前言
这几天玩了玩杭州电子科技大学的Hgame2020,还别说,有点意思2333。
平台网址:
Flag格式:hgame{.+}
20200125 更新:
官方WP地址:https://github.com/vidar-team/Hgame2020_writeup
MISC
签到题
Li0tIC4uLi0tIC4tLi4gLS4tLiAtLS0tLSAtLSAuIC4uLS0uLSAtIC0tLSAuLi0tLi0gLi4tLS0gLS0tLS0gLi4tLS0gLS0tLS0gLi4tLS4tIC4uLi4gLS0uIC4tIC0tIC4uLi0tbase64解码得到
.-- ...-- .-.. -.-. ----- -- . ..--.- - --- ..--.- ..--- ----- ..--- ----- ..--.- .... --. .- -- ...--
一看就是摩斯电码,加入分隔符后解码得到flag
W3LC0ME_TO_2020_HGAM3
在线解密摩斯密码 www.atool9.com/morse.php
壁纸
解压得到图片Pixiv@純白可憐.jpg,foremost提取得到一个zip压缩文件。备注提示 Password is picture ID.
本来还以为是在图片的文件里,而且还找到了一个id属性,然而并不是。
上网查了一下純白可憐,发现是P站画家,看了一篇介绍原来每张图片有个编号来着。
试了试百度搜图,出来的画风有点不对劲emmm。干脆直接上P站搜,然后在页面上找到了这张图。

(还别说,挺好看的哇,还是个中国画师喵。
天意 https://www.pixiv.net/artworks/76953815
得到ID 76953815,作为密码解压flag.txt(这么短还全数字,其实可以暴力破解的),得到
\u68\u67\u61\u6d\u65\u7b\u44\u6f\u5f\u79\u30\u75\u5f\u4b\u6e\u4f\u57\u5f\u75\u4e\u69\u43\u30\u64\u33\u3f\u7dUnicode啦,转ASCII(用的是NATIVE转ASCII来着)得到flag
hgame{Do_y0u_KnOW_uNiC0d3?}
克苏鲁神话
明文攻击得到了解密后的zip文件。
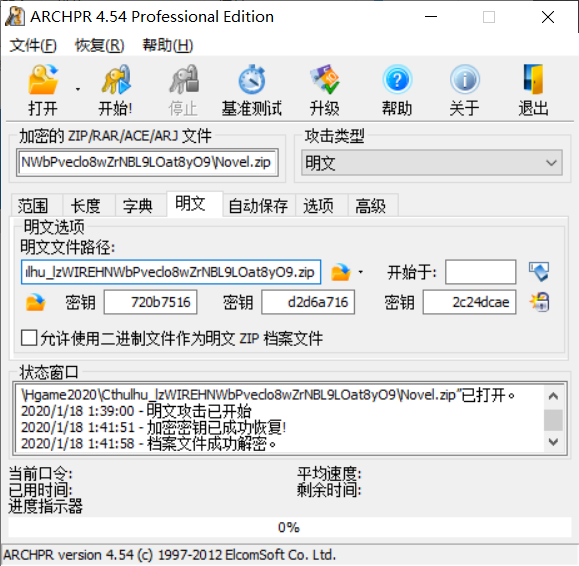
得到加密的 The Call of Cthulhu.doc文件。根据 Bacon.txt文件提示寻找密码。
of SuCh GrEAt powers OR beiNGS tHere may BE conCEivAbly A SuRvIval oF HuGely REmOTE periOd.
*Password in capital letters.然而不成功,不知道怎么做下去了嘤嘤嘤。
>>> s='of SuCh GrEAt powers OR beiNGS tHere may BE conCEivAbly A SuRvIval oF HuGely REmOTE periOd'
>>> s1=[i for i in s if i>='A' and i<='Z']
>>> s1
['S', 'C', 'G', 'E', 'A', 'O', 'R', 'N', 'G', 'S', 'H', 'B', 'E', 'C', 'E', 'A', 'A', 'S', 'R', 'I', 'F', 'H', 'G', 'R', 'E', 'O', 'T', 'E', 'O']
>>> ''.join(s1)
'SCGEAORNGSHBECEAASRIFHGREOTEO'20200125 更新:
看了官方WP才知道Bancon指的是培根密码,我还以为是咸肉/熏猪肉来着。。
根据大小写转为a或b,比如小写为a,大写为b。
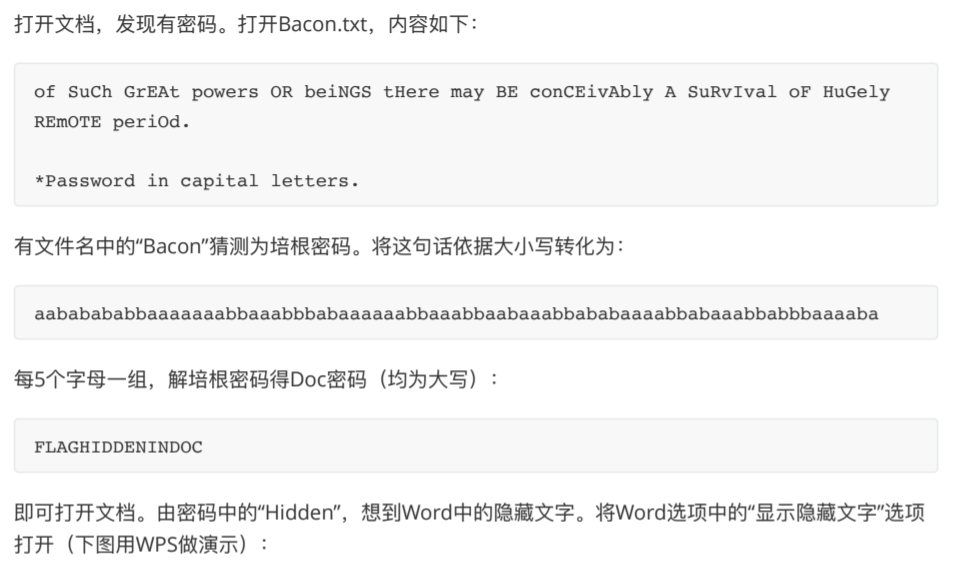
flag隐藏在最后emmm
Ctrl+D把隐藏取消掉就看到了。
hgame{Y0u_h@Ve_F0Und_mY_S3cReT}
签到题ProPlus
Password.txt提示了
Rdjxfwxjfimkn z,ts wntzi xtjrwm xsfjt jm ywt rtntwhf f y h jnsxf qjFjf jnb rg fiyykwtbsnkm tm xa jsdwqjfmkjy wlviHtqzqsGsffywjjyynf yssm xfjypnyihjn.
JRFVJYFZVRUAGMAI
- Three fences first, Five Caesar next. English sentense first, zip password next.
一开始还以为前面的是3个栅栏,后面的是5个凯撒,然后试了半天都不对。
突然一想应该是先栅栏再凯撒,一试果然。
先解密zip密码:栅栏得到JFARZGFVMVRAJUIY,凯撒得到密码 EAVMUBAQHQMVEPDT。解压得到 OK.txt。
同时上面的那句话同理解密得到
Many years later as he faced the firing squad, Colonel Aureliano Buendia was to remember that distant afternoon when his father took him to discover ice.
