2w53CvPHIvm/zlYgJC8pzj+cnGiM07VZ4Hw0CAeYwn9s1M1F2u4KTDQs+QnDrtMtc1yHBkkwjnDtV2VNZhWqK4fEwunu1i0cuWvdyPE5USj6+9ON2mfFCSxwaqRo++niZT5XDcsSKSEgKn4iO8tSt3uBH3YyimubWNNGzcnxPMRNGt+O6E6hzD1zKxZr/dRDQobygI6GZRGLHOQltIiiB6kkIUKeUM2tHBlKahmrBGDtJWfoXJ36aWV86+DEXGe/riFkCtMxn4u4OsDkXpRBr6/xYqMQh1gJIYqwG2e8D0OOTVsy505NXas9fLnhPM5FAdamkTwjsXmoK/9uKcQ1OC+s2xaSbB0B5QgEuxNAAcQDPft4rfo01PAgMb8N4F8NhVpLpLBrgu5FETKNiZb+j1HyRozIUCcDPhDKkWmgjMo9Pt9TIB+4iob6SwiJlY5lE5rPqr80eBMalZ9n2xl6DMAva75f9YYNVNLZ8fk5hl4ktO/WRBMX/f9z+q3YTsSS5lPgsQDv2lxbpNeRiJVyyirbSoBBJIK+ogMUbq5zxnBbWVFaeozIX2DA3J71G40+9JuHhXhN5mmXni910FhfSz2NBai7Oa2TWPcA0o8ug+CYsIPjvSzsEstMM+/ETpOLVhp+EKF47LT2h8uoZOi3y11BaNTyp03EVQYR/nkKqZz+BGPxb73BZEgVKahNQ2srFH8vYNHsDIrz2By4JXWbeeCx5zIZydorLfjVqEA12tmYcf7wcUoZGWLd/lAUDhP3itj4OiqwWdmyDsA5LNW7nzszELZlyiZJs/9zrAo13mK09Ih6dUbya8vmik4doSx3uH2FjB4zDUG9oxgrywTg+7PHYILSF/FGnMSZ9TiU/7icb0S5rAY7HpTJDgBWRGLhHiiiQVhuqtbEiax2KmgXBDeW4fs6DP/OChg36uBseoyoUGi0NVRloweGIWzVdPbhMw6YgXLMicln+KMNzgougS7QqgG9pvDWS6r46Ly9COwYoUGRGI50li4+c/rA0Y3CKA6W56GwFep/ozNQm7rmy+sP/lpOsTYN8TyCig2FuWnY7BQgk4iCiaTwY4MSBMR+7b/nhRQyBD4oANhmTWlwkjozt8VdPE+sWvNA2oy1GfhlbSNZImeU9xnPd0ZY7UoH5bXqIEhxSaMWUD09SOXWq14ku+QJs5iDiaGKnpG02oXPHTHxvMp4ib2VqZl8goSrbbiQsEDbRNKTfYyeIkLDNwlwhDgBlrQY6XuwlKFR6ws6MYefI8TxjkHrSDNkYj1eXmrELc612d31EUGcgityyt/Ge5uC+cz85jOBkgYkkeSQfP9/zSDVqbBK86oDVo/sFjdtKAwDwvX0Z8ZGKDRsyPIA2pY1Y5pXunMPSUEV/PcSD5R0fhKcWSLWQgkr3PsbXP9tEcu9IcBqyh0ZN5auFweQDh7XEM8U9sPlQKLGh9mS4m13VqSkzhRx6oeTDpPSAr9jFypxnsToNuJggYlnnsR2e7aVszPB0cK+z2lq/Rw69ta5S4UEQEE67v/bepkIZGN1j0Zs812cjq0HBwLCcRDwNnu9OsdveHOQeS0h2GFdehsPRCv3PGntda6es18I4XDO6T3CKxBIamstOlnwa1dY5f/rcIXNrJ57ljSk4zyHRQb/Gn5aGW/lmwkYYDQBQCRqwjv9L7CCjvg+RKwoo0ypgCPJA4sdKRQcd7fofnYdIldtA4N0hGReP83jmjXpsFJPGewnQw+y5KUyMYuF/iTTngBiN8Qm1437t8wRg9GJK3cM+5T5Tg908XJY9KMwjM24FbmitNBTXFR1nG3kRenmKZrMWW1SzuAFjhBsk5f0ztECgtvWa7SjA6qd03pbg/bxqYd5KVbE0KhbTZ7/LEf2FDwR6mXSy+ejNLl4088E++rVJj9FmLcAcbug3Qsz9ihRthxxEWYC0MffUC7N6hk5asRIm1J33vui7NVsGzKCpgZ33nkRieY0A1a5WJKoPfD8b9j6R8wLfk9CIIzXL+e/i2usCoqTXYD//J3DkUzB4oSgffdiCgNtEAj541qVYp1JIHA0F3FZ86g4lDGz429Tcgv7aA+mUBqdib05LqFZxgEeFOTZ5uqoKOI6+b+6wXm12+DbsCfesY4/bMtF3mHY+sPSEr/00U77OunBI3hLNxAtndhgRguL7H57iDypYQLq2IE4KSxe5nKz2lQoKrPHtUO/4lVOqyqvm7n4ITwCAaQ6JPHWMKbR1ZARyVdnzcZ9GFJTWJoqs7WhAk9PvNsskUPk8kWB3wP6EusOO9uUImSp/HvfUdU89/ik001/BSHedhDKLZEJltA32tjEbsuv4PLQKtdlhTL5dt/QR5CmkESCvOJsv4MyJXmGcww4LWtCjmxcwoSUXCY2n8yl3f9Bv1PRariIkyr6Rc/QZgIaO+rdM21GJEiNyb2TNs5Cm0lupCvm+u6/PR+pHxtHsoxZzMQvcNo9rfg/kjbCT2Gx/5W5MKFWOQSwf45Xwbtsxb/q1sOTP/7HILeuYgyh7qWRySGry9jjVXMR/XMlMnqPAiax6+uHNcaGESQUMow5i6tJEh/nWawF5DJls7G8LNqpGTLkr1mv6qOh+EmLpxOygrKhMgaCbGKRz/KbPzSLrZgRsCUEmMbe9CQXJNa7gy7raZADwpK8dRygbIaDm/RC4qDllAgQe9kH3lyuPkYxIoodev/fISYr8U23JQ8P1XU3ps7URTz0AAWkBaz6K/uyMiv3zgMqzhkYXgEZ2ihGc51P7+t8KTxyO/3cAoQ6bGL2x69TAu4rK2BM6dSKDgpSPQOeCRXANOTvM/Znz1E1mKLZz6r4U+Ts6nLLDiic+vt3fWCSIrKxYhF6viSnJ4uVFjAZkGhZPs+fTjJqjW55drSF1YxvngSAjxn8FNICvkVD9KCqrWfkprYAEOhicQ6htz+ctYv/8MO9FcxxKycXNw3LIf4ih9abb7BON/zEXM0Y6WIxDNZVP2PWvqYnBi6w1kPeCueTrneLUESTjvvCjcVx8uDpWi5h9N3jRGmCfRTNijEtZIRU6ra6f+6rH5b5fsF9LeGXNLRvHiIcEfgi6Bk6u2epsXO0joJPwCoJd5ZKp3YixjHjUrnvMm+W9VTAiHE0UIX+5D1CUEDcBbmsc8C+De9SwIRXmH+p+67n6rkHNxvctoHDXh/RNbXr6Tsbu24fMjkBJYT/9wkACRMauOx+rPK1NUuc2WDCyWZbXc8JEw3zzgN1w1yfmElTce6v7ahOy1A+n1lKUEmso30mmrAkU1Fzh1loFpxWiFXVbmr5Ct7xH1knCAJf4wDEkvfSawHCVuLYXuVs/WfzPn3VcNz2CUFvVCZRgnusv0F41PVVB75H5uNmEL6z3bsKgrfGzbyiuyCbcXe+X5UCr2WWfzEmFpqNwfaLD64GOTIxkRGY2n7VfkiccJzN3sefkCcPxaunfRq3xnKgxWgrwcdMAync/ZJwwYV7e0Jg0HlOIARGVd5/kRFZKbIpBfO95d5XTeLUNFtCOD9JqzC0WGBZCsyRkFFR6SjfV2yajwPG7ZSD4ExtDtvvPII7/PTtDdSD38MREg4E9oV6eE4bdj6aL0wM0e2RoJmGNKDb7kg8yd+pt1t2Gw1nz1oYbUyZX/yH647dX/ION+g7NIAOghn2udo8pb4ph8ZHOg+TVz8fkBcu7fVlAEeR/xRhFe5AuYglqzhYqPF1ezC+iDOo3H4TN/9etWpm6FN4wBUrMptqVrwpUQx5Vv1Y0v2KG91O8Y691FNdc8zS5UhYmZnWROsLfFTEGGTbhWFxjav09qE+IIXjIP25qqISZjq3qyCNo4P2zQHF/V4U/ym3h7RrvLimDRQ9ftga81VcMSOLIaFwnitN9myKNn/H0uMqTBdfdWFmt1gexY4x92WxXd8Yoj5v7uOjnGIoEfkORt8P7x3Ld4YnAOtcrHbZsX/PUa1i1clmn0Nj3rnJYbJPnxt+chH6UHzj0pvgdVuaBnUgILZktkF8HWE2HJ2KKMVOSwtjpNshsRH6VXqjQY+QGa1UpQWhkFIdjV7YH3COxHFZlb44Siajiy5jJ0+t8eSEsflmQ9kL9KoXCuz1/5QkVFvN5hYldQLBx5VkG3jCWD12XCR/uga6Ia0e8mV+1xiRHvJLaSfyxRIch5durhoW4VfM0lv60SQA2YmQuGhZbIX1isc7lauBLZQc5hNg00RYnyuTs9d/rFfmTnTNbUM77aq4HWtL0Idi4f94ENqOmi4TwAQRIQQQlPoqTvlLKOfbMM6YCnDiKiXIsT7wTHru67LAZ6VqSQ72ScgH3R7jHNAwBf7WUj2xfpdh/BhOTkkyf3SRXS4kn7Mh3nmJFTuKj/R5eiwrKJvbi6Xwtp5gWWNxzpGCrn6ShX6imDaT15t9bWOudaxZO2q4URzJWrB+t2GDvWjaLD9zTrfNmLXVsPJ7hOazcY7kYVPqbGnY2Zz7GzfydCWpK0fyChWo289oBuUpSqHKFoEkOI1t28wRP6VoAeXrXRKUavUK4494iEDVlBgq0z5/QDzzpiJEcahVCGB3vQDwYVKJpofx6V+4065qJ+zyxKZ1VRlKJ/KmWEUivbB5clFCHbvUKIy9K0XJQa7v+jarC03jxyIEYe82l9ziBcUKN3zGx+LoPHgJ40zM4vJf8ebiIKz6/cz2qNtVMGbR4la4rqAA9UJGPGuKU8i0UXDI2TFy3KjHqnPpZ+9yfeEV/V4Ly8WmPZPQyqEhXTXha8IGY9JlNZrjWWC+DqzsKmZJl8bSnmPWNimglQun/HhUHXpOvCm4tflKx0RmVasAa0L7wSb1qJNJf6Brekh0KaDy+8NQVUshR3XE90YnYdiAT5qy15hVM6wsB/7e/iTors5kaUJD35MTfbL1rrDufx6MZBs/WmerQ6vy20J4wwnNkCxllhWH4TI/DRh3OJzkG0AA3A==扔去 base64 解密,就可以得到 flag。
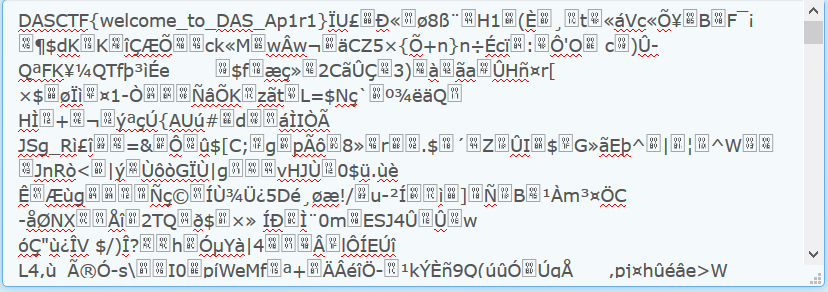
果然 flag 就在文件最开头哈哈哈~
DASCTF{welcome_to_DAS_Ap1r1}
blueshark
Can you dig something you want out from the sea-colored beautiful shark?