emmm不大理解,不管了。
看文件是Ook!编码,解密得到base32编码。
data:text;base32,NFLEET2SO4YEWR3HN5AUCQKBJZJVK2CFKVTUCQKBKFIUCQKBIVCUGQKZIFAUCRCPINCW6S2BIFAU6V2VNRCVCVSSGRXE6MTBKM3DIRKOO53UIMZPGB3DOV3ZINJVOOCHMNCTQ33LMJFXEQKPHBQSW3CBKNLC6MRTIFAUIKZVMM4WIQKBIRVWOQ2FIF3UCY2NIFIUCK2ZIFTUCOCBIZCECSKBKBDUCSKBMZGUCUKBJ5AUI2DHIFAUQN2ZJU2GKL3WNIXWINBQM5CTANJZOZHG2YLYLJQW6L2KMIYXGM3YJMYFIVRWK52G25LNMFYGMYKZF5GFUMKRHF3TMY2WLBQXC4DNOVLVO4KQPFLTSYSOHBJXIRJRMVWHEWTSOBWXCWBSNVIHSMTEKVIGGT3OIZLDE4LRLJZGY3DRNI4GY5SXPJTEK4SSJZMHAYJSME3FU4LMHFYGUODUNZLEIM2EOB4FMZDROFWWCNK2MFXS6STCGFZTG6CLGBKFMNSXORWXK3LBOBTGCWJPJRNDCUJZO43GGVSYMFYXA3LVK5LXCUDZK44WETRYKN2EKMLFNRZFU4TQNVYVQMTNKB4TEZCWJ5FU66BRNRXHON2OJRAXGVLVOR5HGTCJMJ3XMNLNFNVUE2SDFM3XC3LHPFCVKTLOGBUE2WKUGNSFKMCIKF4WQ2ZLNNFGSQ2PF5ZG2ZZWI5KU22RQNBRVCUJTORRTCSCRPFUGWT3LJRUVGRZYOIZHGNSHIVEWQMDYMNJVCM3IMYYTGULXNBCUW3KMPFJUOOCMGZ2TMV2BJFUFK6DGKNAXU2DGKYZVIR2XHBEXCULUGBIXAOCPPJLEU6BXKVRDGRCPKI4WI2LEJZDGMYKFKBUDEYLQMVGGC2TFGRNHSUDWONKHA33RG5AWYOKPNJJEY6DCKVRDGVCPKE4TS3LEJZDFQWKFF5YDAYKKMFFWC6TFGZNHSRDWON5HI4DROJAW4OKPNZIUYQSYLBRG4VCQKFHDK3TEHFFFKWKVF5XTANSGLJFXCN3EGZFDMQTWJUXXK4CLNZBW45CDNZITOTSVLBGHMUSQKFHDK3RZGFFFKNCVHFXVKK2ILJYW2NDEOFHDOQTWJEVXKNKPNVBW45CDNZ3TOTSVNZEHIUTWMNGTKSBRGJFDAMCWHFXVCK2ILJYWYNDUOFHDO2DOJEVSW6CPNVUXC43VNM4TC6TUKJDGGMTJNVZEMODEJQZVMTZSGMYTESRQGBLFM5BSNZHW2ZTRN5VGWMCVHFQXM2TQMM3HAKZQFN2TKT3NINYXM5KVGUYHUZDEIVRW22LOOJLDQZCMNZSE4MTOHEYUUVJUKZLDSNTOJ5WWE4DPIRZTEVJZMF3GU4DDGVYHKOBPOVYEW3SDOF3HIVJVGB4GITSJMRWXS5TSKY4FMTDOORHDC3TEHFFFKWLEKY4XC3SPNVGHA4CEJUZFQOJWNZUXAYZZOJ2XG6TUOBYXERDRKB2FKNKVPBTE4322NV4WM3SXHAYUI3DUHE4W2ZCOIZLFSZC2F5YW4S3NJQ2XIQSNK5RDQNSYOVYWG5DWOZZVI4DPOFZEY4CQMRRTOVKSLBHG64DRPBTEQUZZGFKHI5BZMRUWITSGKZRGI4D2OBXDM4KJGVHEMUCXOI2DMWCPOFTHIUDSOVKHAZ3SOI3HMTKXPBUDSSZWJY2WSQ2CNJBVGTKZMZJXK2TFLFTWOWLXNNVEOSBQOJXTG3KJJFDU2SSJPBUDSSZWJY2WSQ2CNJBVGTKZMZJXK2TFLFTWOWLXNNVEOSBQOJXTG3KJJFDU2SSJPBUDSSZWJY2WSQ2CNJBVGTKZMZJXK2TFLFTWOWLXNNVEOSBQOJXTG3ZUGNUEOULDM4YG6MKOIRMGIZCTKZZG6UKSIRFUCUSEOFAU4RDRIFDEIS2BKJCHCQKOIRYUCRSEJNAVERDRIFHEI4KBIZCEWQKSIRYUCTSEOFAUMRCLIFJEI4KBJZCHCQKGIRFUCUSEOFAU4RDRIFDEIS2BKJCHCQKOIRYUCRSEJNAVERDRIFHEI4KBIZCEWQKSIRYUCTSEOFBUQYKFI42TKM2ZJZ4UOSLDPFLHESTNOQ3XU5DFKNFHK2TCNFYHGWDCNJFVOTLMMEZWETBSGU2G4NDUMFEW26DQOJHDKNDZKZZEU3LUG55HIZKTJJ2WUYTJOBZVQYTKJNLU23DBGNREYMRVGRXDI5DBJFWXQ4DSJY2TI6KWOJFG25BXPJ2GKU2KOVVGE2LQONMGE2SLK5GWYYJTMJGDENJUNY2HIYKJNV4HA4SOGU2HSVTSJJWXIN32ORSVGSTVNJRGS4DTLBRGUS2XJVWGCM3CJQZDKNDOGR2GCSLNPBYHETRVGR4VM4SKNV2DO6TUMVJUU5LKMJUXA42YMJVEWV2NNRQTGYSMGI2TO3RZOBTHOQ3TMN3WYYSVGUVW4VDQIFTCWQTVNNKWWSDXINDUCTRZIEZVGS2TIR3UERDHI4VWOYTIJBFEENCBNB3UIZCROQ2GU22BHBAVCNCCOVXVOMCUPFAVOQKJHBATGVKMKNGDKQKEIFCSWQLCOFDHARRYIFBGOQ3GIFHDC2JQM4VUCQLXIJ3HISBLOAVUUMSZLFRGYU2GGFQWYN3CMRSWU2DJJJSTSMRZGU3HI2CTJBMSWMKUK42WK2CUK5NHG2SWOZFHKZBLF5NFO2DJIN3FKOLMLBMTIK3MMJKTKWLJLB3GI5TFMVZFSVLIGJIHIVJROVMG6VJRNVRESMLCPFRG4ZTWGJLG6WLHOIYVAWSWGJHVA4CXGFHVOSLMG4ZWEM3OOEZEMSLENI3VMTTCNQ3EMTS2NV4U4VZYNU2TGNZZNRQUOSKLHFKDEVTENJVDMVTUKRWGSSTFHEZDSNJWORUFGSCZFMYVIVZVMVUFIV22ONVFM5SKOVSCWL22K5UGSQ3WKU4WYWCZGQVWYYSVGVMWSWDWMR3GKZLSLFKWQMSQORKTC5KYN5KTC3LCJEYWE6LCNZTHMMSWOBUVCMKEI5UWQWLUHFDEEY3FNZKDGMCKGFIG4VCOKZZTOVLXNBFDSSKYKRJVQSDUGA4WIT3EKQ2TA6SWMJBTATJUKNSFGRRYGJWFEM3DKAZWM3SVJ5LE2MKXO52EIK2JNZKVEWCQOAYGIMKEMR5DKML2NRKE4MLTJFIWM2KKGEYFM6BWMRIGMULOKUVWITJRK55HIVCDIVXDA2DEJZFGGZJTKQYTANJRKBXFITSWONGFC6TIJIYUSWD2MFLEQZDXF5SCWZCRGVKXUVTCIMYFANDJMRJEMYZLNZJDGVKOGNIG4WCPKZGTGV3XNBBCWSLOLBJFQSDQGA4TSQ3EKQ2TA6SWMJHTCTTHGFBFGZSLM5GECTLXGVEFE33QON5FUSCXOVMEKM2ZIRIXS2BWIRVDEVKKJUVXATZZLF2UUK3XI5UGYRBQJBEG632TLI2VIZBWPBSFI5DHJZCEWSDPJ5TFEULLNJ4W4N3MNE3W4TCBMJDUKTCSMMVWS2CKJBWE6M3CIYZE6V2FGNGUSU3JGU4UERCTMZFWG5LNKB2GG42KOVMUC2CGPI3EOSDLOVITKZDDMZQTKWKUMR3UEQ2LNZVU2UCKMNWHUNTPGYYXS53NG5TVGRKVKBMWGZKTOBGG4MKCGFZGY6COGJATATLPMVTTIOLMINKFA4KUOZLUY2LGONJHM5LWPE4XKRTIKI3UWYTNGNFHAR3RMJXEITRRPJ5EGRKJLFHEWSTMLBRDKSTZOBSTIWLIIRBGYVKNOFXGCSTVMRGTGVCNJVMWG2LHNNVW4VSONJWG4NTQGVUEGRKNI5WFK6LRORZWWNKVF5RU2ULYM54XCR2SKN2FKM2PNVRHA3SHJVFVCUKTK5KHC3JRPF5HIUJZO54EGR2EINYVUVSHGJKGGNTCOVDVSWLXLJDEISTQI5YWE3SEJYYXU6SDIVEVSTSLJJWFQYRVJJ4XAZJTMFHESVDIKE4XA3JYGNATM22TPB2DQ6CFN53UERCNLFIWQMCZO5XHG52CIRGVSULIGBMXO3TTO5BEITKZKFUDAWLXNZZXOQSEJVMVC2BQLF3W443XIJCE2WKRNAYFS53OON3UERCNLFIWQMCZO5XHG52CIRGVSULIGBMXO3TTO5BEITKZKFUDAWLXNZ2GSRCVJBNGORCMK5BWGZDQI5MHA332NBHTAVSXJNNFKM3DIR4WY2JXHBJHQRCUGE3WCMKKO5XGCS3WIVGXCZTVIJYFG6DEOVGTK2DQGY4HIS3LGVKDSQSXNFLVMTZTKEYG6WJLGNDWG53XHFSVO3CUMM2TMZ3SKJGEY3SMN5RFKTLCMFVGKY2ZMV3EYU3QOVMTQUKWONWGY2TMGFHDMQ2NORJHMUCNMZKGW4CVGNHGKWKLGJJWS6D2GZWTKQKHK5ZTG3TNKBXXSVLVMJWXMTKFMJNFMWJVORKGIZ2EJRLWE2T2JAYEUT2YJZVFQ3SDMRXXC43DPFYHK52GNRZE4MJUNJYUK3SMGIYXC6TIJ4YFMV2LLJKTGY2EPFWGSNZYKJ4EIVBRG5QTCSTXNZQUW5SFJVUWI3CZMQYU43TQIJKHSWCUJZWE2Z2QKJQXQSBWOA2WQQ2FJVDTCWRTKRXVU22TFNQUOSJZKVVGITLXPBUHSS2DGZRXU3ZQKV4USL2GJRCWK4KYOVDUSULXLJLEQZCPNAZFUSZVJFRWSMLJJYYXU6SDIVEVSUDRPJ2W4UKUJFXDQVKNKI3HATZULJUGUQTLKVHDANKILJXXA22SFNFVOSJPKVIGGTKRNBTXS4KPGZSEITLZLB4VC6CIOJVWE4DOI5GUWUKRLBMG4ZCHNFWVESBUN5MWUMKTHF3XQRCHIRFW6N3QO5HXUWSUJFCDAV3TKIVXCZKZKFUEIQTUK5SDANSHLJCXM3LINFIFMSJTMJIDEWBVMRIEKTZSI5XE23RRMQ4WKMKXHFZVET3BLBBE2SKSNJRWSYSYMY4DC6CZM5TVSULLOJHTKUDROZHVKNCNIFKU4SLZLJWGGL32LBEGSU2GM5BUG2ZVNMVXKLZVNJTXQQSBO5UEUV3EPEXWIY3DJI2GCQKJMFKGWVCLG4XW25KQIVCUIQ2FNRFHUSRZKY4XU3SCM5BWQ4CDKNGTO3RLME2DI6RRKJBW2RBYOJ4EQUCVNY2SW6LVGY2FGWSPHBAVC2DJPJEDSST2MRSFUMDXMN3WGWLXOBCGY3KKGZ5HKNRUKRNHKNCBKF4GS6KIJZHHUZDUMQYXO43XMRMUC2CENRWU4NT2OU3DMVDQNE2UC53YNB4UQSSNPI4WYZBRO5VXUZBUIFUEIRTNJ43FI3JXGZ5HA2BVM42HO2CDJBGE2VBRNZSDCMDOPJHHOQTINJBGWT3BMJXDOSZXOJUEU2ZXO5BEGR2MJVTDA3SOGEYW4VCCPJBDKNTTIY4EG2JPKZRGENKQOBKDMM3RGFITIVZRLBTTERZYIZ2HI2ZLORIHEULUIRBUCQSEFNFTEMTZMZLW4MLPKVUEESKBNAXUMYTCGVIHAVBWHBEVCQLTIFIWM4LUORRXMMTQMRLUKSKBK5AUS5RZKUZHKZRXKV2WUQ2FIFCEGRJTGJYWEWCIHFYVQUTIINAUE2SDMI3VMTTSNIVTCTDHO5UECQL2NB2DS33NGE2TSYLMHF3VC3CNJU4DIWCWOI2XGQSSNUYE4L3EK4ZHAYRXOZIEOOCSO5UU642ZOBUEUSDCKE3TSMLCK5WHM5JQFNRHQRCEJFQTK2TNIVXWG5CUNYYFMOLFK4VXEYRXOZCUKTLIG5UU6WKTOB4DCT3CKFMDCMLCGZ2HM5JYO5MXQSCPJE3GQ4LOIVKVU5CEMYZVM5DRK4VTO6TYOZCWGSLKOJDUWWKTKIZDATZPMRLTC4DCG52FA3JYKF3XSR3VLE2WQS2IJRKTKOKGMZMGY5TRGIVTO6CCIREWKNDKNVCXCY3EKRWTARRZMRLSW4TCG53E2