题目附件:在这里
一个流量包,看了是蓝牙协议,呜又是没见过的。发现 Wireshark 还可以分析蓝牙数据包唉。((其实好多都可以
binwalk 发现了一个 7z 的压缩包,直接当成压缩包打开,发现有个 password_is_Bluetooth_PIN.txt文件,看来得找 PIN 了。
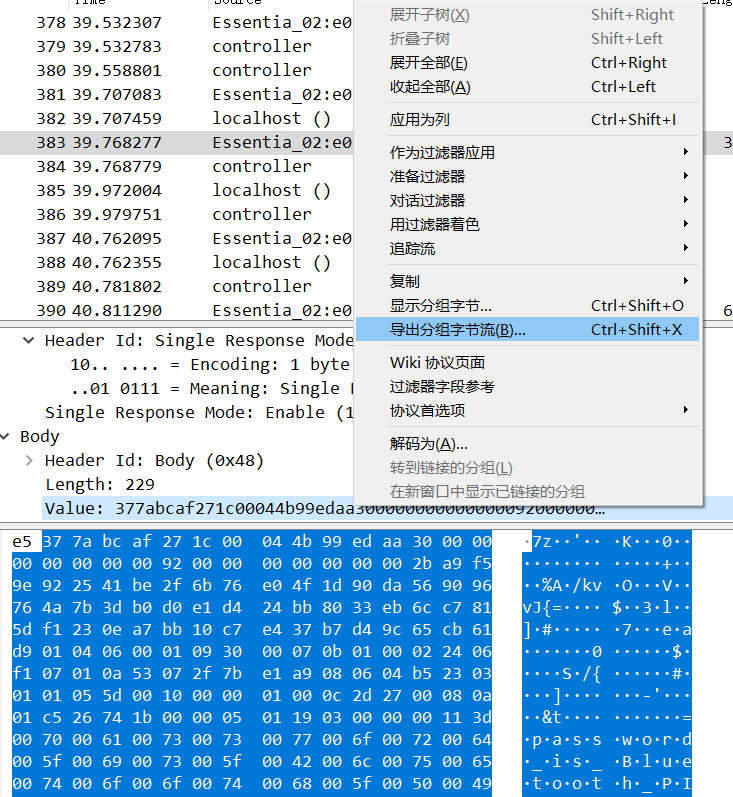
从数据包这里也找到了这个压缩包。
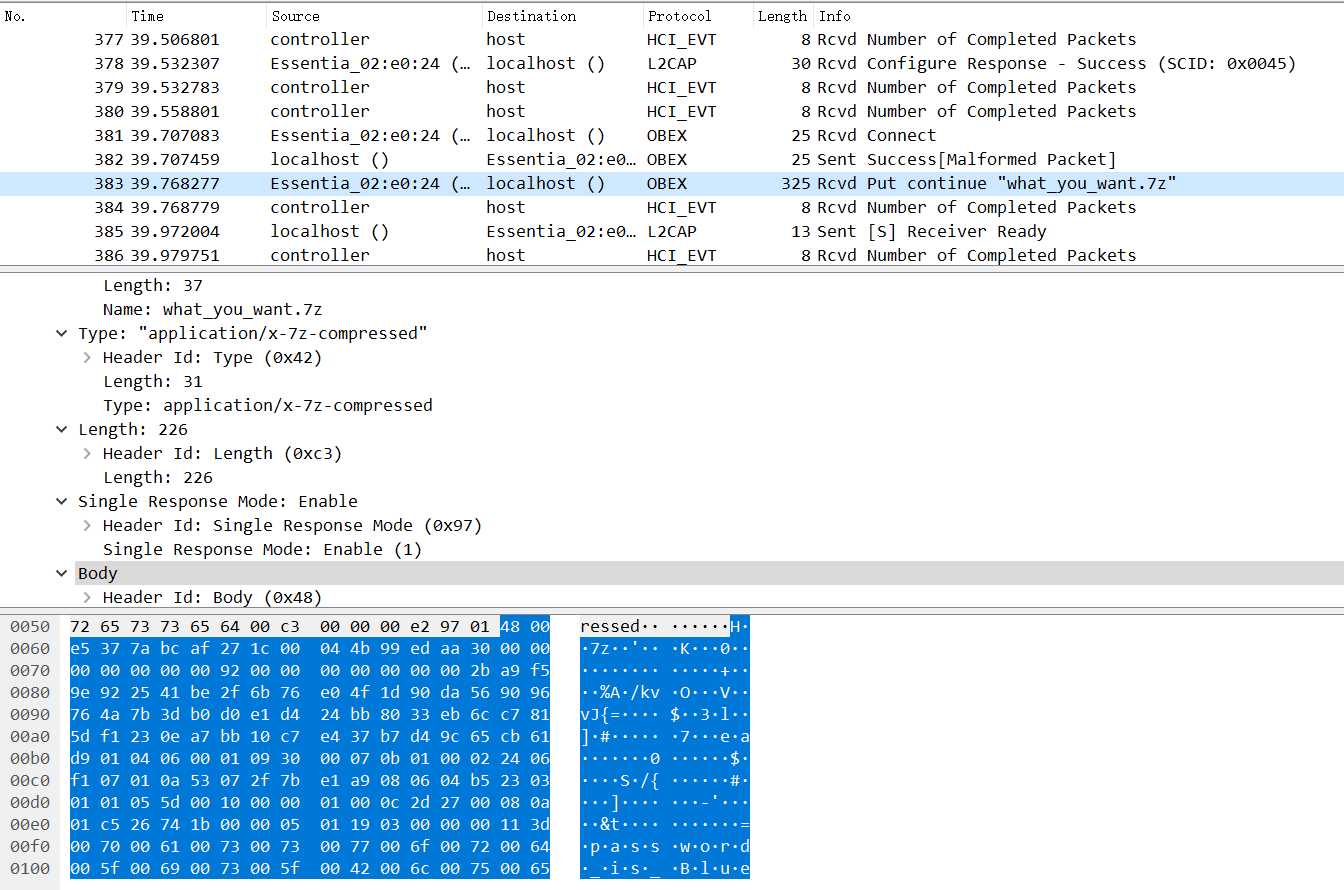
本来以为 PIN 就是4位的,还想爆破一波。。结果发现不是。
后面大佬说是在网络流里可以找到 PIN,emmm?