R2NKJ5GST3PMFYHQRSHMJITGOJRMJQWY5TVHA4GE6CIINETM6DJNVCWWZDUIR3DGVTUMFLSWN2UGRSDI4LBKNSWOVDRFNUDANLVGJHXA5KVKV5EIT2FIJUG4RCXMNUXKNKSKRGU2NCRI5DWGTS2PFFTO3CGJV3XU2CBLFNHOMLOJFZHKVKVPJCE6RKCNBXEIV3DNF2TKUSUJVGTIUKHI5RU4WTZJM3WYRSNO55GQQKZLJ3TC3SJOJ2VKVL2IRHUKQTINZCFOY3JOU2VEVCNJU2FCR2HMNHFU6KLG5WEMTLXPJUECWK2O4YW4SLSOVKVO6TENNHFCTDNGN4WG2LUPJYXK5BTMFFHIYLGG5FG2M3GOF3GQU2HKU4WC3SNOFQTOZTPK4YXCL3DNVQWIZLVF5DG6WSRGFYWG6LQG5YCW2BXMFYDSU3EOIYXCMZPK5UGQQ2XLIXUW3SPOI3EQZDRNUYXAK3TK5RGMK3BGJCUSWSYGBYWGNTSOJSDE2LCK5XCW6K2OQZTM4RUKVUGYUCXOB5EW3LVGM3EM5DBOYZUU3LOLBZHM6DBI5KU4YLOJVYWKNTGN5STE4LGKVXGCOLBOQXTC32ZKFWG2ZTZOB5HCK3IGNQXA5DBMZZEM3JTF5WXI2CDI5LDSS3OJ5YTMM3EN5WTC4BPONWWEZBLOEVUMSLEIRXHOS3DNNSWKWKPJVAVINSIKBSVKSSNF5RUCWK2IFXCWT3FNN2VGWSPHBAVCNSIKBRVKNKJHBRXOY2ZIFXDET3FGBYVGWRLGRAVCNSEKBRVKOKKHBZXOZCZIFVDAT3FGRYFGWRWGVAXO6KCKBZWGOKKMNVXUZBUIFUDAT3FGRYHSURVGVTTI52CKBXWGOJVKFVXUOLXIJUGYRCVLJ5EY5LHFM3FS4BSOMZXQ5TGLJXFIUSWK5EFOZTZMJTU6ZLGKNUDGTSKNZSDSSSVLFSFMOKKOVGTMNKOI5EGG23VMYZVK3CUNBLFQM3NLF5HE22FMNTHS2JRHFSGSZCOIZLGEZC2PJFXKULYGU4UWTDGGAZFUMBQKZLGQMLOHBWTIRDONYYG6ZD2KNNDGZSTKZDUQVTGKNRGUT3VKRJGQM2KJRXDSMKKKU2FMVRZGVWU2NRVIJEEQODPORTFQWLOKRJFMVZTK5RXS4TLJVSWMU3JGM4U43LEJZDFMWLELIXUU5KBGU2TSS2IMMYHCY3KMFJXC4DHGNEWMWKOOJZDC3RLLBCSWNCFKEZWSULVOBCHKQJQPA3TGZTSOZRXGS3ELFAWOUCVNBTFGZSZIJYHEMLWF5MFKNRUIV3XU2CRMVYEG5LHHB3TOWCYOJ3DQ42KMQ2ES2CQIVUGIU2QMNBHA4RROUXVQYZVGRKTI53IIFSXAQZLNMVXOTCULBZGMODVJI4XOSTIOZAWOZCTJBSEENLKGJ2XMWDGGVMVCN3XKJAWK4CDGZVSW52EKRMHEZRLOU2XQ52KPBVEGZZZKNDGIQRZM4ZHK5SXMY2WGVBXNNJHCQ2MMM4HAV22JN2W45BQGFSWE3ZYGVYWGM2ZK5SDQSSTMFFVQRLTNNFU2MSSGUXVQNKPO52TOSKTNYYUK6KKLE2EKY3UKRXDM5SDLJXGIMSFNZIEWVTNKNUHOTBVJNVE4MDFMMYU6YTTJRHSWRLQJZLFA2KXINBEQYSZGQVXEODOLJMGIZ2KKQ3G2WSFONRUGT2XOB5DSSDMJZ5HKN2DKRXGQS32LJITIRTTNBJG2NSQKBQTGSRSIYZWEQ2VGJYW26CMIZAWU5DPMNTFMNSUOM3XK52FGU2VGTLZK5HUEWCMKU2XK2T2NVYHUZDILIZXO3CKN5YGGU3ZKFXXUWSINY4WM2ZTKA2FGQKJGREFC52DIFCHQZ2DIFEHUQKFIFCGOQJULFAUCQRYO5BECRBUM5BUKQLXIFRU2QKRIEVVSQLHIE4ECRSEIFEUCUBPO5AUM3ZQNBKVU4TIGFWUCQKBIFAUESSSKU2UK4TLJJTWOZZ5HU======再base32解密得到
iVBORw0KGgoAAAANSUhEUgAAAQQAAAEECAYAAADOCEoKAAAOWUlEQVR4nO2aS64ENwwD3/0v7WyCSW8GcE8okbKrAO8a+lASV/23AAD+5c9dAADkgCEAwAcMAQA+YAgA8AFDAIAPGAIAfMAQAOADhgAAH7YM4e/vj/d40gE059vNmaxZao/Jb1s3xK0TV6WtmumapfaY/LZ1Q9w6cVXaqpmuWWqPyW9bN8StE1elrZrpmqX2mPy2dUPcOnFV2qqZrllqj8lvWzfErRNXpa2a6Zql9pj8tnVD3DpxVdqqma5Zao/Jb1s3xK0TV6WtmumapfaY/LZ1Q9w6cVXaqpmuWWqPyW9bN8StE1elrZrpmqX2mPy2dVOKOx1lnw7NLAsUutzsLIbwv5m+kBjC+7qmgyEUMn0hMYT3dU0HQyhk+kJiCO/rmg6GUMj0hcQQ3tc1HQyhkOkLiSG8r2s6GEIh0xcSQ3hf13QwhEKmLySG8L6u6WAIhUxfSAzhfV3TGW8IqQt0Qp8OzVJx7Ub3DOR9didNFfaEPh2apeLaje4ZyPvsTpoq7Al9OjRLxbUb3TOQ99mdNFXYE/p0aJaKaze6ZyDvsztpqrAn9OnQLBXXbnTPQN5nd9JUYU/o06FZKq7d6J6BvM/upKnCntCnQ7NUXLvRPQN5n91JU4U9oU+HZqm4dqN7BvI+u5OmCntCnw7NUnHtRvcM5H12J00V9oQ+HZql4tqN7hnI++xOmiqsuk91ztRFc2imrF8dL3VO2312J00VVt2nOmfqojk0U9avjpc6p+0+u5OmCqvuU50zddEcminrV8dLndN2n91JU4VV96nOmbpoDs2U9avjpc5pu8/upKnCqvtU50xdNIdmyvrV8VLntN1nd9JUYdV9qnOmLppDM2X96nipc9rusztpqrDqPtU5UxfNoZmyfnW81Dlt99mdNFVYdZ/qnKmL5tBMWb86XuqctvvsTpoqrLpPdc7URXNopqxfHS91Ttt9didNFVbdpzpn6qI5NFPWr46XOqftPruTpgrr6vMWxh9K6N5iCBjCSMYfSujeYggYwkjGH0ro3mIIGMJIxh9K6N5iCBjCSMYfSujeYggYwkjGH0ro3mIIGMJIxh9K6N5iCBjCSMYfSujeYggYwkjGH0ro3o43hGQcg0o1NDXddSVroQRDKARDqANDqAFDKARDqANDqAFDKARDqANDqAFDKARDqANDqAFDKARDqANDqAFDKARDqANDqAFDKARDqANDqAFDKARDqANDqAFDKARDqANDqCHaEG553YNyGIcyVrJmt7zteSJujbipsXbjKWMla3bL254n4taImxprN54yVrJmt7zteSJujbipsXbjKWMla3bL254n4taImxprN54yVrJmt7zteSJujbipsXbjKWMla3bL254n4taImxprN54yVrJmt7zteSJujbipsXbjKWMla3bL254n4taImxprN54yVrJmt7zteSJujbipsXbjKWMla3bL257n9pfwCscwlbU5+nTpAf+BukUkHwCGAN9A3SKSDwBDgG+gbhHJB4AhwDdQt4jkA8AQ4BuoW0TyAWAI8A3ULSL5ADAE+AbqFpF8ABgCfAN1i0g+AAwBvtH+p+J2YYblSF1al7bdejhiJe92956thSHY+1TW5ehTWZsjVvJud+/ZWhiCvU9lXY4+lbU5YiXvdveerYUh2PtU1uXoU1mbI1bybnfv2VoYgr1PZV2OPpW1OWIl73b3nq2FIdj7VNbl6FNZmyNW8m5379laGIK9T2Vdjj6VtTliJe92956thSHY+1TW5ehTWZsjVvJud+/ZWhiCvU9lXY4+lbU5YiXvdveerYUh2PtU1uXoU1mbI1bybnfv2VpiQ1DGihYt9FBcenT30J1PnTNVs7UwhJ9IXTSXHt09dOdT50zVbC0M4SdSF82lR3cP3fnUOVM1WwtD+InURXPp0d1Ddz51zlTN1sIQfiJ10Vx6dPfQnU+dM1WztTCEn0hdNJce3T1051PnTNVsLQzhJ1IXzaVHdw/d+dQ5UzVbC0P4idRFc+nR3UN3PnXOVM3WwhB+InXRXHp099CdT50zVbO1Ng1BSfKgLAMw5HRopszZHWuXE3YDQyh6Dj2UJM+pO9YuJ+wGhlD0HHooSZ5Td6xdTtgNDKHoOfRQkjyn7li7nLAbGELRc+ihJHlO3bF2OWE3MISi59BDSfKcumPtcsJuYAhFz6GHkuQ5dcfa5YTdwBCKnkMPJclz6o61ywm7gSEUPYceSpLn1B1rlxN2A0Moeg49lCTPqTvWLifsRvuvy9uFhR7Kbm3JpGqbnDN1zzCEIYNKJlXb5Jype4YhDBlUMqnaJudM3TMMYcigkknVNjln6p5hCEMGlUyqtsk5U/cMQxgyqGRStU3OmbpnGMKQQSWTqm1yztQ9wxCGDCqZVG2Tc6buGYYwZFDJpGqbnDN1zzCEIYNKJlXb5Jype3aNIThQ9pm83A6kSxt8xEowBDMYQh0YwnswBDMYQh0YwnswBDMYQh0YwnswBDMYQh0YwnswBDMYQh0YwnswBDMYQh0YwnswBDMYQh0YwnswBDMYQh0YwntiDUHZgDLWCcdpGXpozhO0VWKZU3cDyli78RxDT17a1JwnaKvEMqfuBpSxduM5hp68tKk5T9BWiWVO3Q0oY+3Gcww9eWlTc56grRLLnLobUMbajecYevLSpuY8QVslljl1N6CMtRvPMfTkpU3NeYK2Sixz6m5AGWs3nmPoyUubmvMEbZVY5tTdgDLWbjzH0JOXNjXnCdoqscypuwFlrN14jqEnL21qzhO0VWKZU3cDyli78RxDT17a1JwnaKvEMidlYd1NnpBTyXTNlMgPRaxH6p5hCEMG1Z3ToZkS+aGI9UjdMwxhyKC6czo0UyI/FLEeqXuGIQwZVHdOh2ZK5Ici1iN1zzCEIYPqzunQTIn8UMR6pO4ZhjBkUN05HZopkR+KWI/UPcMQhgyqO6dDMyXyQxHrkbpnGMKQQXXndGimRH4oYj1S9wxDGDKo7pwOzZTID0WsR+qeYQhDBtWd06GZEvmhiPVI3bP2X5dPEO2GnMn1d9e1W9sROaXBMIRjcibXf81xYggYQkrO5PqvOU4MAUNIyZlc/zXHiSFgCCk5k+u/5jgxBAwhJWdy/dccJ4aAIaTkTK7/muPEEDCElJzJ9V9znBgChpCSM7n+a44z1RCmD8rxHPUn5+yu64SZO8AQhizH9JzddZ0wcwcYwpDlmJ6zu64TZu4AQxiyHNNzdtd1wswdYAhDlmN6zu66Tpi5AwxhyHJMz9ld1wkzd4AhDFmO6Tm76zph5g4whCHLMT1nd10nzNwBhjBkOabn7K7rhJk7wBCGLMf0nN11nTBzB56sF8Ci/Vbb5PpT63q1Q4W1Xg2G8Fttk+tPrQtDCABD+K22yfWn1oUhBIAh/Fbb5PpT68IQAsAQfqttcv2pdWEIAWAIv9U2uf7UujCEADCE32qbXH9qXRhCABjCb7VNrj+1LgwhAAzht9om159al9wQlMM84XVr5sBRm0N/dW2pb7vPG8RwiOsYphJHbQ791bWlvu0+bxDDIa5jmEoctTn0V9eW+rb7vEEMh7iOYSpx1ObQX11b6tvu8wYxHOI6hqnEUZtDf3VtqW+7zxvEcIjrGKYSR20O/dW1pb7tPm8QwyGuY5hKHLU59FfXlvq2+7xBDIe4jmEqcdTm0F9dW+rb7vMGMRziOoapxFGbQ391balvu88bxHCI6ximEkdtDv3VtaW+7T4d4qaSegTq+h05u2OpuUUzDOEBhnDWciu5RTMM4QGGcNZyK7lFMwzhAYZw1nIruUUzDOEBhnDWciu5RTMM4QGGcNZyK7lFMwzhAYZw1nIruUUzDOEBhnDWciu5RTMM4QGGcNZyK7lFMwzhAYZw1nIruUWzdkNQLm3ycitzqut3aJtaf7Jm3fqvhSGU9anMqa7foW1q/cmadeu/FoZQ1qcyp7p+h7