噢,Ctrl + F,选择 分组详情 或者 分组列表,字符串 或者 正则表达式,这样搜就找到了。
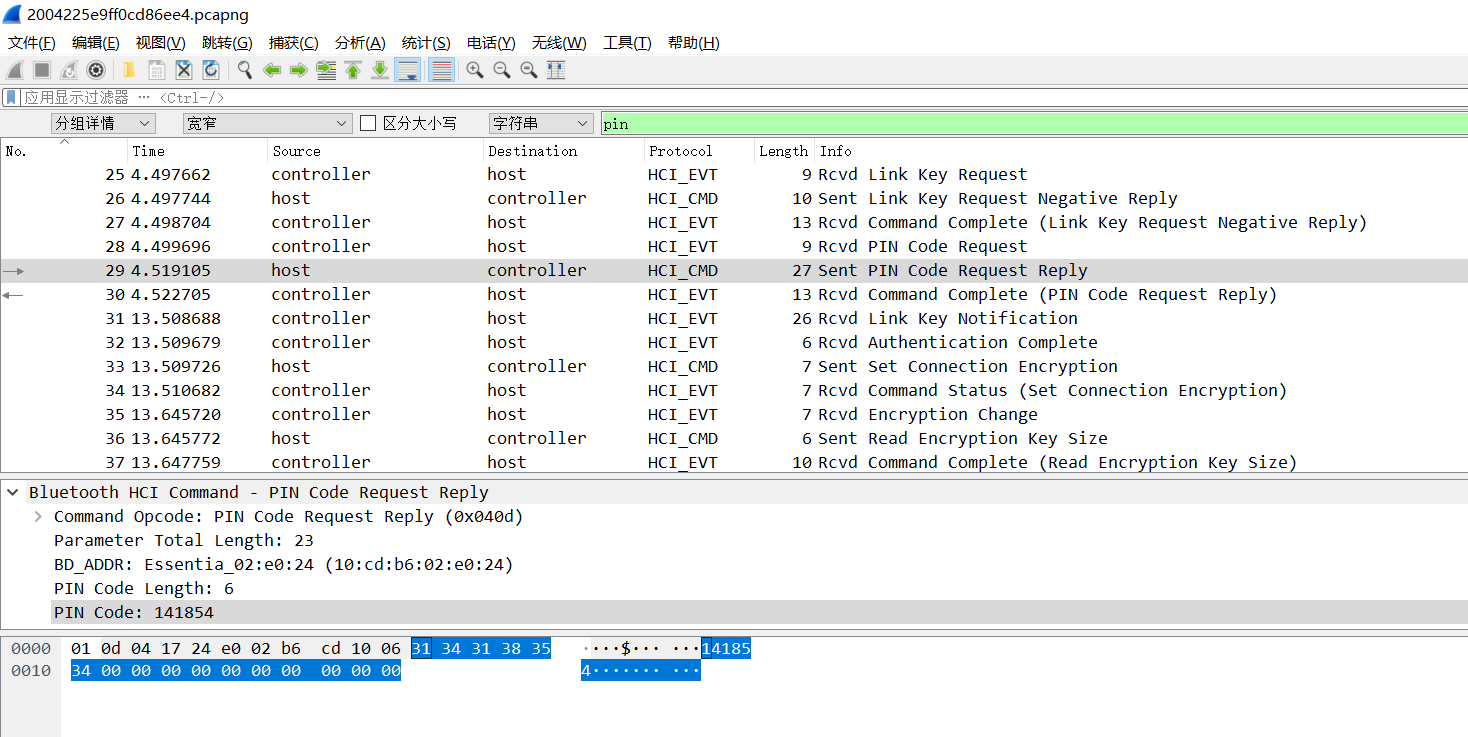
PIN 就是 141854。
用来解压就可以得到 flag。
flag{6da01c0a419b0b56ca8307fc9ab623eb}
导出这个压缩包可以先选中,再
Ctrl + Shift + X导出分组字节流。而后保存到文件打开就行。
后面有空再了解一下内存取证什么的(这次好像有一题
题目版权归官方所有。
以上内容仅供学习研究使用,请勿用于非法用途。
好像这篇有点水唉(先不管了
周日还要补周一的课呢(
(溜了溜了