ap9Sdr1q3/WhhCWZ/KnOr6Hdqm1p+sWbf+a2EIZX0qc6rrd2ibWn+yZt36r4UhlPWpzKmu36Ftav3JmnXrvxaGUNanMqe6foe2qfUna9at/1oYQlmfypzq+h3aptafrFm3/mthCGV9KnOq63dom1p/smbd+q+FIdDnwKckeeYOMAT6HPeUJM/cAYZAn+OekuSZO8AQ6HPcU5I8cwcYAn2Oe0qSZ+4AQ6DPcU9J8swdYAj0Oe4pSZ65AwyBPsc9Jckzd4Ah0Oe4pyR55g4wBPoc95Qkz9wBhlDUZzLug+6Yp2s3xvfZnTRVWHWfybgOefSh3NJnd9JUYdV9JuM65NGHckuf3UlThVX3mYzrkEcfyi19didNFVbdZzKuQx59KLf02Z00VVh1n8m4Dnn0odzSZ3fSVGHVfSbjOuTRh3JLn91JU4VV95mM65BHH8otfXYnTRVW3WcyrkMefSi39NmdNFVYdZ/JuA559KHc0qcjaSqpg3IfYNrr1n+XE+4EQ3iQupDuA0x73frvcsKdYAgPUhfSfYBpr1v/XU64EwzhQepCug8w7XXrv8sJd4IhPEhdSPcBpr1u/Xc54U4whAepC+k+wLTXrf8uJ9wJhvAgdSHdB5j2uvXf5YQ7wRAepC6k+wDTXrf+u5xwJxjCg9SFdB9g2uvWf5cT7kRqCLc8pWZKunt01ebo85qc3YWd8JSaKXEskKM2R5/X5Owu7ISn1EyJY4EctTn6vCZnd2EnPKVmShwL5KjN0ec1ObsLO+EpNVPiWCBHbY4+r8nZXdgJT6mZEscCOWpz9HlNzu7CTnhKzZQ4FshRm6PPa3J2F3bCU2qmxLFAjtocfV6Ts7uwE55SMyWOBXLU5ujzmpzdhZ3wlJopcSyQozZHn9fk3P4SAI4HQwCADxgCAHzAEADgA4YAAB8wBAD4gCEAwAcMAQA+YAgA8AFDAIAP/wAFo0hUZrh1mAAAAABJRU5ErkJggg==一看结尾==,应该是base64编码,于是继续解密。
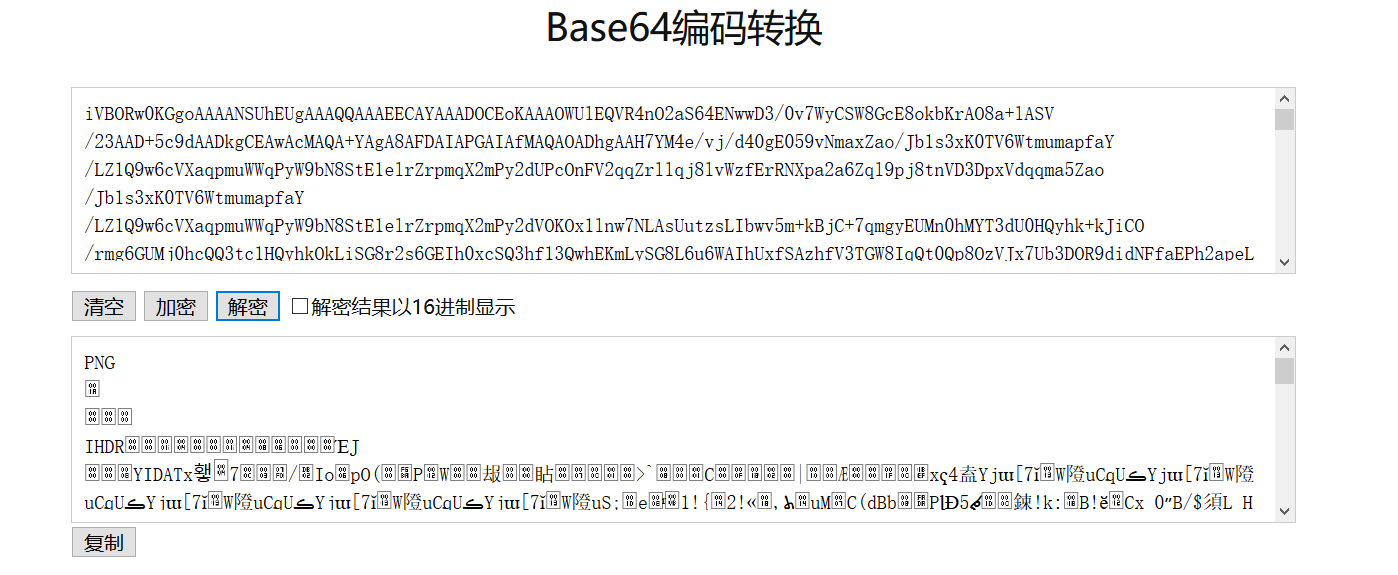
噫是个PNG图片。加上头补全 data:image/png;base64,。草(一种植物),真会玩,是个二维码。
(也可以base64解密后保存为二进制文件然后打开。

扫码得到flag:
hgame{3Nc0dInG_@lL_iN_0Ne!}
真的会玩2333((好,我也要整一个各种编码的嘻嘻嘻
Reference:
https://www.qqxiuzi.cn/bianma/kaisamima.php
https://www.splitbrain.org/services/ook
每日推荐
得到一个.pcapng抓包文件,用Wireshark打开,查看http,发现应该是与wordpress博客相关。
利用“文件-导出对象-HTTP”,分析其中的对象。
结合题目提示
ObjectNotFound正听着网易云每日推荐…
发现了一个上传的网页——
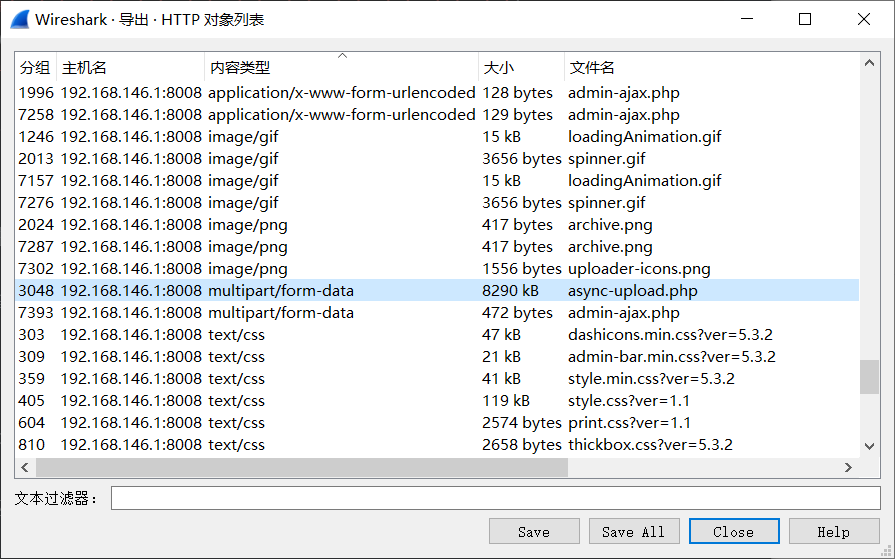
这是一个提交的表格,发现了上传的文件 song.zip,将其提取出来。
压缩包里果然是一首歌,且备注里提示是6位数字。
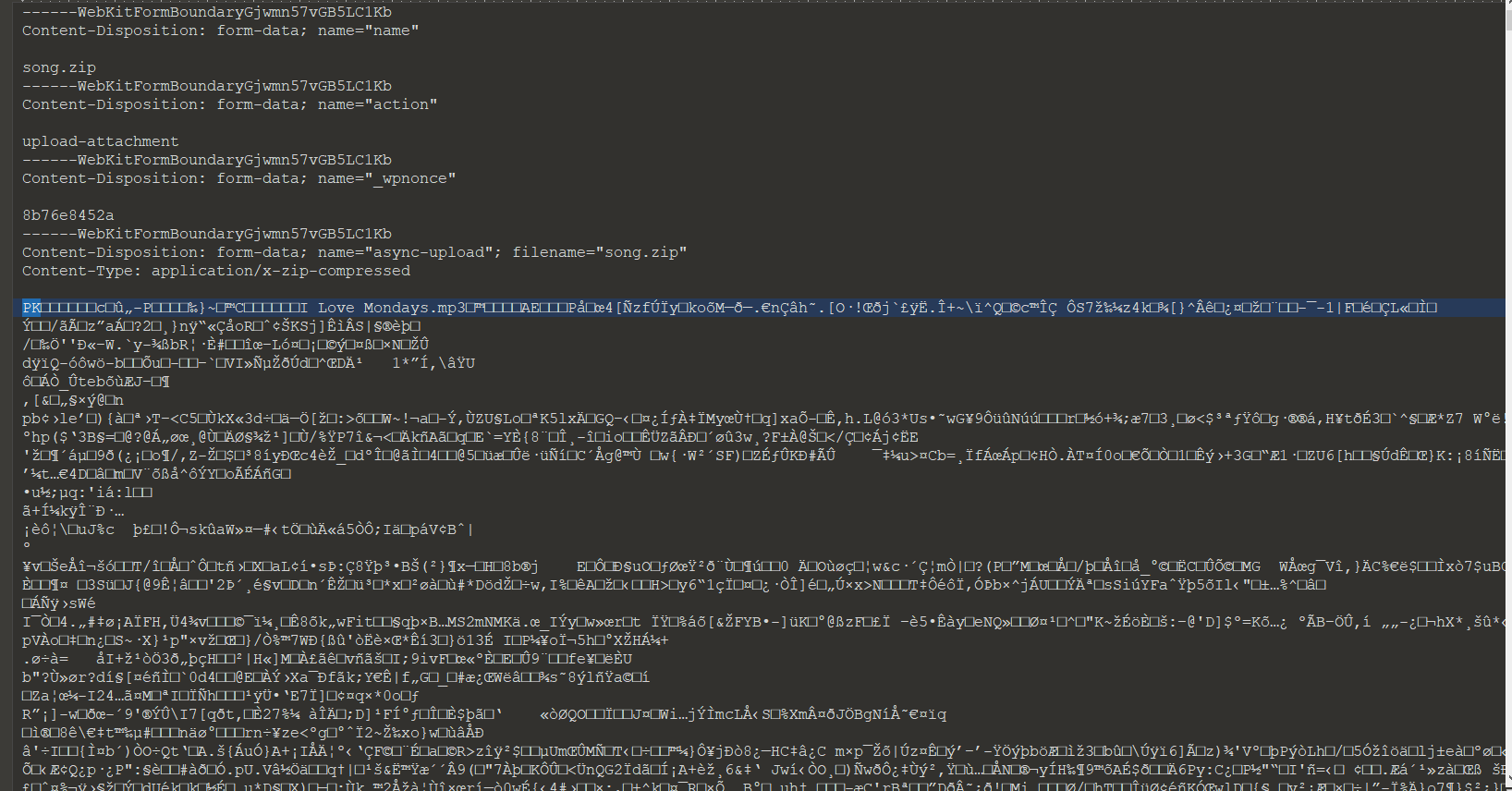
考虑到6位数字,直接就暴力破解好了。(其实还在抓包文件里找了老半天没找到(((
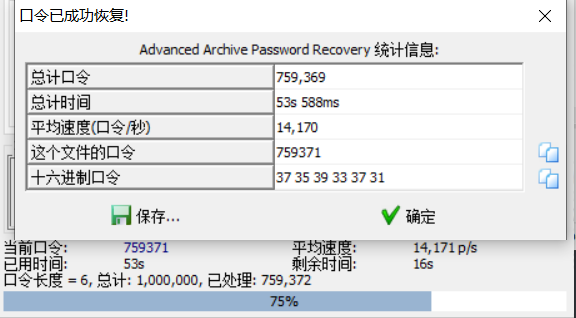
利用口令759371解压得到mp3文件。
一开始打开010editor找,没有。
foremost提取得到了封面图,也没有隐写。
看来在音频里了,猜想就是音频隐写嘛。
既然是MP3,先试试MP3StegoDecode,结果么得。
the bit stream file I Love Mondays.mp3 is a BINARY file
HDR: s=FFF, id=1, l=1, ep=on, br=4, sf=3, pd=0, pr=0, m=0, js=0, c=0, o=0, e=0
alg.=MPEG-1, layer=I, tot bitrate=128, sfrq=0.0
mode=stereo, sblim=32, jsbd=32, ch=2
[Frame 3]OpenTable: could not find tables/huffdec
Check local directory './tables/'
Please check huffman table 'huffdec'上网找了一下,下了个音频处理软件Audacity。(免费开源跨平台,还不错
Free, open source, cross-platform audio software. Audacity is an easy-to-use, multi-track audio editor and recorder for Windows, Mac OS X, GNU/Linux…
查看频谱,得到flag:
hgame{I_love_EDM233}
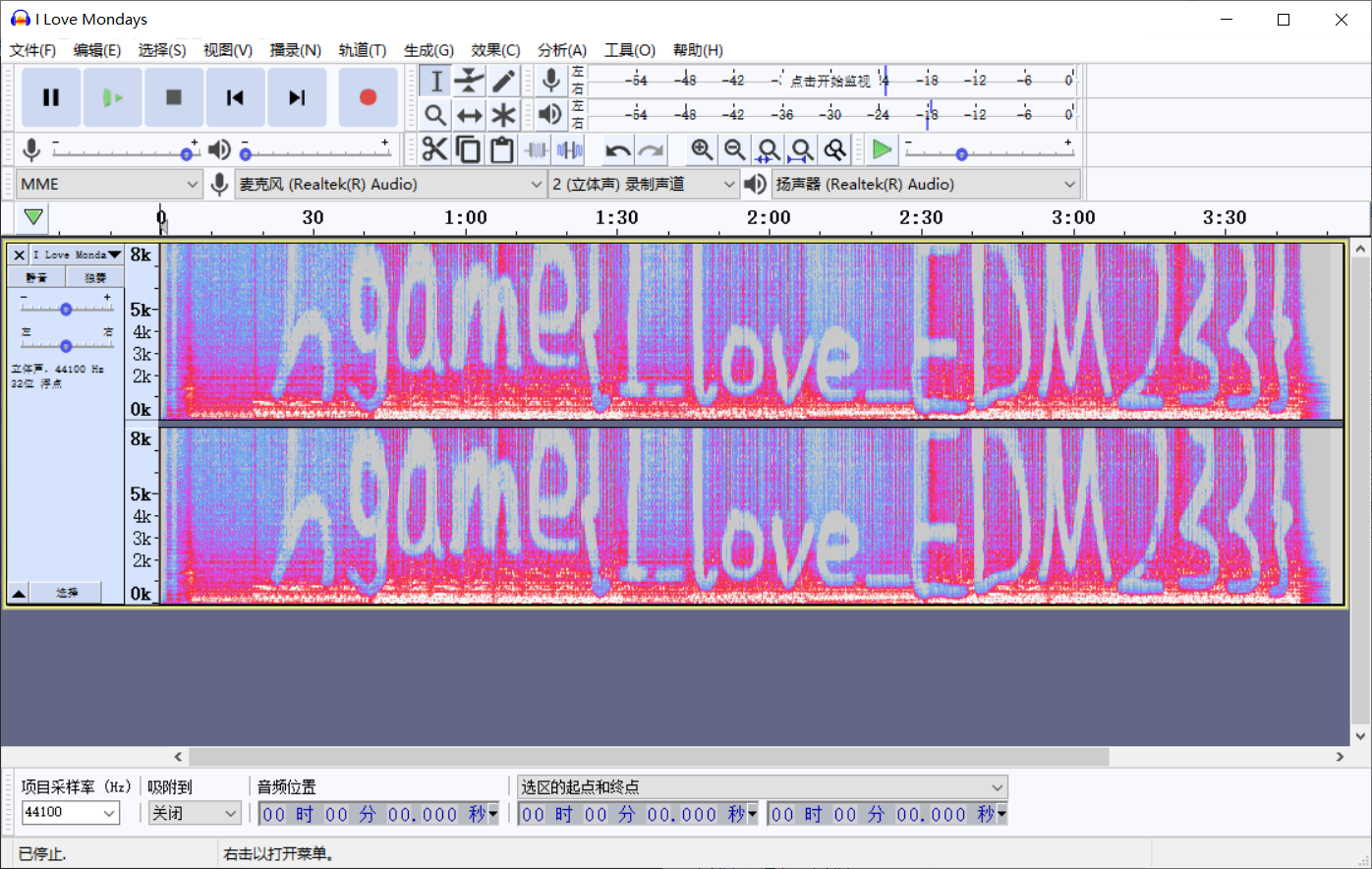
Electronic Dance Music (电子舞曲)可还行。
第一次做音频隐写的题,哇脑洞真大,太有意思了233333
Web
Cosmos 的博客
先在网页里找了半天没找到emmm
后来发现,既然说版本管理工具,还有GitHub嘛。
那就构造/.git/config试试
果然——
[core]
repositoryformatversion = 0
filemode = true
bare = false
logallrefupdates = true
[remote "origin"]
url = https://github.com/FeYcYodhrPDJSru/8LTUKCL83VLhXbc
fetch = +refs/heads/*:refs/remotes/origin/*好,这个GitHub仓库有戏!
访问一波,然后在commit里找到了flag。
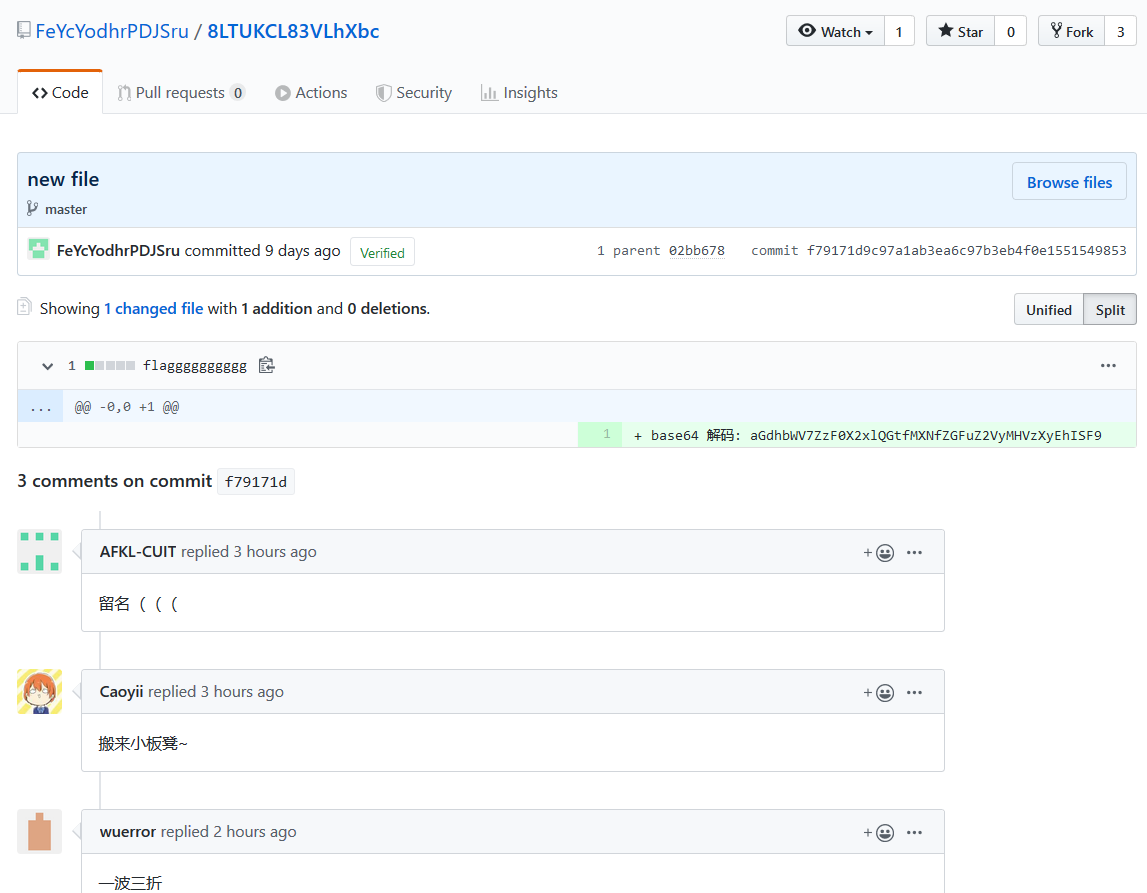
base64解码得到flag
hgame{g1t_le@k_1s_danger0us_!!!!}
/.git目录公开访问是挺危险的emmm
接 头 霸 王
直接访问,提示
You need to come from https://vidar.club/.
增加请求头: Referer: https://vidar.club/,重发后提示
You need to visit it locally.
增加请求头:X-Forwarded-For: 127.0.0.1
You need to use Cosmos Brower to visit.
改UA:User-Agent: Cosmos
The flag will be updated after 2077, please wait for it patiently.
根据响应头 Last-Modified: Fri, 01 Jan 2077 00:00:00 GMT,进行修改。把 If-Unmodified-Since 设置在 Last-Modified 之后就可以了。
增加请求头:If-Unmodified-Since: Fri, 01 Jan 2077 00:00:00 GMT
得到flag
hgame{W0w!Your_heads_@re_s0_many!}
这题一波三折啊。
最后这个操作让我想到了ustc的hackgame里
信息安全 2077那道题,然后回去看了一下233.Reference:
🐔尼泰玫
cxk有点好玩2333
随便玩了一下觉得有点无聊(x
看了一下网页源代码,发现是用canvas画布画出来的,交互用的js,有点意思i。
然后打开了Burp Suite,抓个包看看吧。
发现游戏结束的时候会POST当前得分。
不够则提示
Your score must more than 30000 , then you can get the flag. Happy game!
那就截包改包好了啦,直接给他加个0.
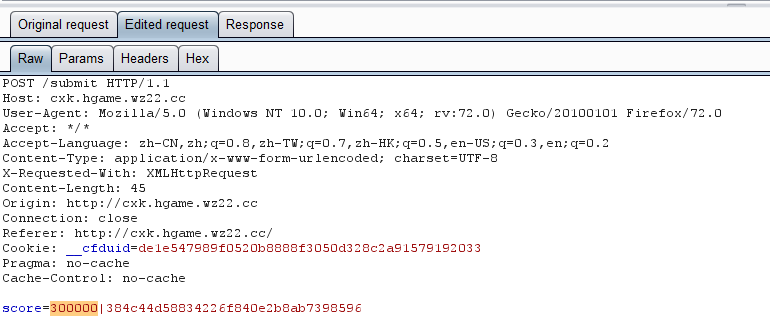
这就出来了呀!
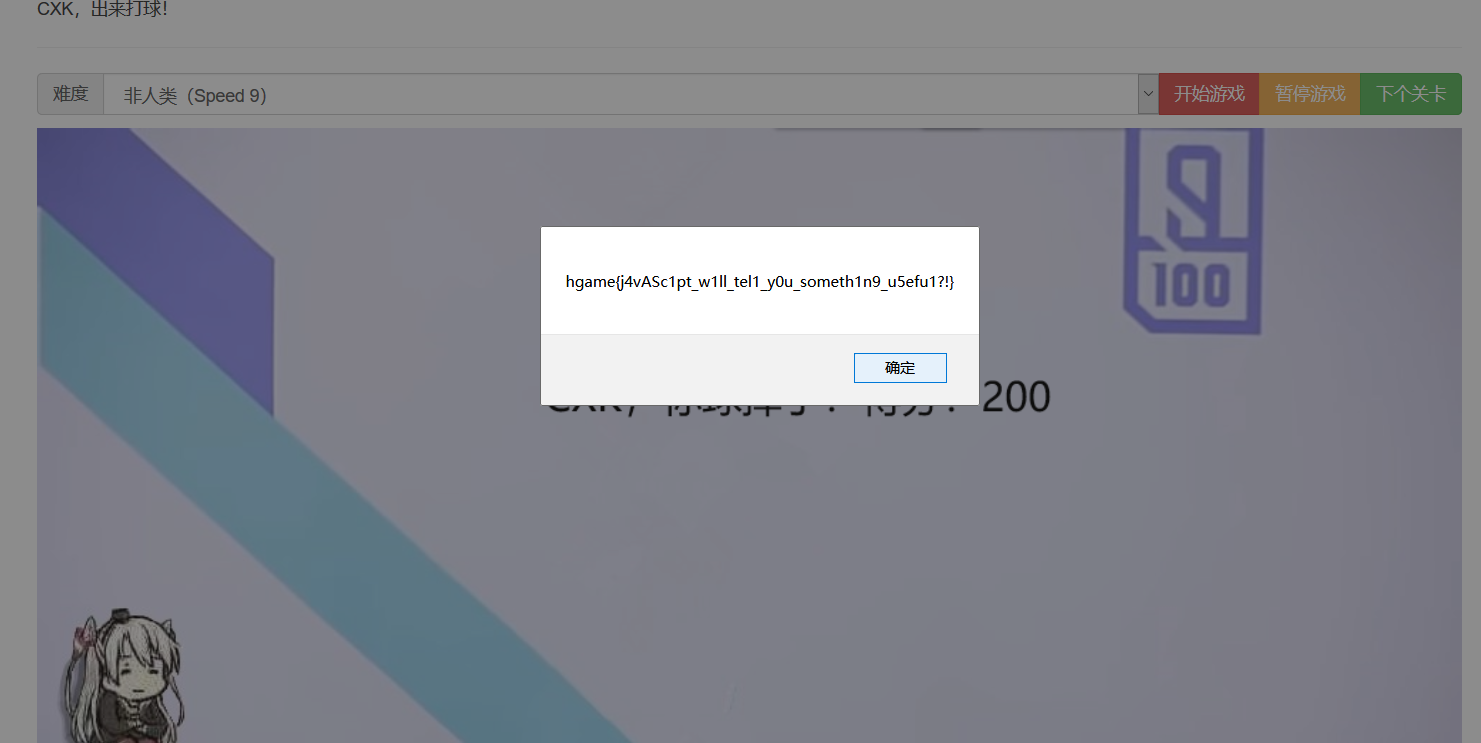
hgame{j4vASc1pt_w1ll_tel1_y0u_someth1n9_u5efu1?!}
Code World
http://codeworld.hgame.day-day.work/
发现重定向到了 http://codeworld.hgame.day-day.work/new.php
同时看到了一句js
console.log("This new site is building....But our stupid developer Cosmos did 302 jump to this page..F**k!")curl看了一下之前的网页405。
嘤不会了。。
20200125更新:
看了官方WP,发现要把请求改成POST发到原页面。
于是试了一下,返回
人鸡验证 目前它只支持通过url提交参数来计算两个数的相加,参数为a 现在,需要让结果为10再构造参数a,根据提示
参数a的提交格式为: 两数相加(a=b+c),考虑到+的Urlencode为%2b于是构造
/?a=2%2b8,得到flagThe result is: 10 hgame{C0d3_1s_s0_S@_sO_C0ol!}
Crypto
InfantRSA
题目给了如下的代码——
#!/usr/bin/env python3
from secret import flag
assert flag.startswith(b'hgame{') and flag.endswith(b'}')
m = int.from_bytes(flag, byteorder='big')
p = 681782737450022065655472455411
q = 675274897132088253519831953441
e = 13
c = pow(m, e, p*q)
assert c == 275698465082361070145173688411496311542172902608559859019841RSA啦。这里就根据密文C把明文M给找出来。
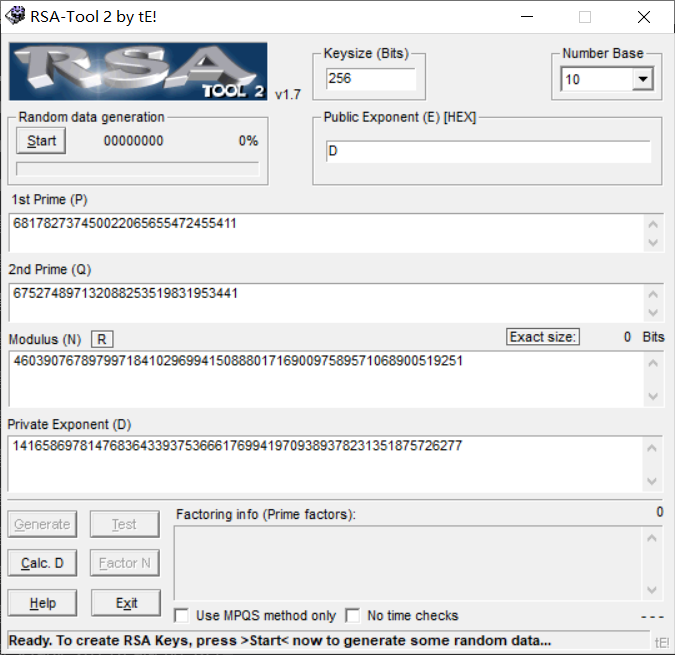
c = 275698465082361070145173688411496311542172902608559859019841
n = 460390767897997184102969941508880171690097589571068900519251
d = 141658697814768364339375366617699419709389378231351875726277
m = pow(c,d,n)
# 得到m为39062110472669388914389428064087335236334831991333245
# 再将数字m转换为字符串
import binascii
flag = binascii.unhexlify(hex(m)[2:])或者 用上面的工具里的Test:
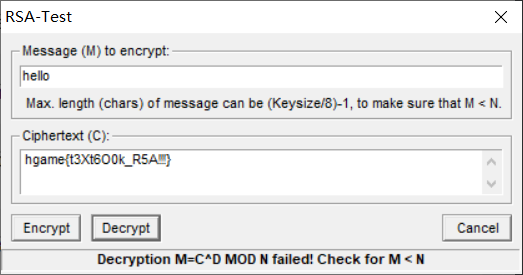
得到flag:
hgame{t3Xt6O0k_R5A!!!}
Reference: 介绍RSA的
https://www.freebuf.com/articles/others-articles/166049.html
https://www.freebuf.com/articles/others-articles/161475.html
https://www.k2zone.cn/?p=2157
Reorder
nc 47.98.192.231 25002
敲个回车就可以得到一个乱序的字符串,刚开始还以为是分组来着,然后试了半天不对emmm。
后来才发现,原来每次的结果都不一样233,比如下面是一些实验结果。
Rua!!!
$hLjgp+ame{UI5mtA3}u_!iP!RmTn0eT
Rua!!!
$mtgIUeapjm{h+5LAeT_nTRP!u!m3i0}
Rua!!!
t5m{ag+eh$UjILmpT0!mP_iR3ATun}e!
$mhmjI5te+{apUgLAe3!un0TRimP!T_}
mat5jIpmg$heLU{+!PT0un!e_A3R}Tmi
{LUpt5mI+e$mgajhm}T!T0!niRAe_Pu3
$Umm+g{LIe5jphtaAT!ei_m}nR0u!3TP
5I{eLmt+ha$mgpjU0nmR}eTi3PA!_!uT
Lm$jham{pUt+5Ige}!Au3Pem!TTi0n_R既然是乱序吧,那就看看到底是什么个顺序好了!
上面字符串的长度为32,于是构造字符串
str1='123456abcdefghijklmnopqrstuvwxyz'
输入后得到 str2='jhca1346ibdefg25zxsqkmnpyrtuvwlo'
试了发现该顺序不变,于是得到编码的对应关系(正变换逆变换嘛233333)
str1='123456abcdefghijklmnopqrstuvwxyz'
print(len(str1))
str2='jhca1346ibdefg25zxsqkmnpyrtuvwlo'
# 正变换
location=list(range(len(str1)))
for i in range(len(str2)):
location[i]=str1.index(str2[i])
print(location)
# [15, 13, 8, 6, 0, 2, 3, 5, 14, 7, 9, 10, 11, 12, 1, 4, 31, 29, 24, 22, 16, 18, 19, 21, 30, 23, 25, 26, 27, 28, 17, 20]
# 逆变换
ilocation=list(range(len(str1)))
for i in range(len(str2)):
ilocation[i]=str2.index(str1[i])
print(ilocation)
# [4, 14, 5, 6, 15, 7, 3, 9, 2, 10, 11, 12, 13, 1, 8, 0, 20, 30, 21, 22, 31, 23, 19, 25, 18, 26, 27, 28, 29, 17, 24, 16]
# 验证结果
str3=''
for i in location:
str3+=str1[i]
print(str3)
# jhca1346ibdefg25zxsqkmnpyrtuvwlo这里用到的是正变换,暴力破解一波吧!
str_encrypted = r'Lm$jham{pUt+5Ige}!Au3Pem!TTi0n_R'
str_decrypted = ''
for _ in range(80):
for i in location:
str_decrypted += str_encrypted[i]
print(str_decrypted)
str_encrypted = str_decrypted
str_decrypted = ''最开始试了50次没出来233,后来把数字改大了一点233.
终于跑出来了!
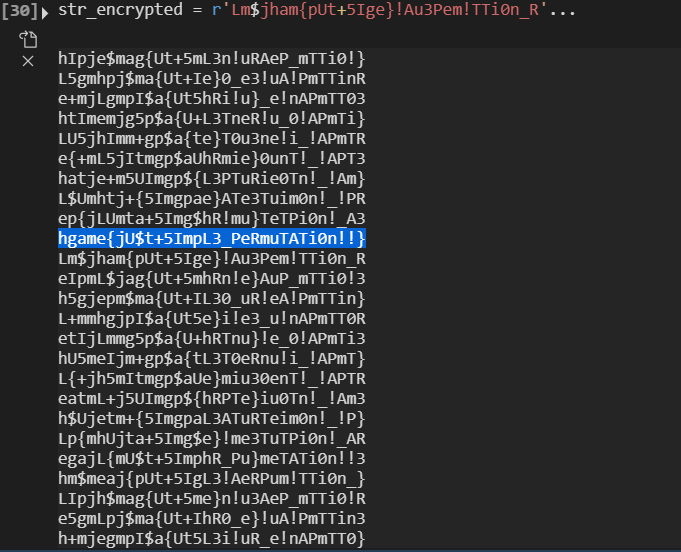
得到flag:
hgame{jU$t+5ImpL3_PeRmuTATi0n!!}
果然就排列呗23333
还试了一下,这个130次一循环来着emmm。就这样,发现range改到131就出现两个了。
str_encrypted = r'Lm$jham{pUt+5Ige}!Au3Pem!TTi0n_R'
str_decrypted = ''
for _ in range(130):
for i in location:
str_decrypted += str_encrypted[i]
if str_decrypted.startswith('hgame'):
print(str_decrypted)
str_encrypted = str_decrypted
str_decrypted = ''不对唉!好像没这么简单。重新试了一下之前的几个Rua!!!之后的结果,发现这个变换不可行emmm。
必须是连续输入上一次出来的结果才行。(可能理解有误
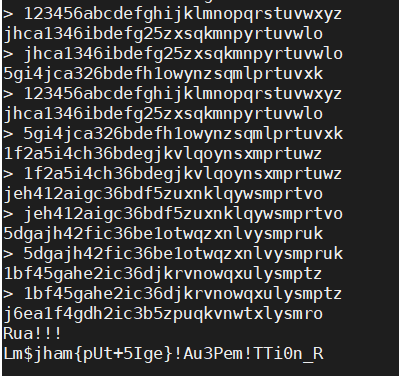
Affine
题目给了这段用来加密的代码,现在就想办法还原回去找flag吧。
#!/usr/bin/env python3
# -*- coding: utf-8 -*-
import gmpy2
from secret import A, B, flag
assert flag.startswith('hgame{') and flag.endswith('}')
TABLE = 'zxcvbnmasdfghjklqwertyuiop1234567890QWERTYUIOPASDFGHJKLZXCVBNM'
MOD = len(TABLE)
cipher = ''
for b in flag:
i = TABLE.find(b)
if i == -1:
cipher += b
else:
ii = (A*i + B) % MOD
cipher += TABLE[ii]
print(cipher)
# A8I5z{xr1A_J7ha_vG_TpH410}提示了flag以 hgame{ 开头,以 } 结尾,很明显能看出来{ } _这三个字符是找不到而直接加到cipher里的。
容易得到 MOD=62,于是乎思路就是,利用 hgame 与 A8I5z 的映射关系,把A和B两个参数给求解出来,再把参数i反解出来,最后把flag还原。
码代码吧。
TABLE = 'zxcvbnmasdfghjklqwertyuiop1234567890QWERTYUIOPASDFGHJKLZXCVBNM'
MOD = len(TABLE) # 62
flag = 'hgame'
cipher = ''
for b in flag:
i = TABLE.find(b)
print(b, i)
# 求解得到对应的i
# h 12
# g 11
# a 7
# m 6
# e 18
str_encrypt = r'A8I5z{xr1A_J7ha_vG_TpH410}'
iis = list(range(5))
i = 0
for letter in str_encrypt[0:5]:
iis[i] = TABLE.index(letter)
print(letter, iis[i])
i += 1
# 求解得到对应的ii
# A 46
# 8 33
# I 43
# 5 30
# z 0得到了字母对应的i和ii,而**i与ii满足关系 (A*i+B) % 62 = ii**,从而可以把A、B解出来。
查了查模逆运算,看了看觉得有点麻烦emmm
猜想A、B不会太大,干脆直接遍历好了。。
for A in range(1, 62):
for B in range(1, 62):
if (12*A+B) % 62 == 46 and (11*A+B) % 62 == 33 and (7*A+B) % 62 == 43 and(6*A+B) % 62 == 30 and(18*A+B) % 62 == 0:
print("Yes: ", A, B)
# Yes: 13 14得到A=13,B=14.
接下来还原flag。
# Begin to decrypt...
A = 13
B = 14
str_encrypt = 'xr1AJ7havGTpH410'
str_decrypt = ''
for letter in str_encrypt:
ii = TABLE.index(letter)
for i in range(62):
temp = (A*i + B) % 62
if temp == ii:
print(i, TABLE[i])
str_decrypt += TABLE[i]
print(str_decrypt)
# M4thu5EdiNcRYpt0
# So the flag is `hgame{M4th_u5Ed_iN_cRYpt0}`.这里先把_给去掉了,最后再加上。
于是乎flag就是:
hgame{M4th_u5Ed_iN_cRYpt0}
看来果然是数学啊2333,还想看看大佬们怎么用数学方法解出来的。((
如题目所言——
Some basic modular arithmetic…
Reference: 一点关于模逆运算的介绍,后面有空再看看吧(x
Pwn
Hard_AAAAA
nc 47.103.214.163 20000
IDA分析一波,发现是memcmp比较,backdoor函数里是执行/bin/sh的。
其中s与v5距离为 -31h-(-ACh)=123,构造payload发了个"0O0o"过去,发现么得。
int __cdecl main(int argc, const char **argv, const char **envp)
{
char s; // [esp+0h] [ebp-ACh]
char v5; // [esp+7Bh] [ebp-31h]
unsigned int v6; // [esp+A0h] [ebp-Ch]
int *v7; // [esp+A4h] [ebp-8h]
v7 = &argc;
v6 = __readgsdword(0x14u);
alarm(8u);
setbuf(_bss_start, 0);
memset(&s, 0, 0xA0u);
puts("Let's 0O0o\\0O0!");
gets(&s);
if ( !memcmp("0O0o", &v5, 7u) )
backdoor();
return 0;
}20200125更新:
看了官方WP,草(一种植物),好气啊,\x00把字符串识别隔断了。
未完待续
(可能会咕咕咕


